While not as established as Genesis Market, these new marketplaces offer stolen data, logs, and credit card information. Through effective marketing, they provide an adequate platform for fraudsters to turn a quick profit. This blog will provide an overview of these emerging marketplaces catering to cybercriminals. Cybercriminals no longer had to rely solely on Tor to access marketplaces, and they were less susceptible to scams from sellers. The real-time communication facilitated by these chat services, especially Telegram, allowed fraudster buyers to interact with sellers more effectively, increasing their success rate and reducing the risk of falling victim to scam sellers.
Telegram Market
With the growing popularity of end-to-end chat services, cybercriminals are shifting their operations to platforms like Telegram. The Telegram platform offers developers the opportunity to create applications within the ecosystem. Seizing this chance, cybercriminals are incorporating their services into the platform, allowing customers to securely purchase services, automate their attacks, and receive real-time customer support.
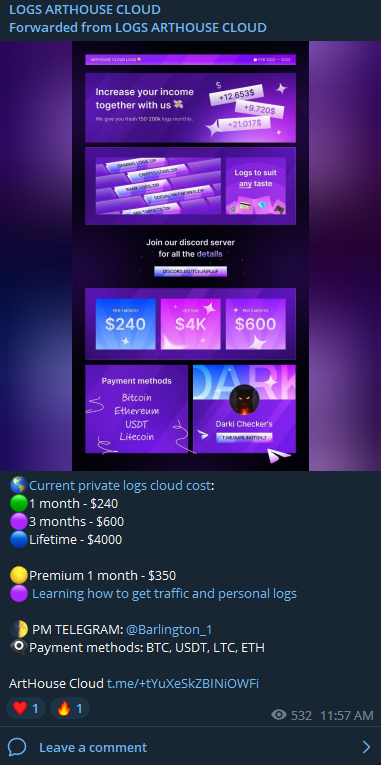
Logs/Credential
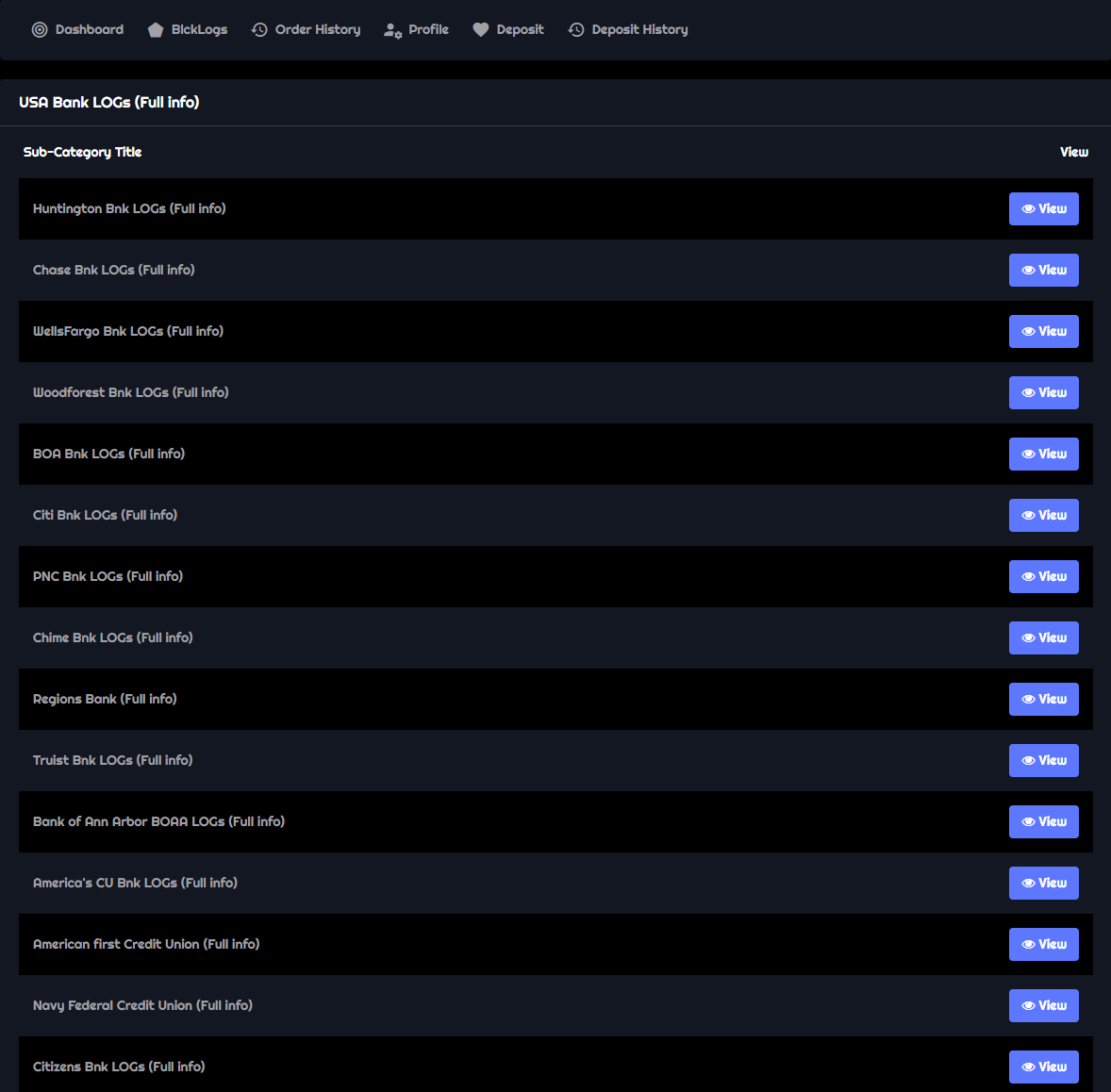
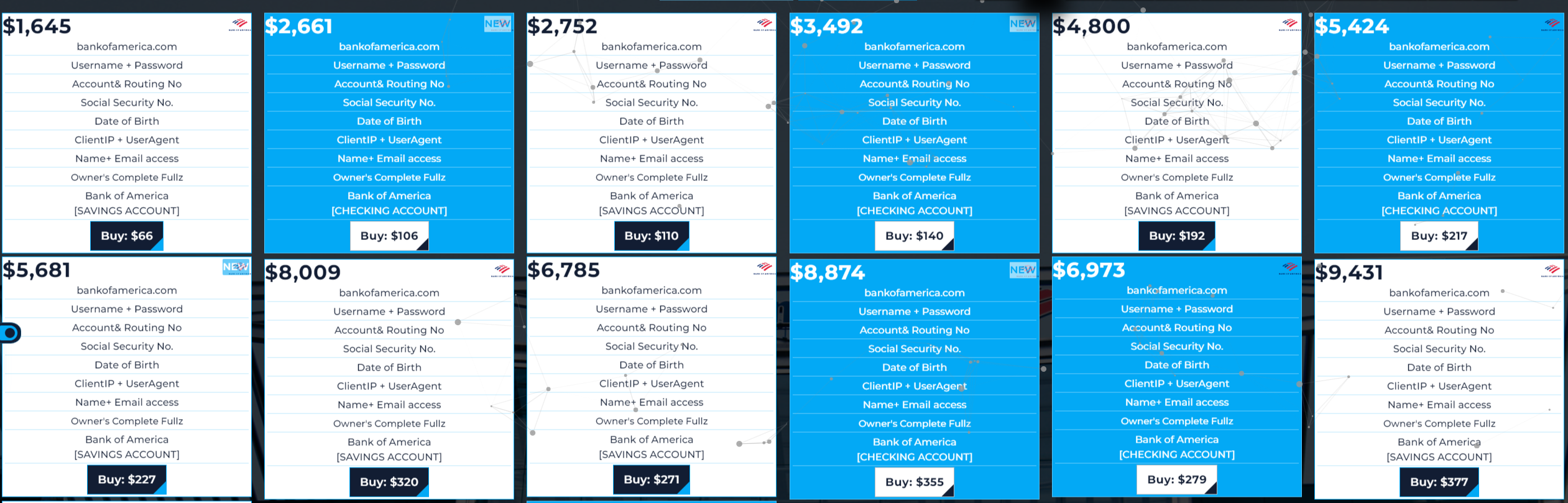
Similar to the Genesis market, cybercriminals have established markets on Telegram where fraudsters can buy accounts, including access to bank accounts. These accesses typically include bank credentials (username/password) and email access. For as low as $100 dollar (depending on accounts balance), fraudsters can take control of an account and engage in fraudulent activities.

