OTP, or One-Time Password, is a popular method used for two-factor authentication (2FA) to enhance account security. It typically involves receiving a unique code via SMS or email, which is required alongside the password for login verification. However, cybercriminals have found ways to bypass this security measure using OTP bots.
These OTP bots are sophisticated automated scripts or bots designed to manipulate victims through social engineering tactics, tricking them into providing the OTP code sent by the bank or website. Many of these bots are developed to operate on platforms like Telegram, where cybercriminals control them through dedicated bot channels. This enables the cybercriminals to conceal themselves from the actual attacks, making detection and attribution more challenging. Figure 1 show the overview of the OTP Bot attacks.
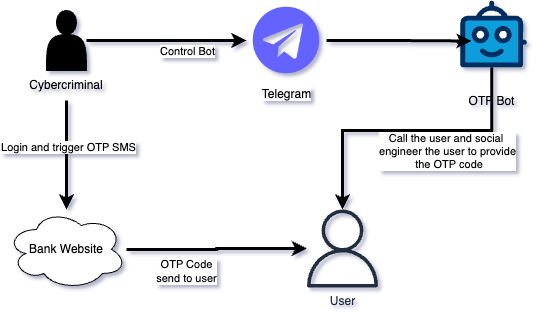
After stealing the credentials through a phishing attack or obtaining them via a malware stealer, the cybercriminal logs into the bank website and triggers the OTP if it’s enabled. The bank then sends the code to the victim via SMS or email. Once the code is sent to the victim, the cybercriminal activates the OTP bot, which impersonates the bank and calls the victim, requesting the OTP. If the victim provides the OTP, the bot receives the code, allowing the cybercriminal to enter it and complete the account takeover.
OTP Bot
There are various OTP bots available in the dark web, with one example being accessible through the Telegram platform. Upon accessing the bot, users can initiate its functionalities. Below are the steps for using one of these OTP bots.
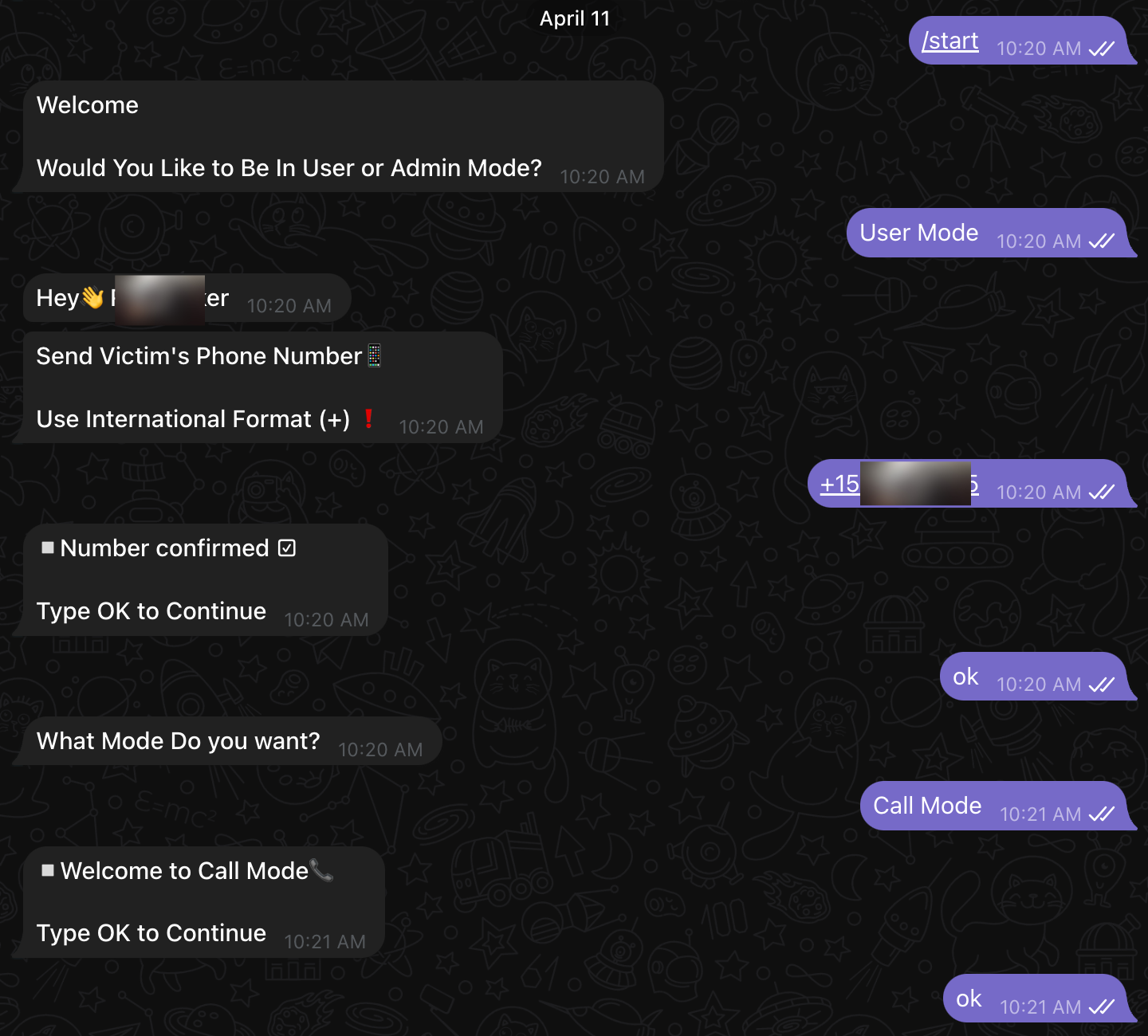
Once logged into the bot, you can enter the victim's phone number. The next step is to select the mode, either call-mode or SMS-mode. In this case we selected Call Mode.
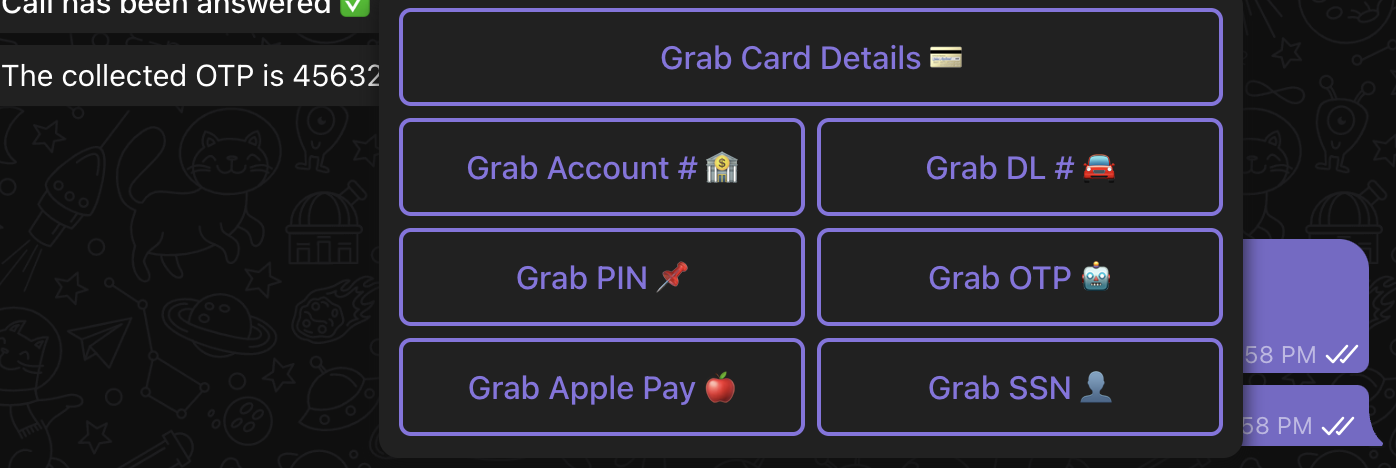
The following step is to select the attack methods. In this case, we select the Grab OTP.
