How It Starts
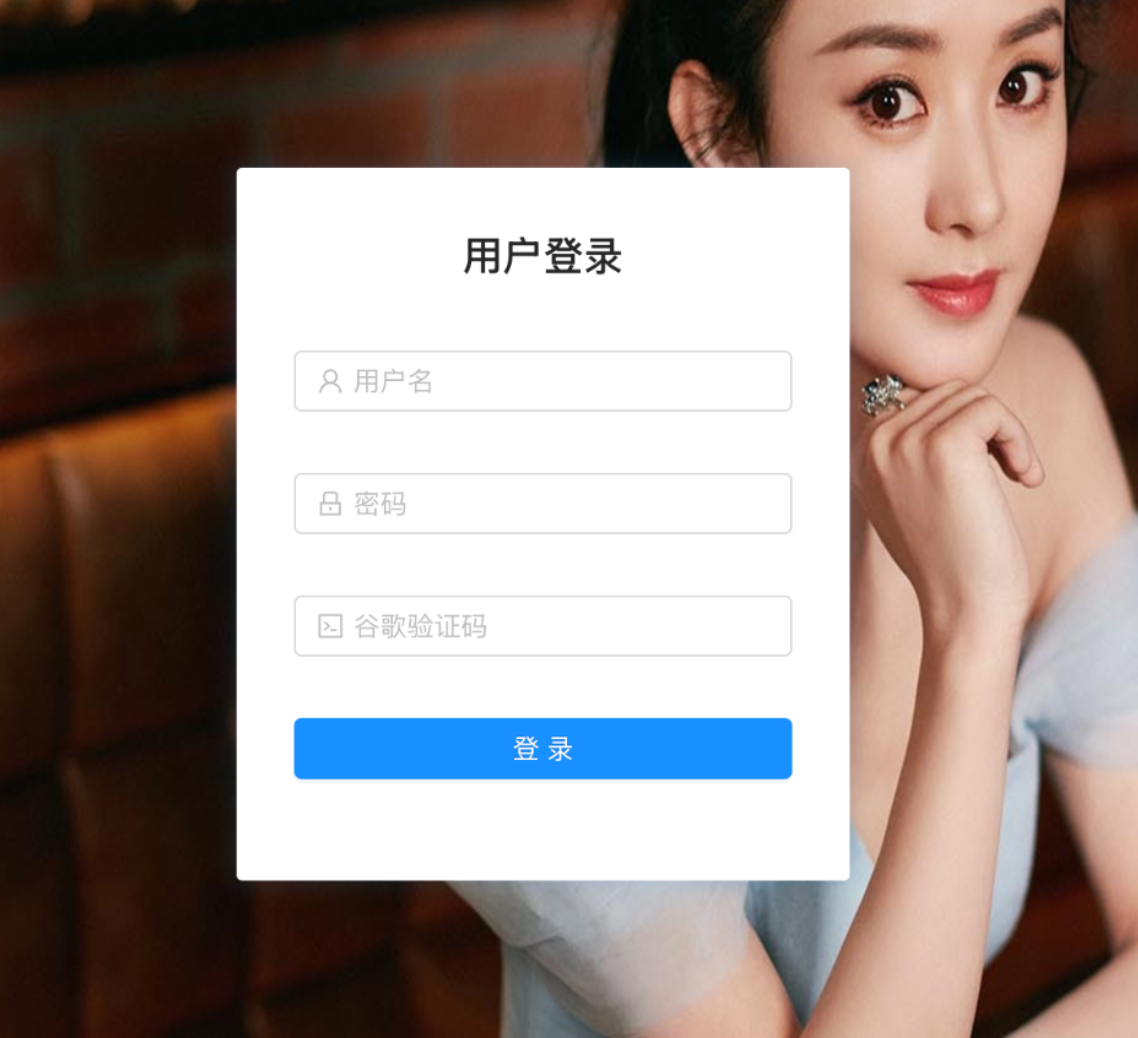
CyberArmor’s team identified an intriguing desktop screenshot taken by a infostealer. The user is infected with WorldWind, also known as StormKitty, a infostealer. Once infected, the malware captures screenshots and collects system information, including browser passwords, browsing history, and cryptocurrency application data. Figure 2 shows the screenshot captured by the WorldWind stealer.
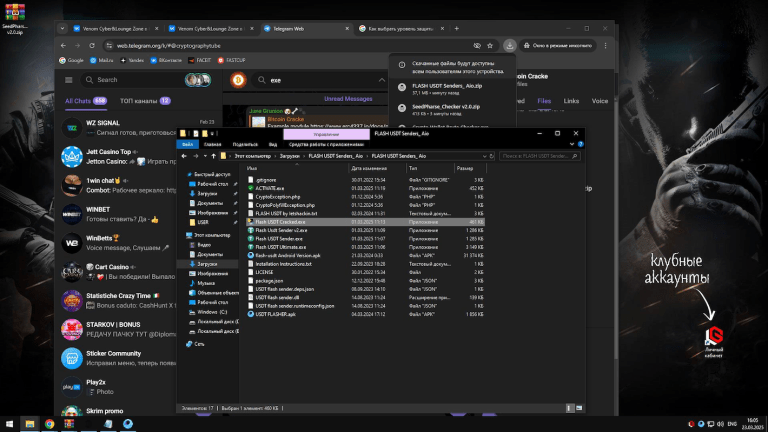
The screenshot reveals a folder containing a software named FLASH USDT Senders, which the user recently downloaded. In the background, the user’s Telegram is visible, showing the group https://t.me/@cryptographytube. This is a potential source of the malware infection. Analyzing the software could provide further context on how the infection occurred.
