Through these automated scripts and software, compromised credentials found in breaches are cross checked to see if these credentials (username and password) are able to log into certain websites.
This technique allows attackers to identify potential victims, which they can later target with more specific attacks like phishing, social engineering, or account takeover. Figure 1 shows the account checking process overview.
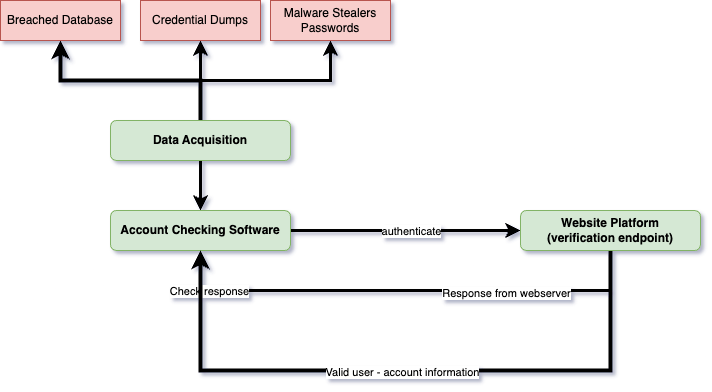
Coinbase Account Checking Overview
In recent Coinbase account checking campaigns, cybercriminals exploit Coinbase’s “send money/crypto by phone or email” feature to identify active accounts. By using this method, they can determine if an email address is associated with a Coinbase account, allowing them to target verified users for further attacks. Figure 2 shows an example of the email received from Coinbase in this type of attack.
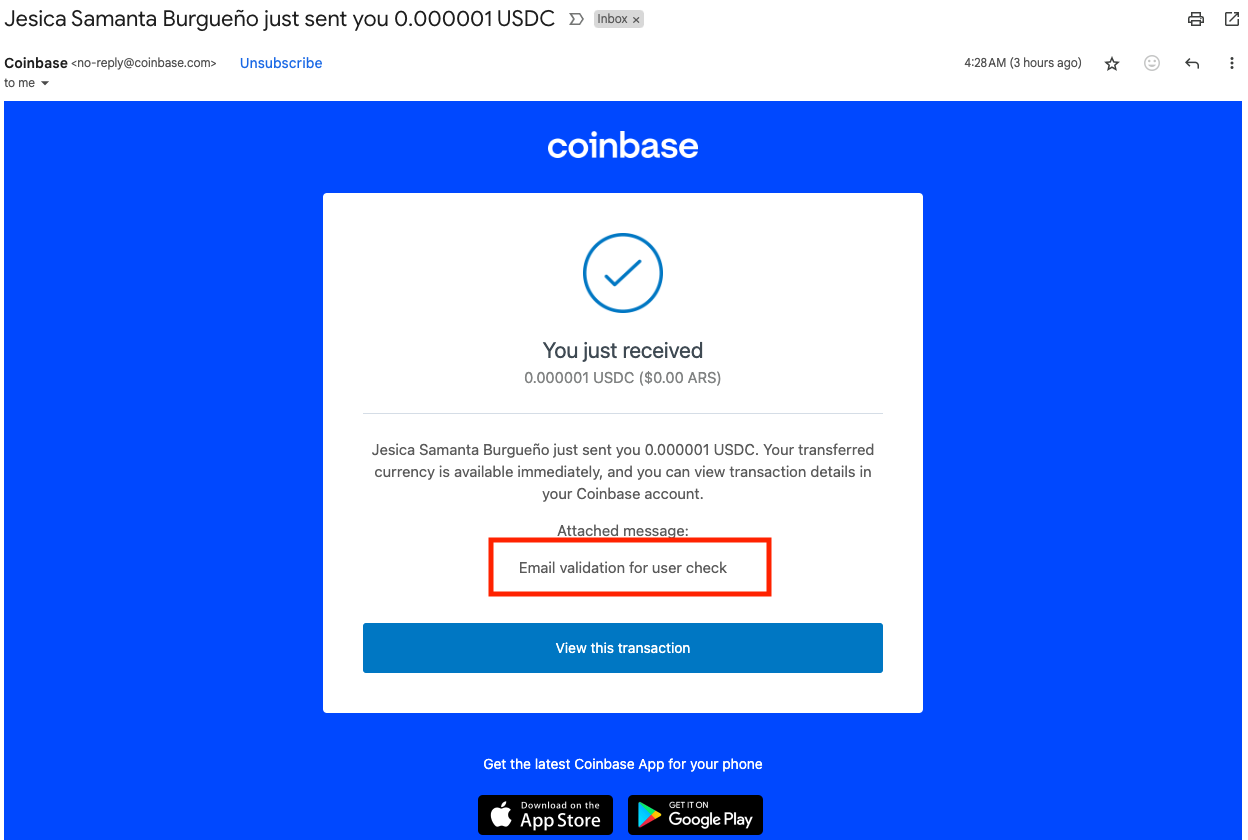
As shown in the email above, the sender, named “Jessica Burgueno,” sent us 0.000001 USDC using Coinbase’s “send money” feature. Since we have an account on Coinbase, the transfer status appears as “successful,” informing the cybercriminal that our email is linked to a valid Coinbase account. This confirmation signals that our email address can be targeted in follow-up attacks, such as phishing campaigns or social engineering using OTP bots. Figure 3 shows an example of successful transfer in Coinbase.
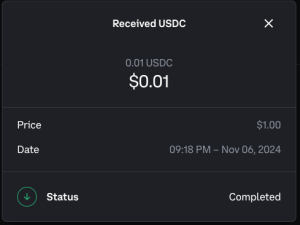
For an email address that is not registered with Coinbase, the transfer would be marked as “unsuccessful.” This response signals to the cybercriminal that the email is not linked to a Coinbase account, allowing them to disregard it and focus on other potential targets.
Key Takeaways
If you have a Coinbase account, you could be at risk from this type of attack. If you don’t have a Coinbase account, there’s no immediate concern. However, this method can be used on other platforms as well.
If you receive this kind of email and have a Coinbase account, the cybercriminal will be able to confirm your account exists, making you vulnerable to follow-up phishing and social engineering attacks.
How to Protect Yourself
Enable 2FA: Use two-factor authentication (2FA) to secure your account.
Monitor for Suspicious Activity: Regularly check for unusual emails or login alerts.
Avoid Publicly Sharing Email/Phone Numbers: This limits the data attackers can use for account checking.