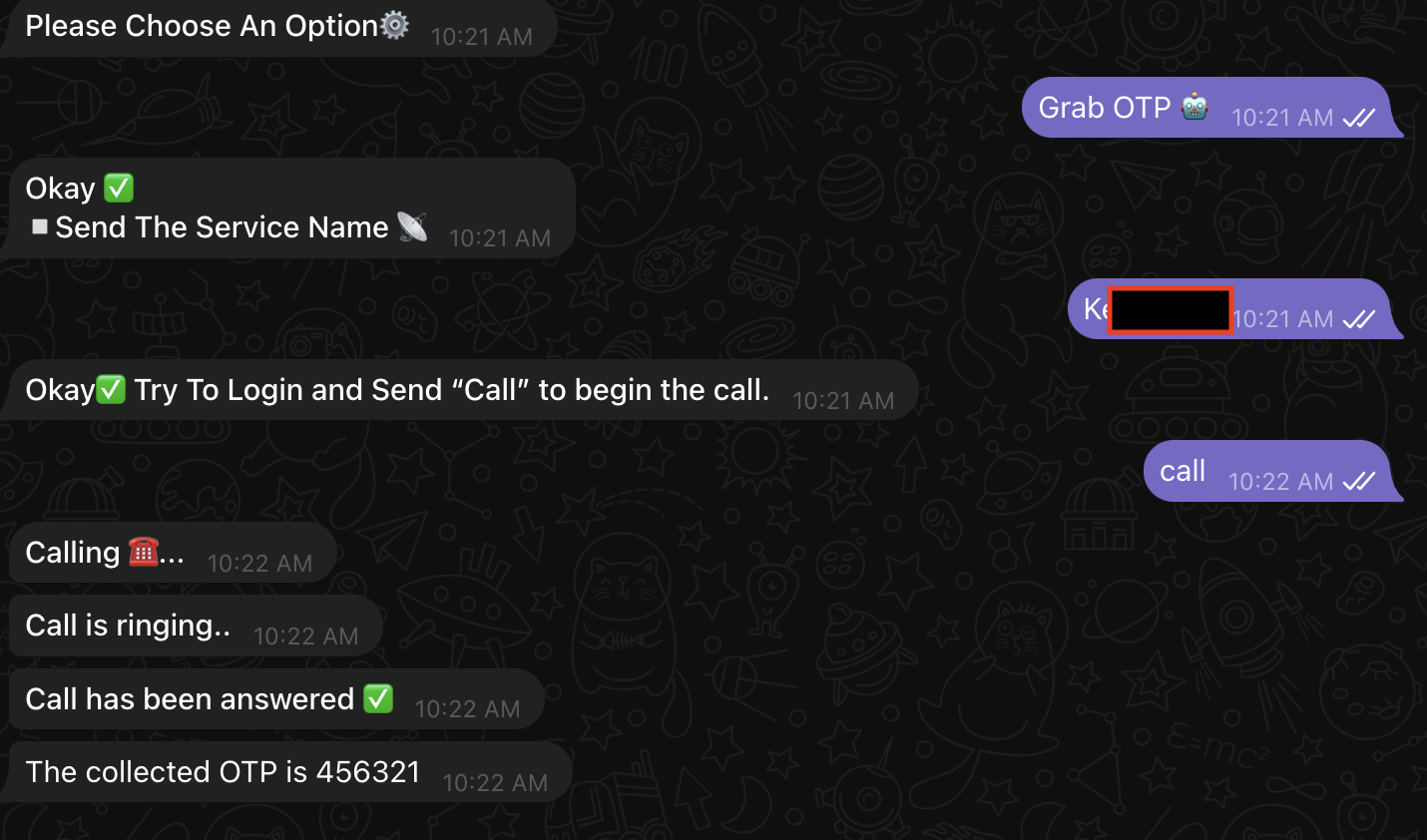
The next step is to enter the Service name. This is the brand we want to impersonate. Once the call is triggered, the bot will call the victim and impersonate the brand. The collected OTP is the one entered by the victim.
The implications of account takeover through OTP bots are significant. Not only can attackers gain access to sensitive personal information, but they can also carry out fraudulent activities such as unauthorized transactions, identity theft, and even extortion.
So, how can individuals and businesses protect themselves against this emerging threat?
- Strengthen Security Measures: Implement additional layers of security beyond OTP, such as biometric authentication or hardware tokens, to reduce reliance on SMS or email-based OTP.
- Educate Users: Raise awareness among users about the risks of phishing attacks and the importance of securing their email and SMS accounts with strong passwords and enabling two-factor authentication where possible.
- Monitor Account Activity: Regularly monitor account activity for any suspicious login attempts or unauthorized access and take immediate action to mitigate potential threats.