By analyzing the folder name and the Telegram channel, we identified that the software was shared by a user named Brain Box, with the Telegram ID 7101105223. Figure 3 shows the Telegram message where the user shared the software.

Flash USDT Sender
Flash USDT Sender is a software that allows users to create fake USDT transactions, simulating confirmed blockchain transactions that remain visible for 90 days. Scammers use this software to deceive victims by generating fake transactions, making it appear as though a payment has been completed.
Sample Overview
The sample shared by Brain Box has the following properties.
Filename: FLASH USDT Senders_ Aio.zip
MD5: df9aa637c6f482d7b5e55b2bafa70023
SHA1: 21299aac3fef64e0f812d486d571eedf03b8e9db
SHA256: fbe554b708be46efb6e6e96745133dcc0bf2f90051e91571360bd801ad8bc8f2
File Size: 38,877,929 bytes
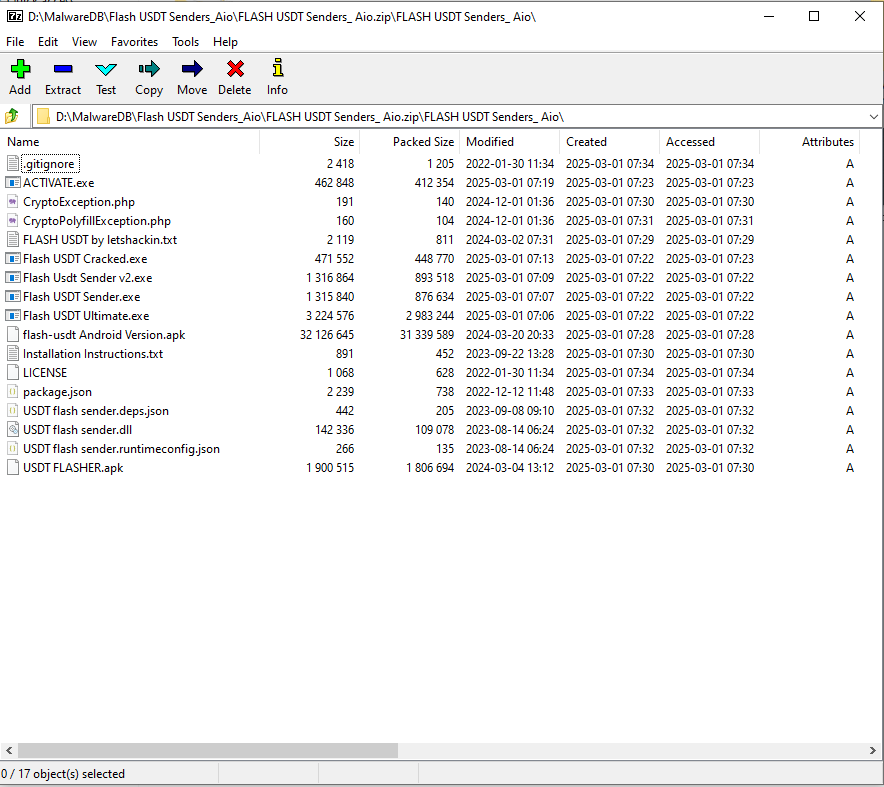
The software contains various files, with the main Windows executable having the following properties.
Filename: Flash USDT Sender.exe
MD5: cddd6cbe3647a3e2cc16f30cf896997b
SHA1: 92ed4117ddfb76d166d1a0a2cd1d4e13c524dab4
SHA256: 0daf5698a1d810cbc872c291049c5a917f3805e53c118e575af698ff8e480ccf
File Size: 1315,840 bytes
File Type: PE32 executable (GUI) Intel 80386 Mono/.Net assembly
Flash USDT Sender
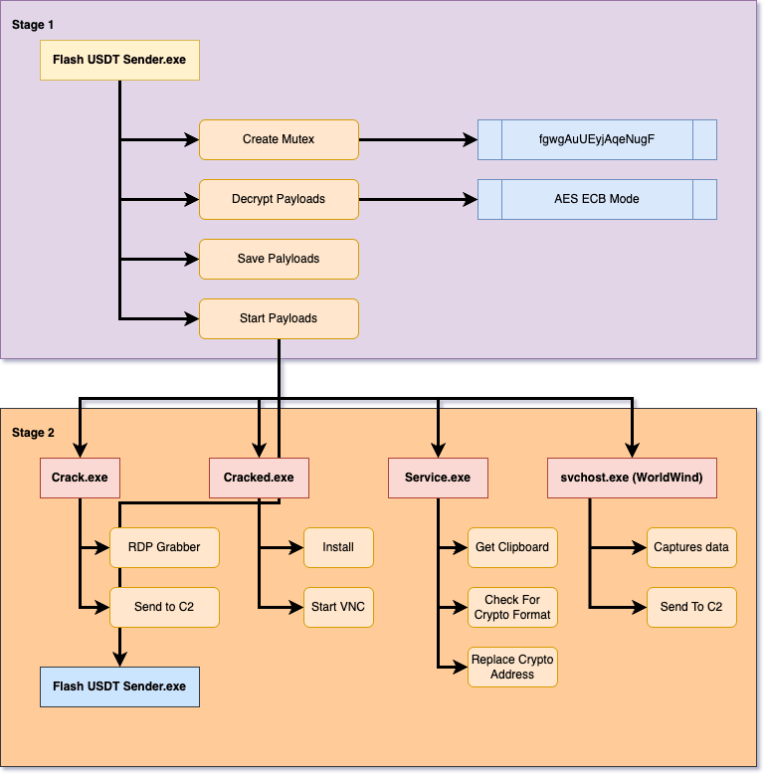
Flash USDT Sender is a .NET application that initially appears to function like standard software. However, analysis with dnSpy revealed it to be a malware dropper. The software contains five encrypted payloads within its resources. Upon execution, it decrypts these payloads, installs them in %APPDATA%, and then launches them. As shown in Figure 5, the software includes payloads named crack.exe, cracked.exe, service.exe, svchost.exe, and Flash USDT Sender.
