We believe that gaining insight into the cybercriminal process in various attacks is essential for detection and countermeasures. This blog provides an inside look at a malware campaign from the hacker’s perspective, covering email harvesting, campaign setup, delivery, and email sample.
Email Harvesting
The first step in a malware campaign is gathering a list of potential targets. While there are various methods cybercriminal used to harvest email address. Below are some of the common methods.
- Scraping Public Databases - Extracting emails from websites, forums, and social media platforms like LinkedIn and Facebook.
- Data Breaches & Leaked Lists – Acquiring bulk email addresses from dark web marketplaces.
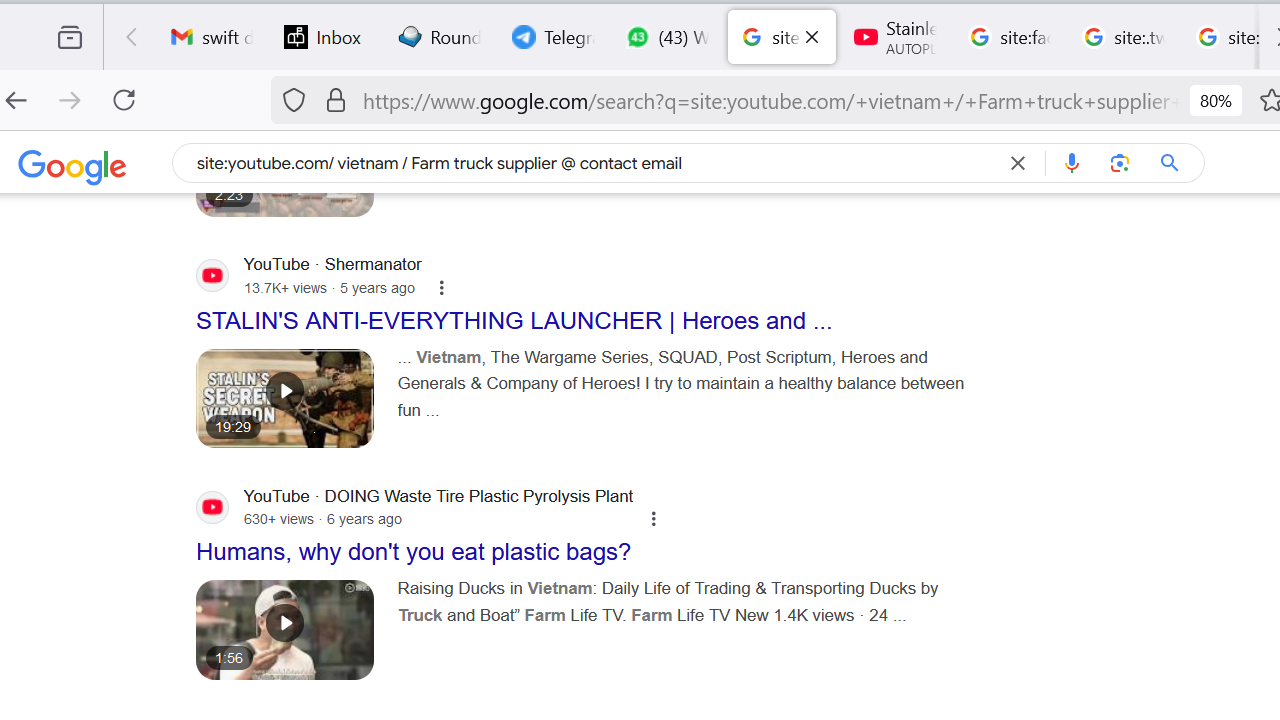
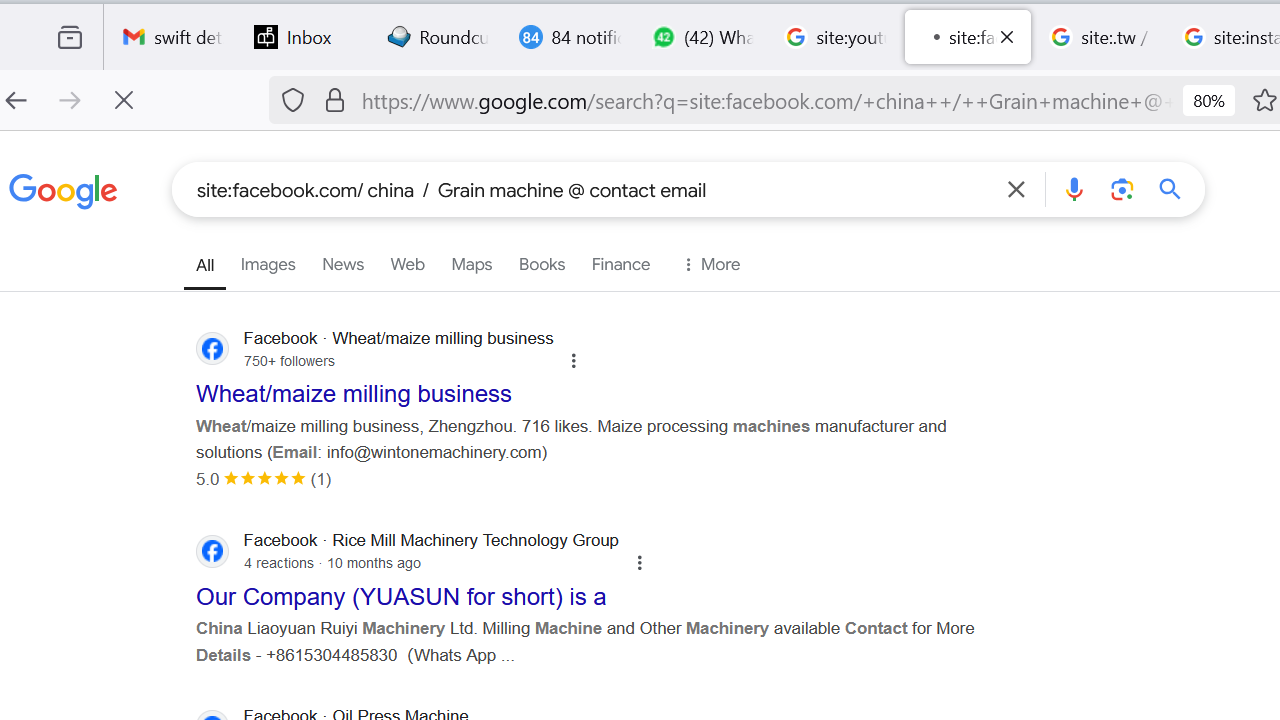
Nigerian hackers utilize Google dorking techniques to harvest email addresses. These cybercriminals search for emails on social media platforms using specific Google dork queries. Below are some of the Google dorks they employ.
site:youtube.com/ malaysia /sales / Farm truck@ contact email
site:facebook.com/china / Grain machine @ contact email
The first search allows the hacker to find Malaysian businesses with email addresses on YouTube. The second query targets Chinese grain machine businesses with contact emails on Facebook.