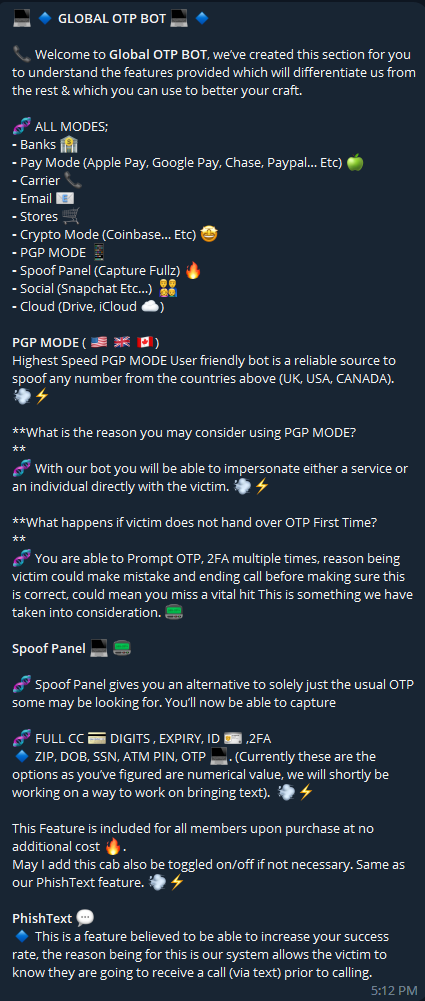
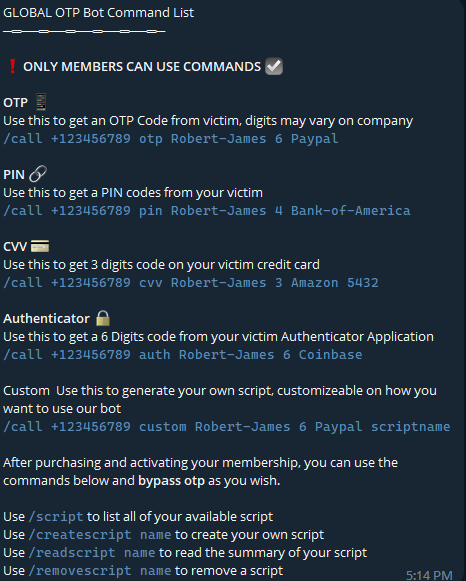
OTP Bot Automation
With the rise in account takeovers, organizations are increasingly implementing multi-factor authentication to mitigate the risk. Consequently, cybercriminals have started offering OTP bot services. In this scheme, the fraudster supplies the victim’s phone number and the targeted brand to the OTP bot. The bot then makes a call to the victim, posing as the brand’s call center, and captures the one-time passcode (OTP). The obtained passcode is then provided to the fraudster, enabling them to execute their account takeover. These services operate as fully automated processes. Below are some examples of such markets.


Open Market Place
Much like the Telegram market, cybercriminals are now harnessing cloud technology and web development frameworks to create their platforms for selling stolen data, akin to the Genesis marketplace. While these new platforms may be limited compared to well-known markets, they signify a trend where cybercriminals are deploying their own platforms on the clear web.