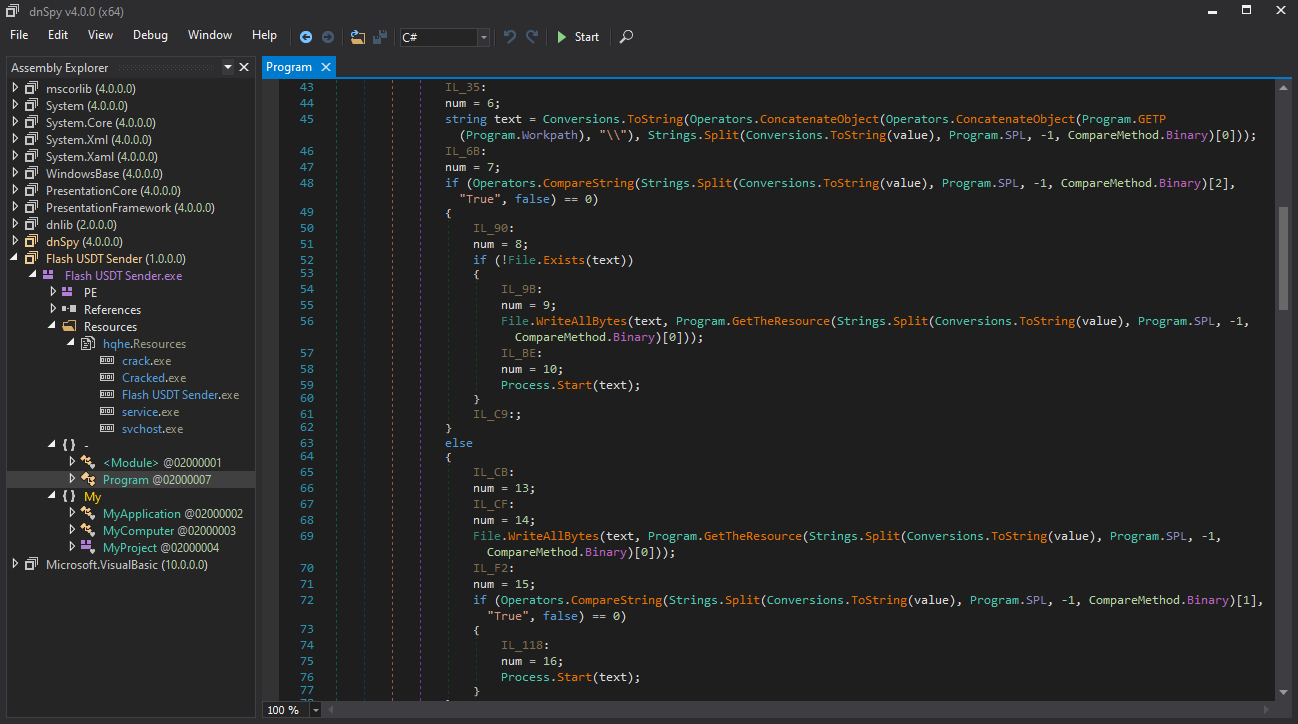
The payload is encrypted using AES in ECB mode, with the key derived from the MD5 hash of the mutex (“fgwgAuUEyjAqeNugF”). Figure 6 shows the decrypted payload in CyberChef.