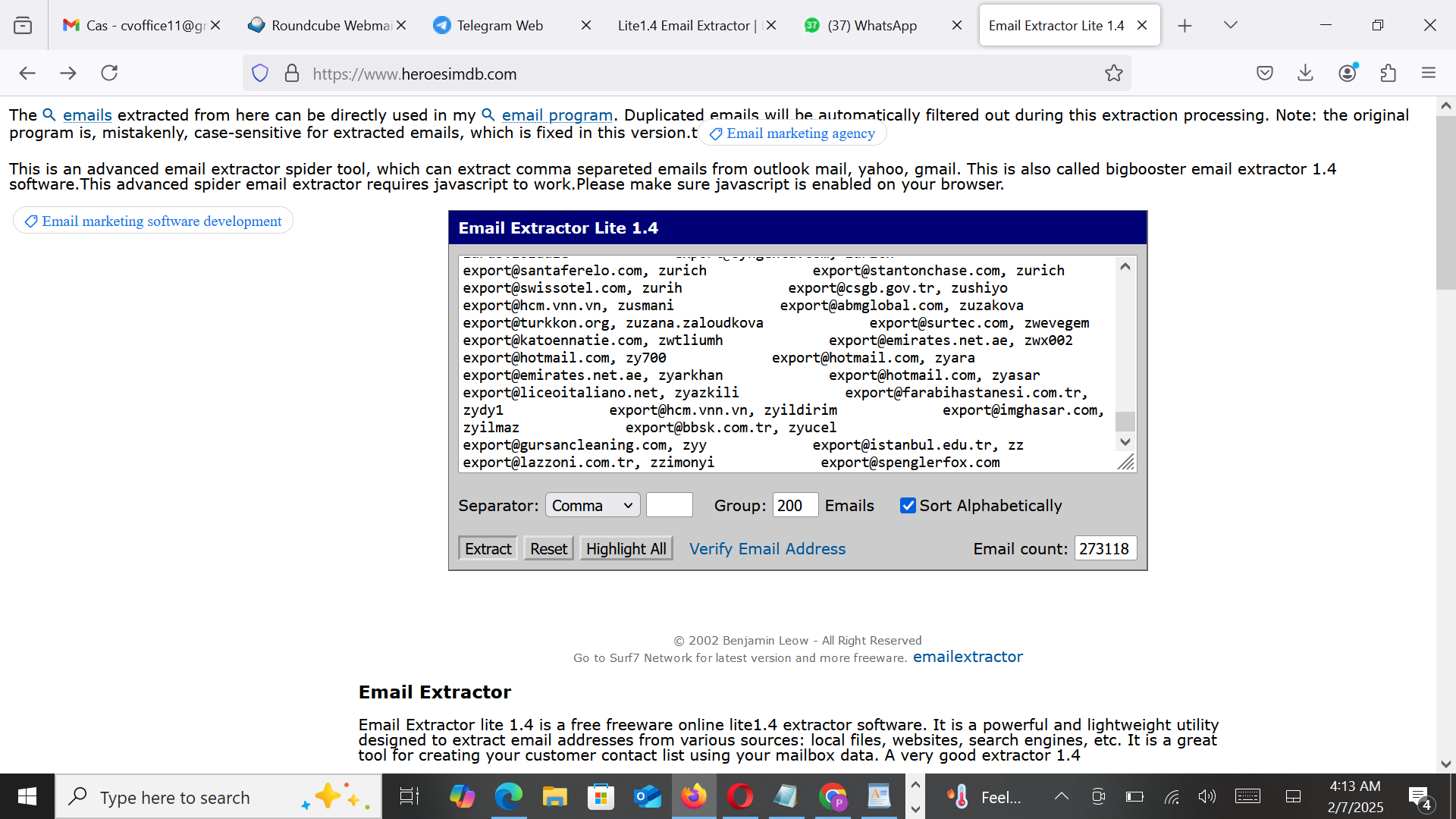
Using the results, the cybercriminal copied and pasted the content into heroesimdb[.]com to extract email addresses. The following image shows this process in action.
Analysis
What we put online can be used against us. That’s why it’s crucial to understand what is exposed on the internet.
- Phone numbers can be exploited for social engineering attacks.
- Email addresses can be targeted with phishing links, malware campaigns, or scams.
Take extra precautions with your external assets—awareness is the first line of defense.
Email Configuration
Once a sizable list of email addresses is collected, the next step is setting up a campaign to distribute the malware effectively:
- Creating a Spoofed Domain – Registering a domain that mimics legitimate businesses to improve credibility.
- Configuring a Mail Server or Using Bulletproof Hosting – Ensuring bulk email delivery without getting blocked.