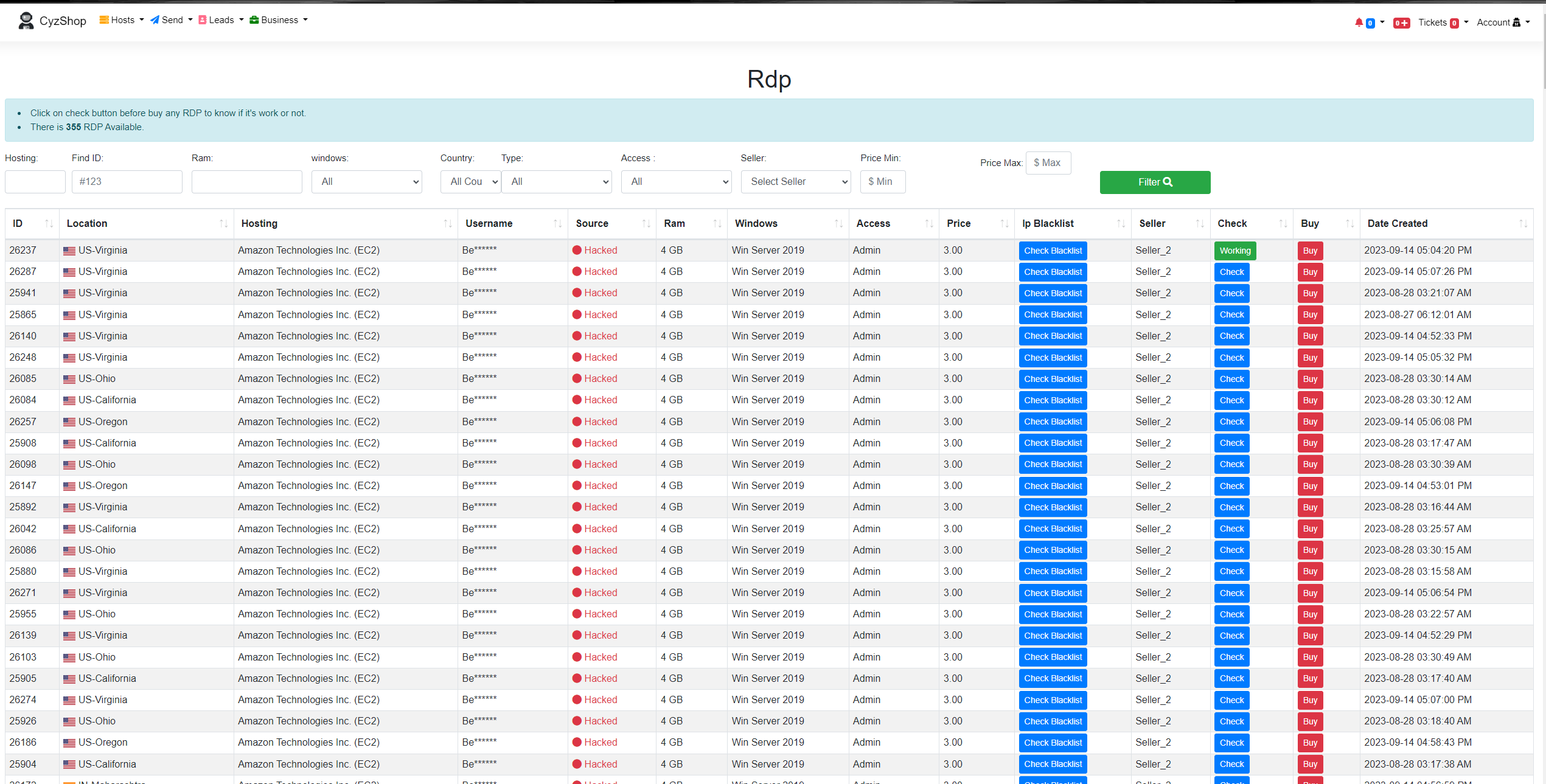
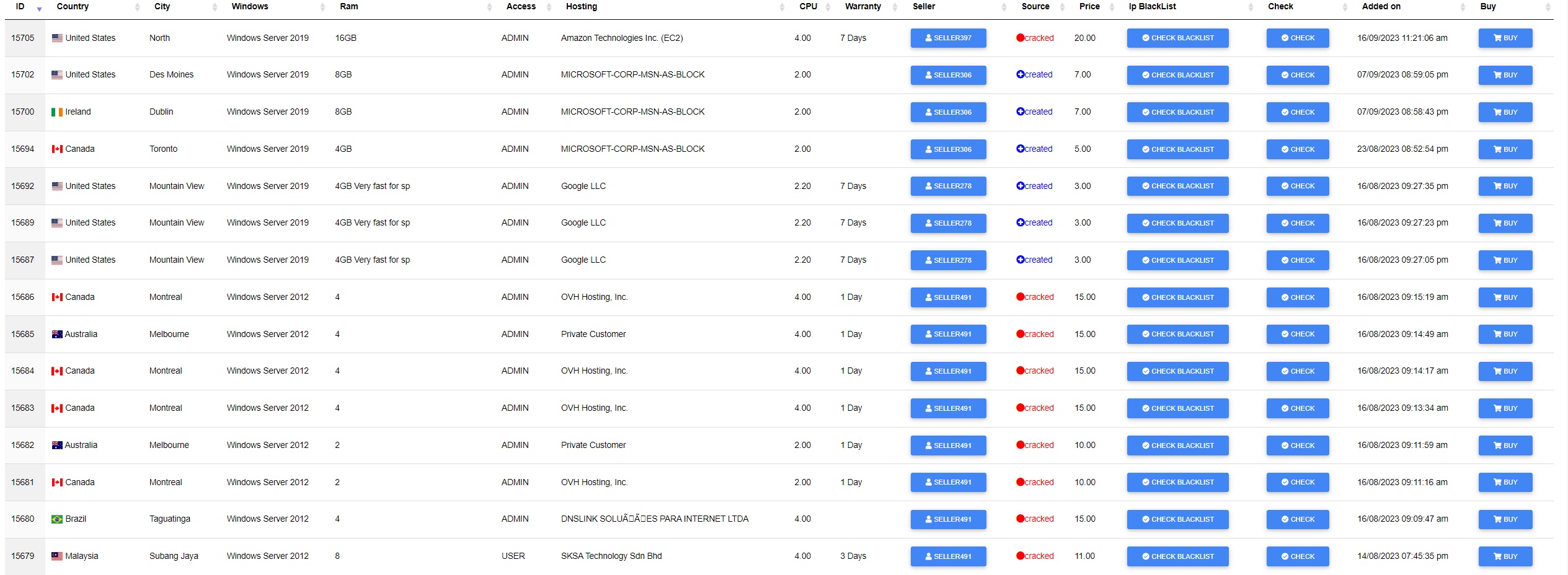
New Market
These new marketplaces on the clear web are often hosted on a cloud platform such as Google Firebase. These websites are usually open for anyone to register and make purchases. They commonly use cryptocurrency as the payment method, with goods delivered via email. Here are some examples of such marketplaces:


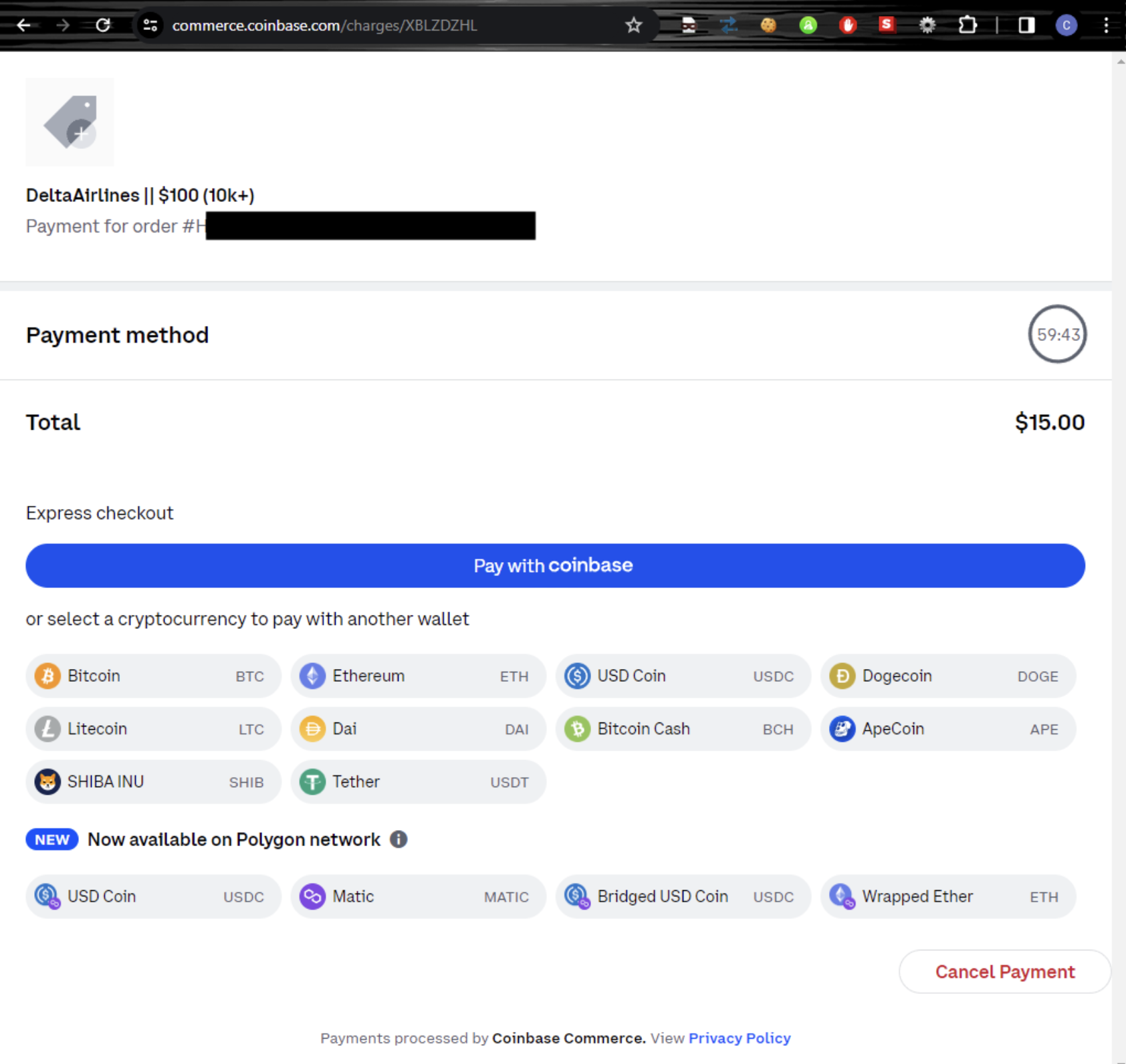
Payments
The Coinbase’s commerce platform is the common platform these cyber criminal use as a payment method. While other website provide their Bitcoin address for the buyer to send money in. The Coinbase’s platform is much more flexible method as it track the session of the buyer and able to validate of the credit available for purchase. Below are some example of the payment.