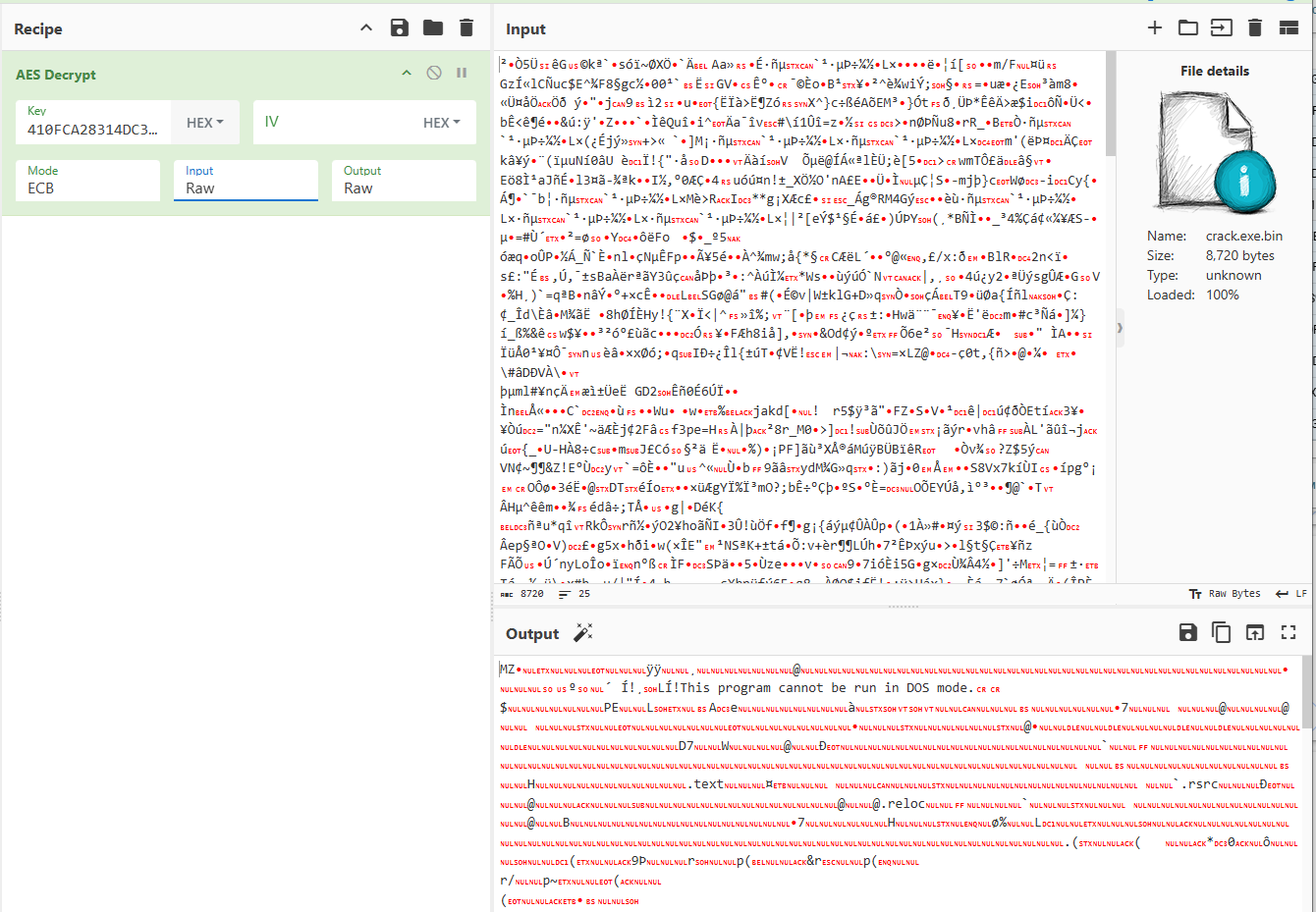
Decryption Key
410fca28314dc32b044f8efd36cdf316
Payloads Overview
Once decrypted, the loader drops the executable into the %APPDATA% directory and executes it. The following are the properties of the decrypted payloads.
crack.exe
MD5: 9215015740c937980b6b53cee5087769
SHA1: a0bfe95486944f1548620d4de472c3758e95d36a
SHA256: a5390a297f14ef8f5be308009ec436d2a58598188dbb92d7299795a10ba1c541
File Type: .NET executable
cracked.exe
MD5: 0dfa83a82f6418c73406d78296de61be
SHA1: dd7eceef8a434c43e0751e180bf714e08771d336
SHA256: 8d27369ffa8b29d561fa9daf485be14d2fc00287bb1c69d4c84d514891c8db5e
File Type: .NET executable
service.exe
MD5: f2e3df6480be8613cddb3319d70536fb
SHA1: c3fd8bfcb699432852b4dd5149fd979a026a2a9f
SHA256: 3218439f6308183f5d2fb10e8c6d4f0befe23dcc5231a7d55c41ff1f5d0762d7
File Type: .NET executable
svchost.exe
MD5: 36e79d9c029304417b9e0a142eb22a42
SHA1: ec3e50b99c320bf80cf990558da8707fbb52edab
SHA256: b9b3b3630d78ed68c6cca1fb41fe51fa1626c6a58bd62387d824e344b8e451bb
File Type: .NET executable
Flash USDT Sender.exe (Real)
MD5: ac7938b542469a1c5bb108fc046ac87b
SHA1: 9571a4ab3359b982f0ab33b03e815df8c354b0f3
SHA256: 1efd1de7aef995821042509c66121a942c7ee8e004badbb4e14a10b5d7c96292
File Type: .NET executable
Crack.exe (RDP Grabber)
This malware is an RDP grabber. Upon execution, it checks if the system is listening on port 3089. If the port is open, the malware attempts to change the password and sends the new credentials to the C2 server.
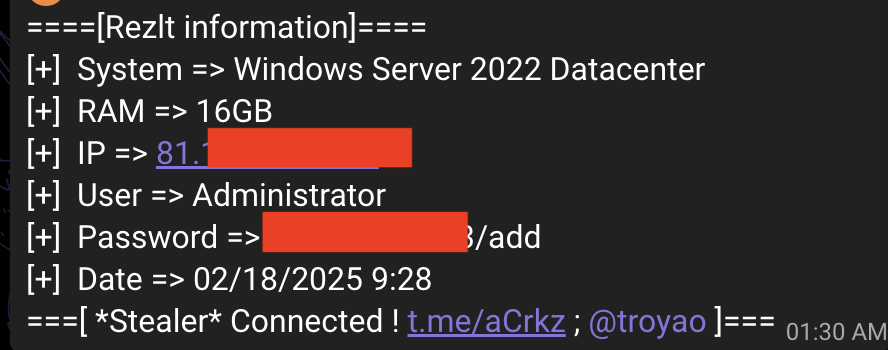
Currently at this time, we observed there are 198 system is infected with this malware.
Cracked.exe (VNC Server/Keyboard Sniffer)
This malware functions as a VNC server and keyboard sniffer. Upon execution, it starts a VNC server and initiates a keyboard sniffer, which captures keystrokes and transmits the data to its command-and-control (C2) server. Below is the identified C2.