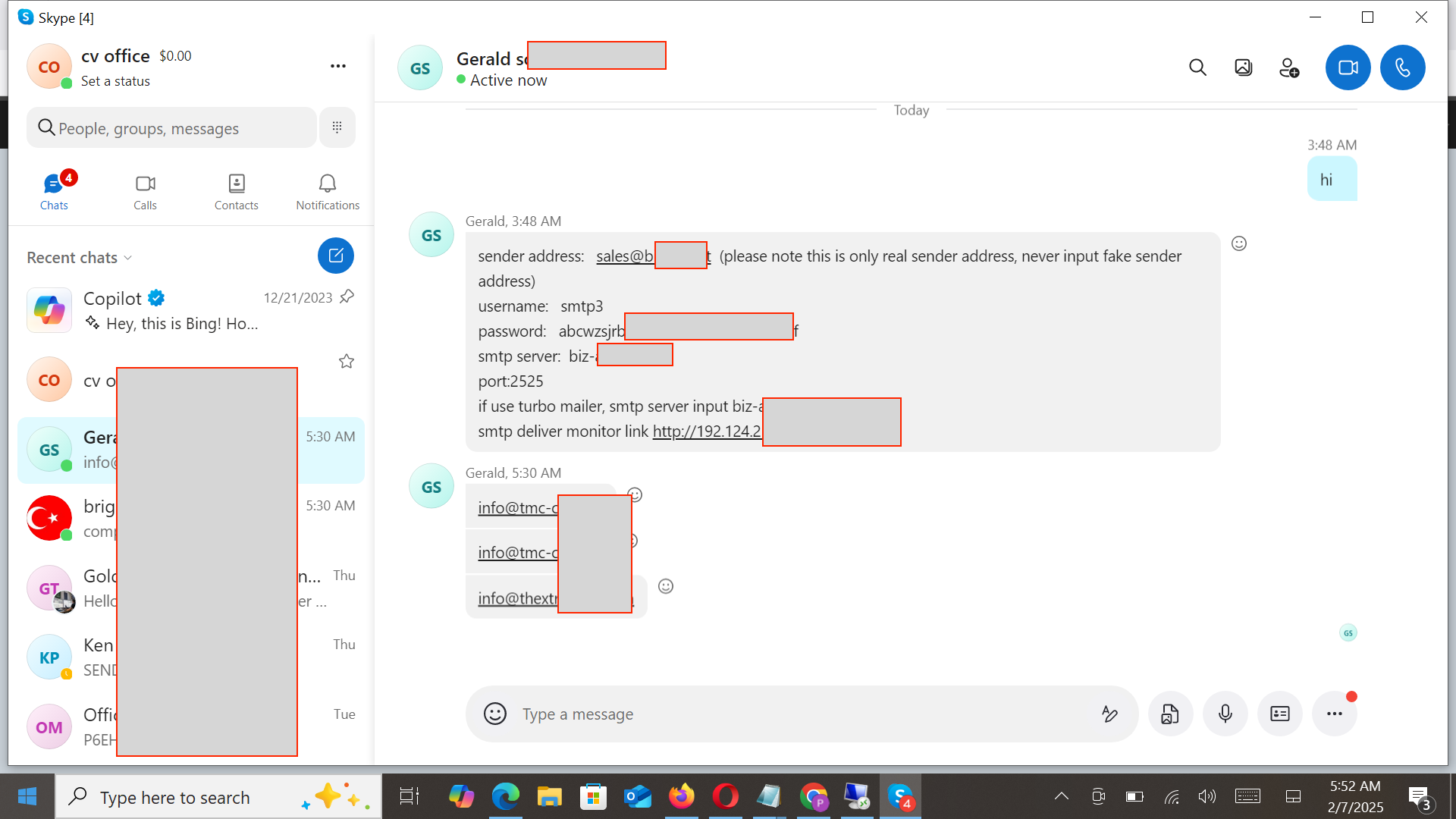
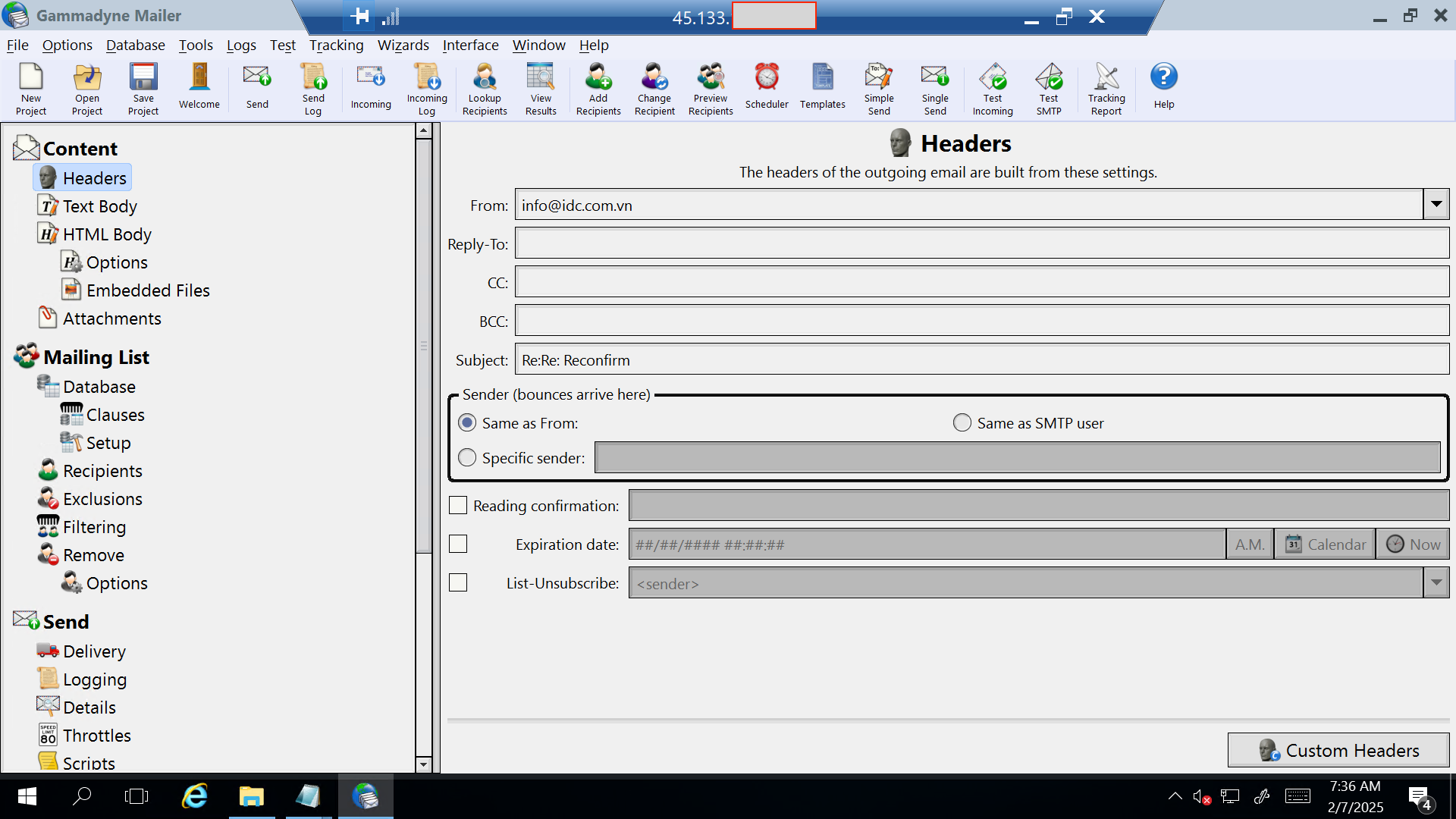
To obtain a domain for sending emails, the cybercriminal acquired an account from a user named Gerald on Skype. Gerald provided the cybercriminal with the email account, SMTP server information, and login credentials.
The following image shows their communication.
To execute the email campaign, the cybercriminal used Gammadyne Mailer, a software designed for automating business email marketing and other email operations.
Below is the software’s description from its official page.
“All you need is a mail server to relay the emails, and these can be rented for a few dollars per month. Or you can simply use the mail server that comes with your website. Gammadyne Mailer is the only practical solution for large mailing lists.”