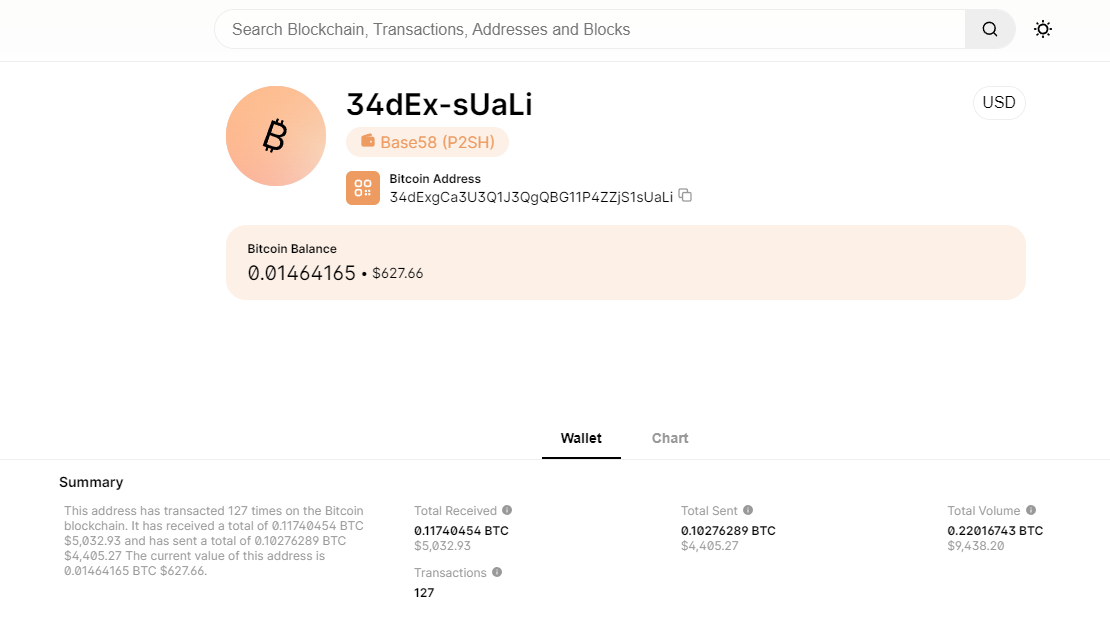
Some websites utilize Bitcoin as a payment method. However, instead of generating a unique Bitcoin address for each user, they use a single address for all payments. This practice can be tracked using blockchain trackers. Below is the address of a marketplace named ‘logpoint’. Records show that they have received crypto payments 127 times, totaling more than $5,000 in US dollars.