185.252.232[.]158
64.23.232[.]116
Service.exe (Crypto Clipper)
Crypto Clipper is a type of malware that monitors the Windows clipboard. It retrieves clipboard data and searches for cryptocurrency addresses. If a cryptocurrency address is detected, the malware replaces it with the attacker’s address. This manipulation redirects the transaction to the cybercriminal’s address instead of the intended recipient.
At this time, several transactions have been recorded for Bitcoin, Tron, and Ethereum. Below are the attacker’s cryptocurrency addresses.
Bitcoin
bc1qzmt3wunk3a7r4fy26kyye6suvmhufsuqv893pm (0.0021084)
1FoAEgf2zUxZZnLnrh4NySvFjuVCUdJ7Lq
39myS6nW3UMUq4KD2cG9p7RAHuhmKEp1UZ
Litecoin
ltc1q2ecs69500vws8rju88qg6dxful8qrsaycntwy5
Le9YSUdEzne4PqFWi3aqQQKHwFyqNrobuc
ltc1q2ecs69500vws8rju88qg6dxful8qrsaycntwy5
Le9YSUdEzne4PqFWi3aqQQKHwFyqNrobuc
Dash
DQQ32u8NaGAHCpCsWgvGo11uiTuMbtushe
Ethereum
0xb99cF9Af6fE91eD030542F730bc384258eA4f365 (0.006963554980524)
XRP
rpEcRxoWq7XinwuGBPNtb9NF49uXR4QWBz
TRON
TTSW5A1wjmkzvrpq36yREcHKE2cQ9f8t4Y
Svchost.exe (WorldWind Stealer)
WorldWind Stealer (also known as StormKitty) is a type of malware primarily used for stealing sensitive information from infected systems. It targets users’ personal data, including passwords, browser history, and information related to cryptocurrency applications. Once the malware infects a system, it typically performs the following actions:
- Screenshot Capture: The malware captures screenshots of the user’s desktop, often to gather additional information or monitor the user’s activities.
- Data Theft: It extracts stored passwords, browsing history, and cryptocurrency application data, targeting platforms like Bitcoin wallets or other digital asset management tools.
- Exfiltration: The stolen data is sent back to the cybercriminal’s command-and-control (C2) server for further exploitation.
Figure 9 shows a screenshot of the decompiled code of the malware.

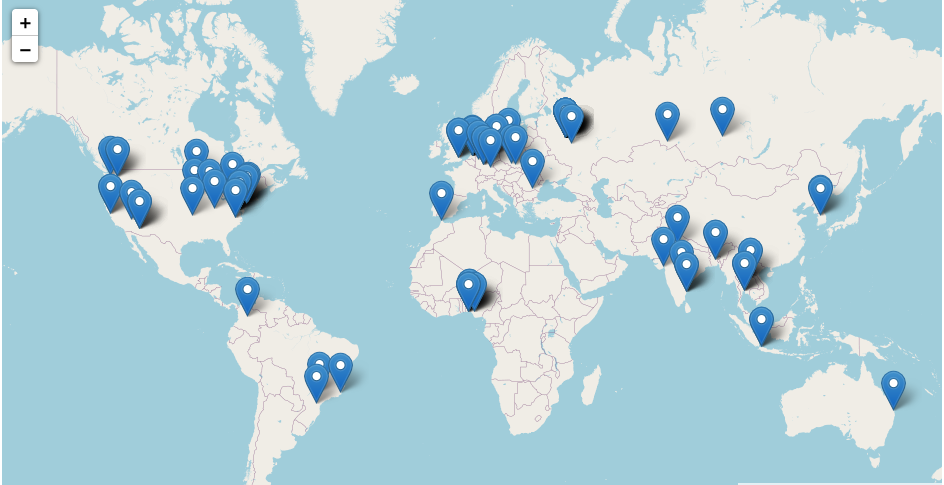
Currently, we have observed 43 infected machines. Below is a map showing the locations of the infected users.

The following images show the desktops of the infected systems.