- Employ Advanced Security Solutions: Invest in advanced cybersecurity solutions such as endpoint protection, email filtering, and threat intelligence platforms to detect and mitigate OTP bot attacks proactively.
- Stay Proactive: Stay proactive against the latest attacks by utilizing intelligent dark web platforms to stay ahead of cybercriminals.
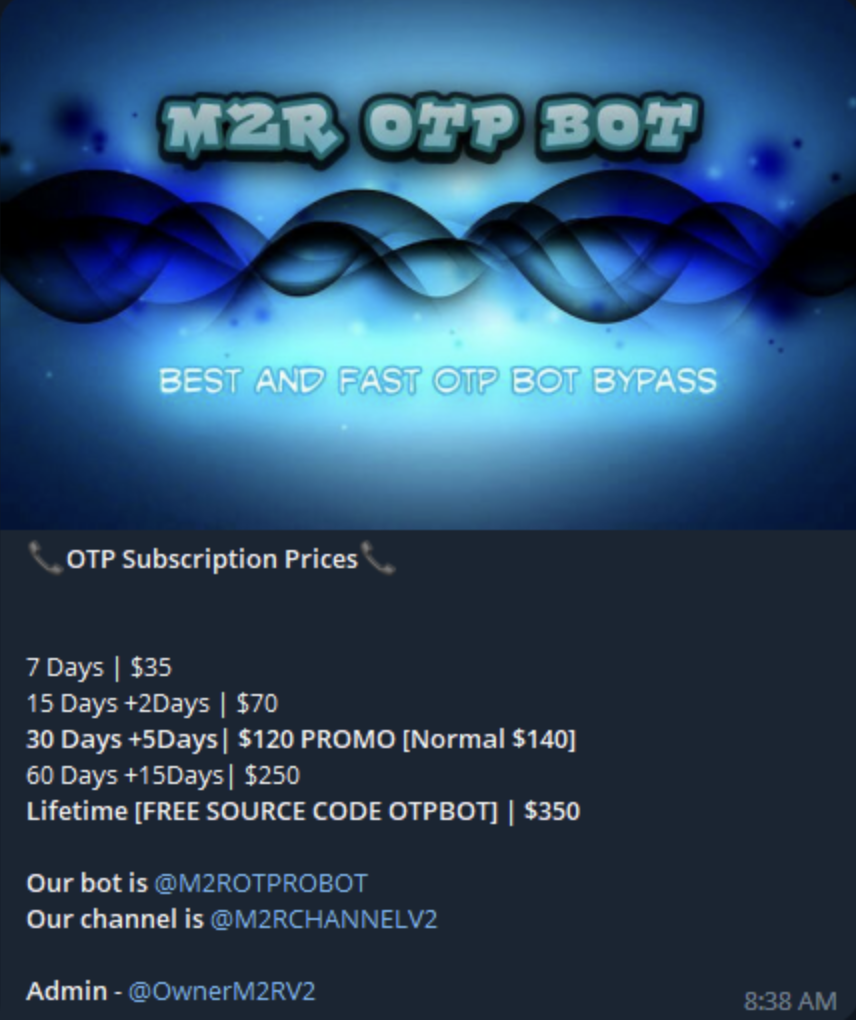
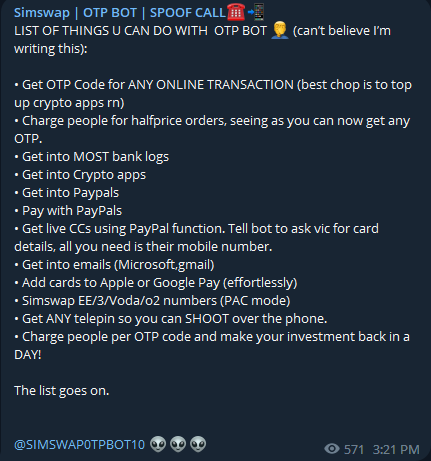
OTP Bot Services
There are numerous OTP bot services available on the Dark Web and Telegram platform. Below are some examples of these services.

Summary
In conclusion, account takeover through OTP bots represents a significant cybersecurity threat in today’s digital landscape. By implementing proactive security measures, raising awareness among users, and staying vigilant against evolving threats, individuals and businesses can effectively mitigate the risk of falling victim to OTP bot attacks and safeguard their valuable assets and sensitive information.