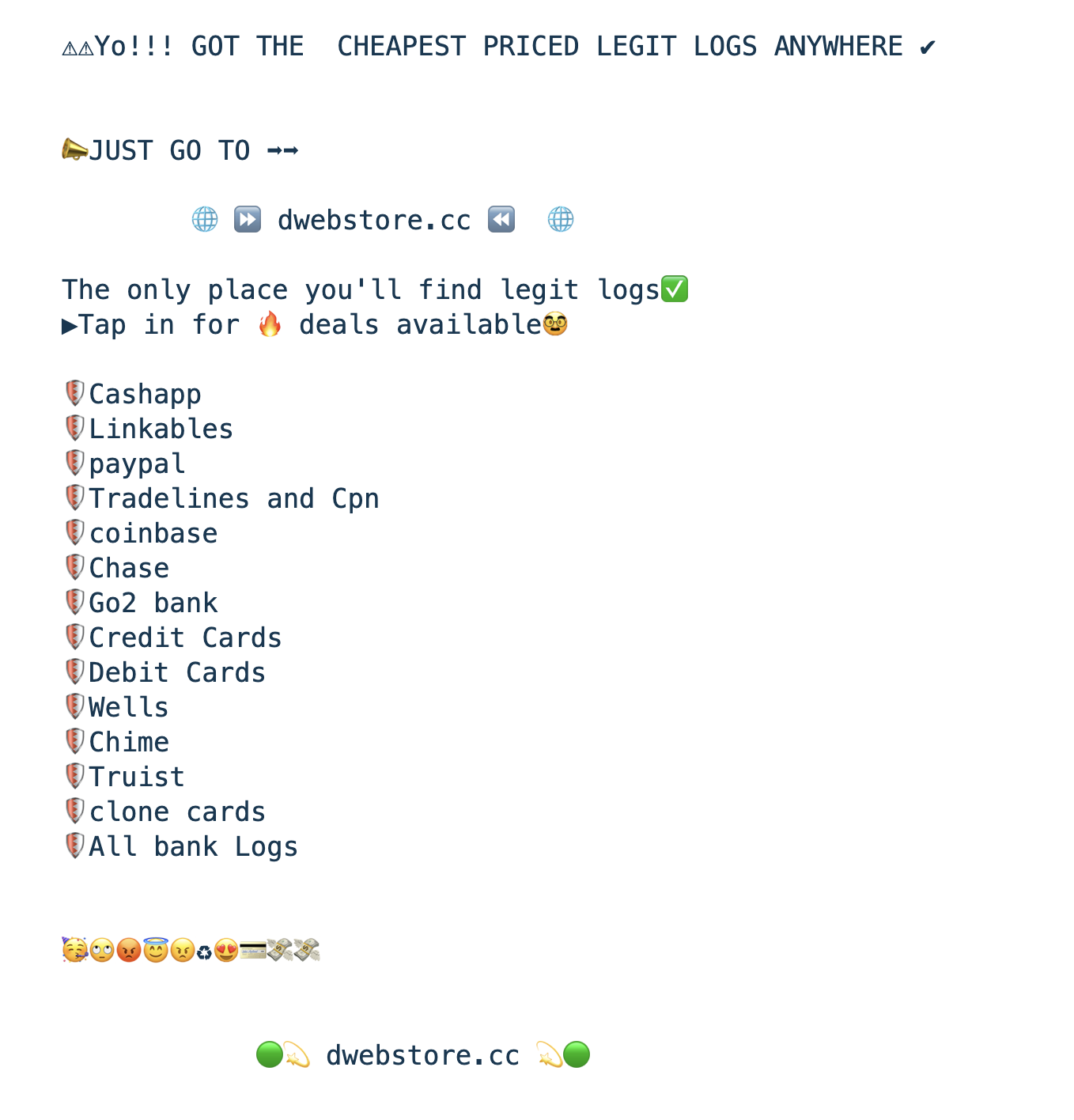
Marketing/Advertisement
In these emerging markets, marketing and advertising play a crucial role. As these markets are new and lack endorsements, continuous advertising is often necessary. Telegram provides cybercriminals with an easy way to create networks and promote their products. Here are some examples of marketplace advertisements:

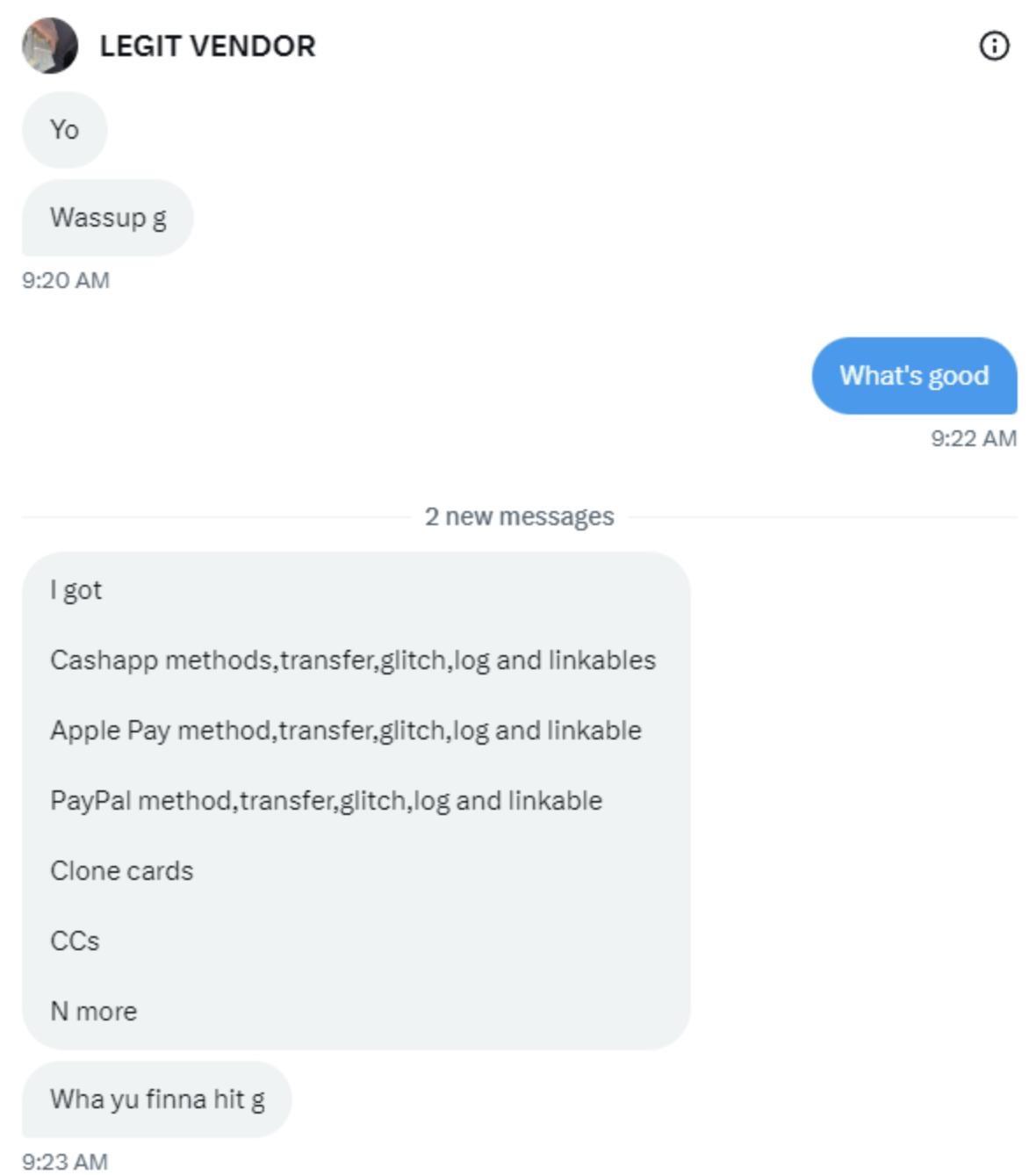
Vouches
Vouches serve as a form of reputation-building within cybercriminal circles. When a cybercriminal successfully conducts a transaction or provides a service, others may vouch for their reliability and effectiveness. These endorsements function as a dubious currency, signaling to potential clients that a particular actor can be trusted in the illicit landscape. Here are some examples of vouches for these cyber criminals.

Conclusion
This evolution paved the way for the emergence of smaller-scale marketplaces operated by individual groups or even single actors. Although not as established as renowned platforms like Genesis Market, these new marketplaces serve as hubs for stolen data, logs, and credit card information. Through strategic marketing, they offer fraudsters a viable platform to swiftly turn a profit. As cybercriminals move swiftly, it is imperative that we match their pace, adapt to their evolving methods, and stay one step ahead. At CyberArmor, we are committed to continuous research, enabling financial institutions to take prompt action and consistently disrupt these emerging marketplaces.