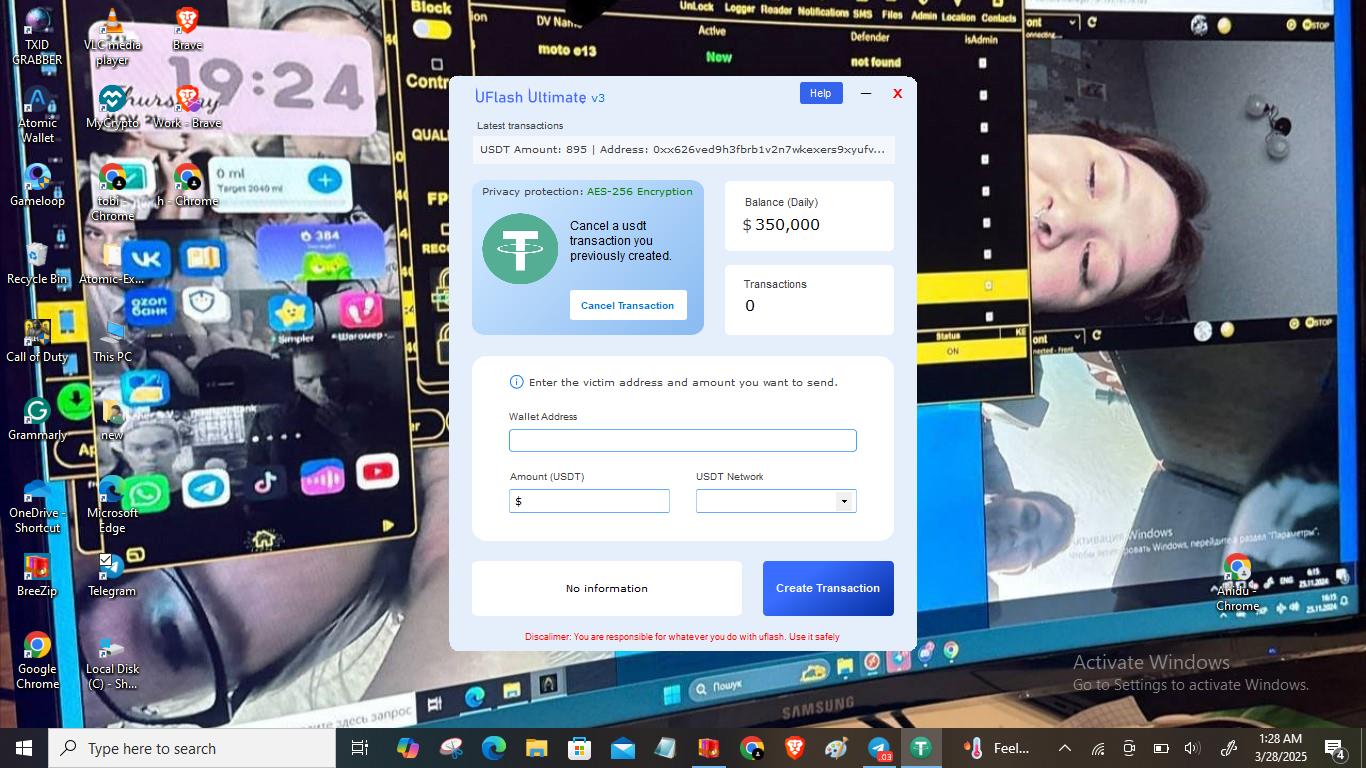
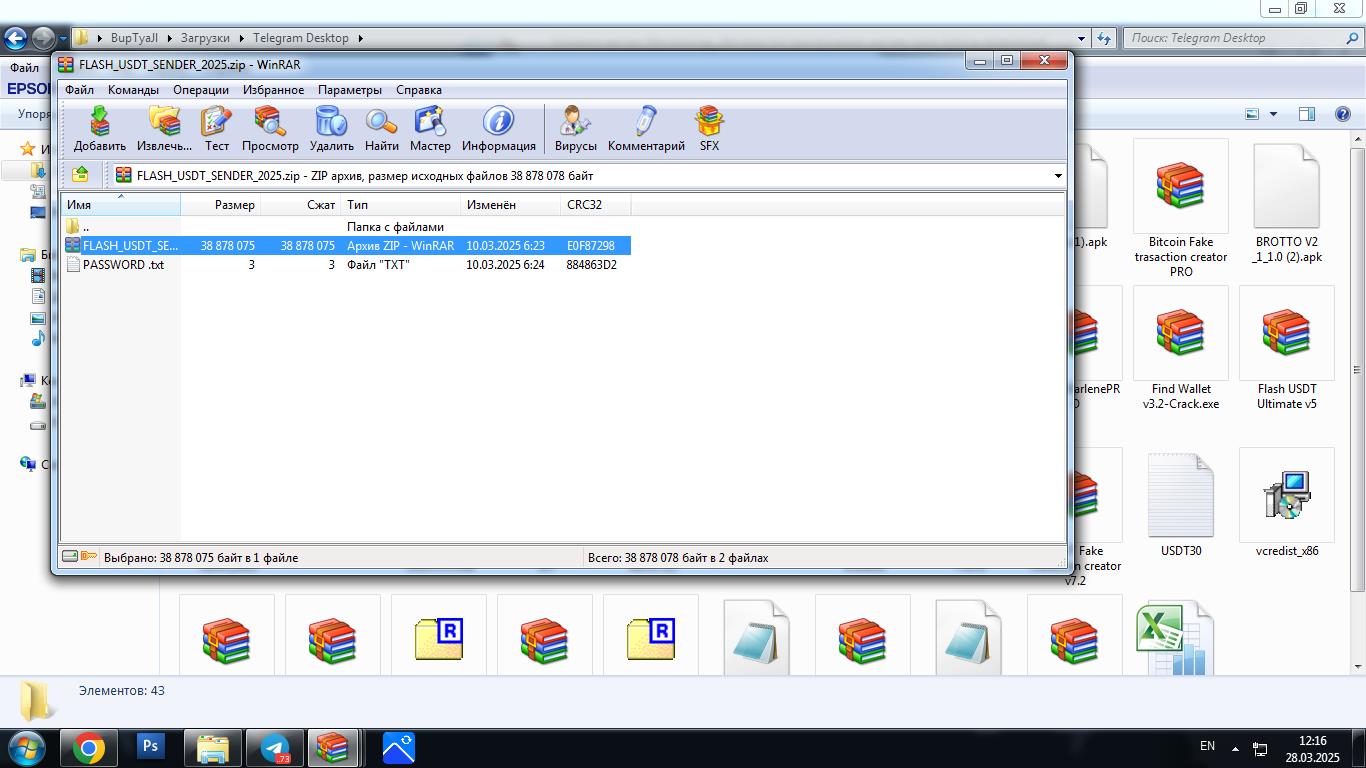
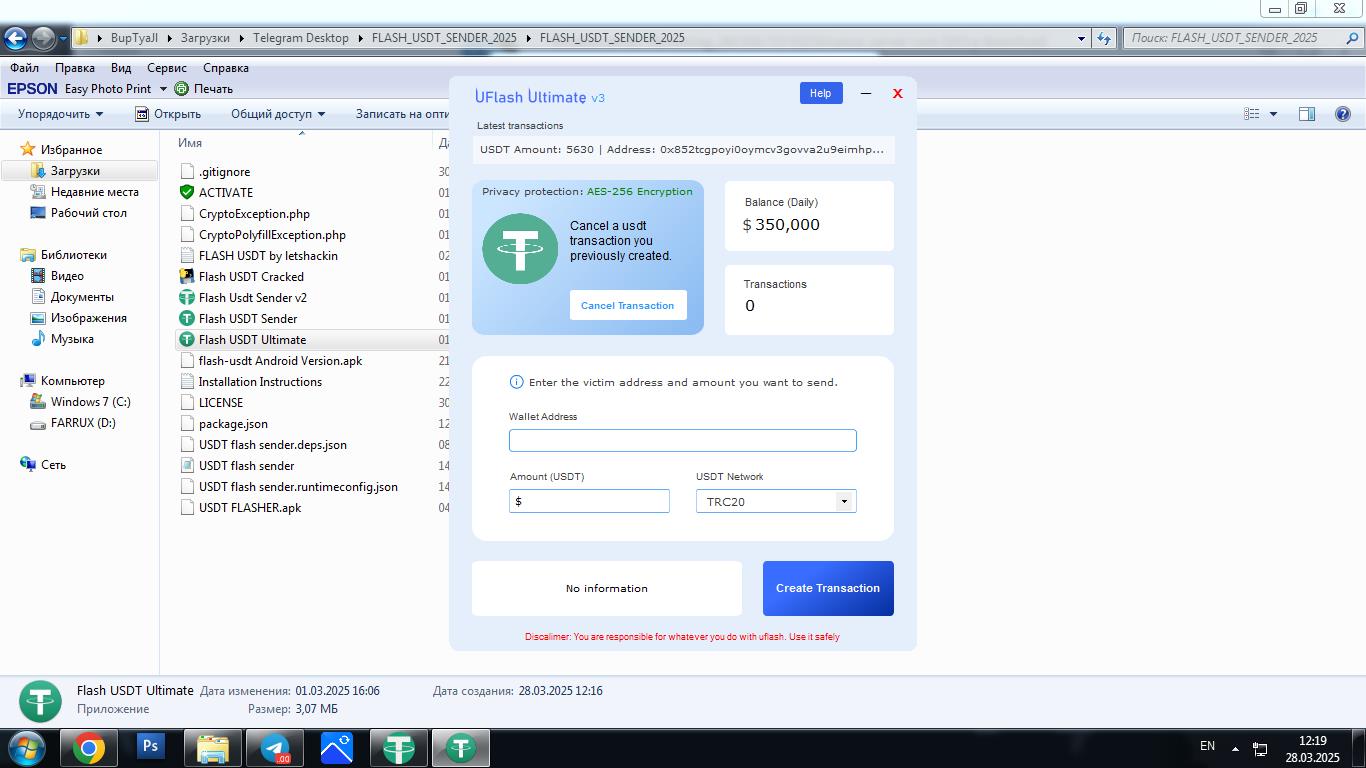
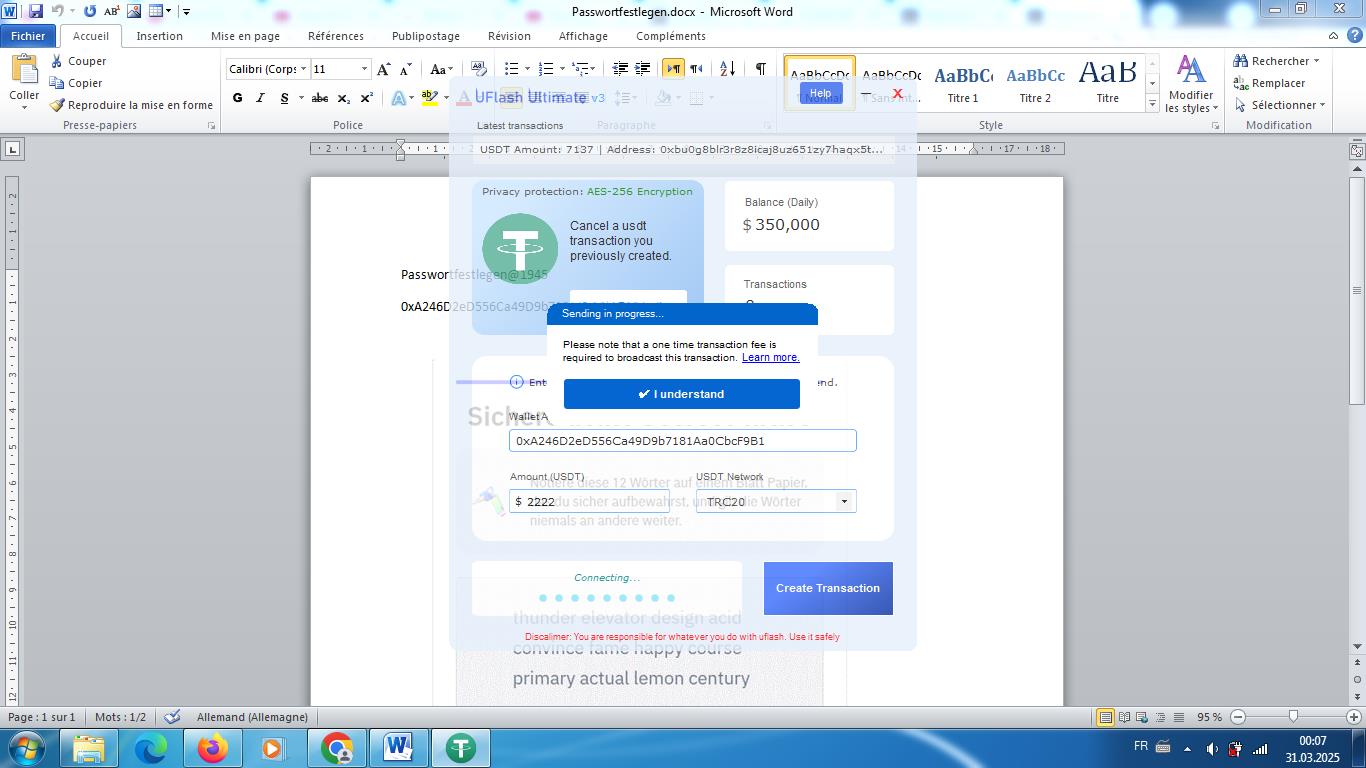

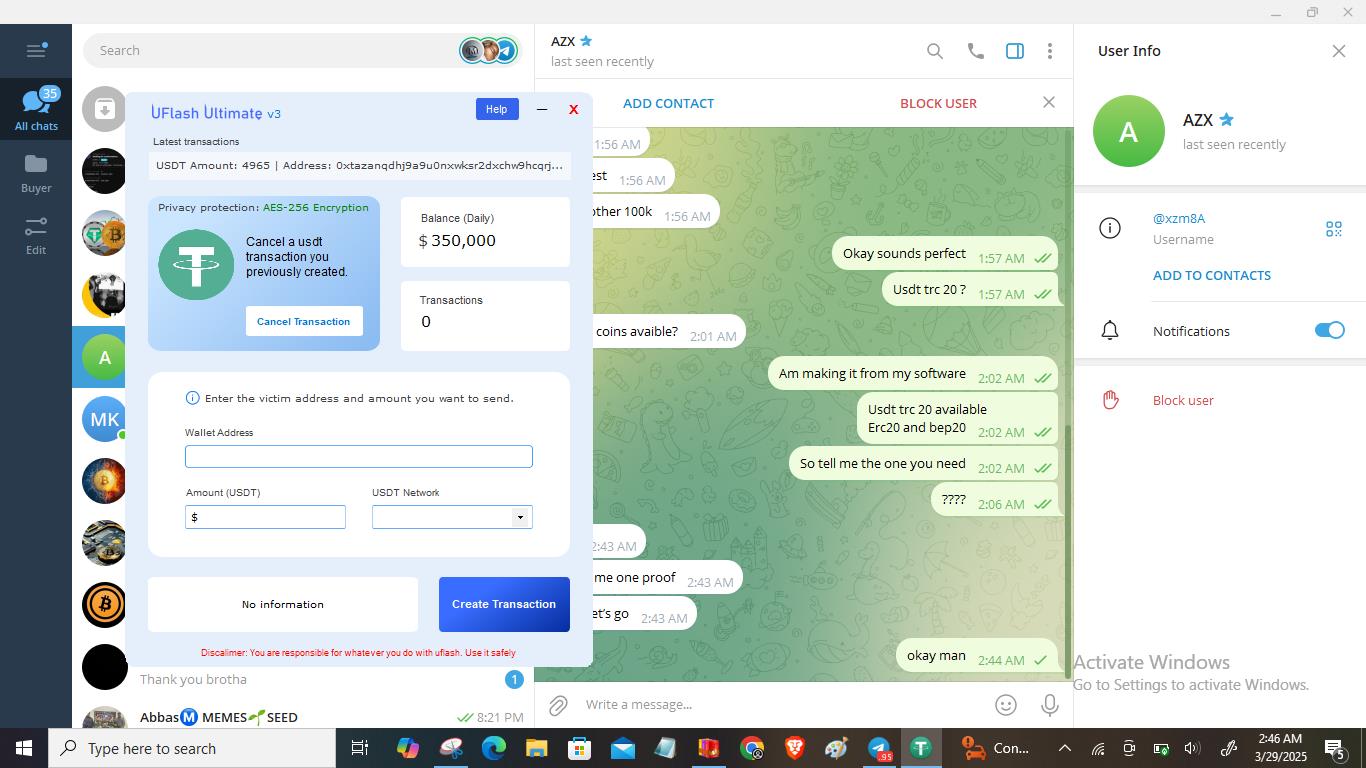
Conclusion
From a simple software download to infecting the system with four different types of malware, this attack demonstrates the severity of modern threats. By monitoring clipboard activity, logging keystrokes, deploying hidden VNC servers, and executing a infostealer, the attackers gain full control over compromised devices. The discovery of infected systems and active transactions linked to the attacker’s addresses further underscores the need for heightened security measures.
To mitigate such threats, users should avoid downloading software from untrusted sources, enable multi-factor authentication, and actively monitor credential exposure to stay ahead of potential attacks.
Protect Your Assets with CyberArmor
Phishing and infostealers pose significant threats to organizations. Understanding these threats and the techniques cybercriminals use to target individuals and businesses is crucial. Organizations can stay proactive and ahead of threat actors by leveraging threat intelligence. Speak to our team to learn how the DarkArmor Intelligent Platform helps protect organizations and mitigate emerging threats.