The following images shows how the cybercriminal configures Gammadyne.
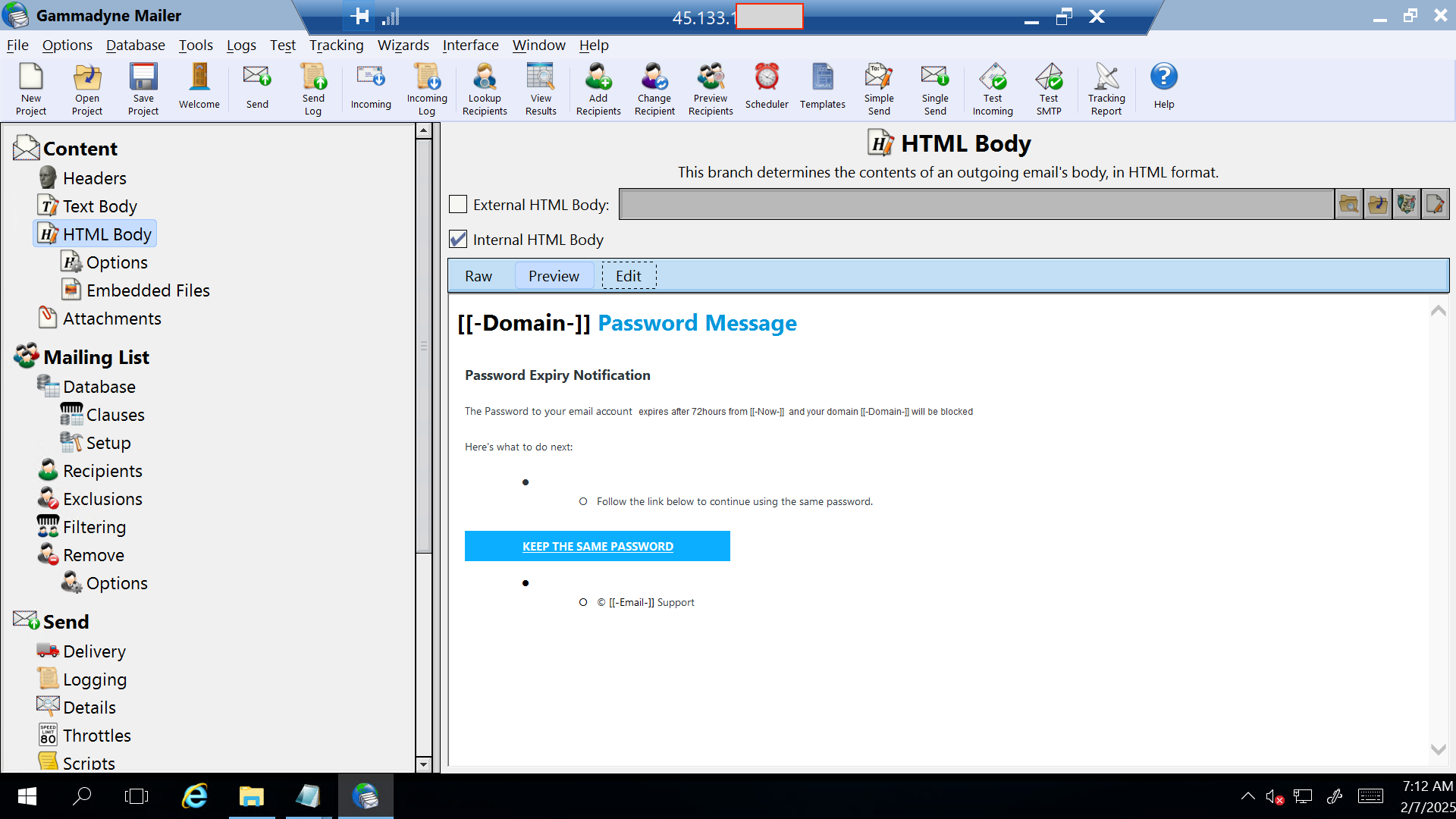
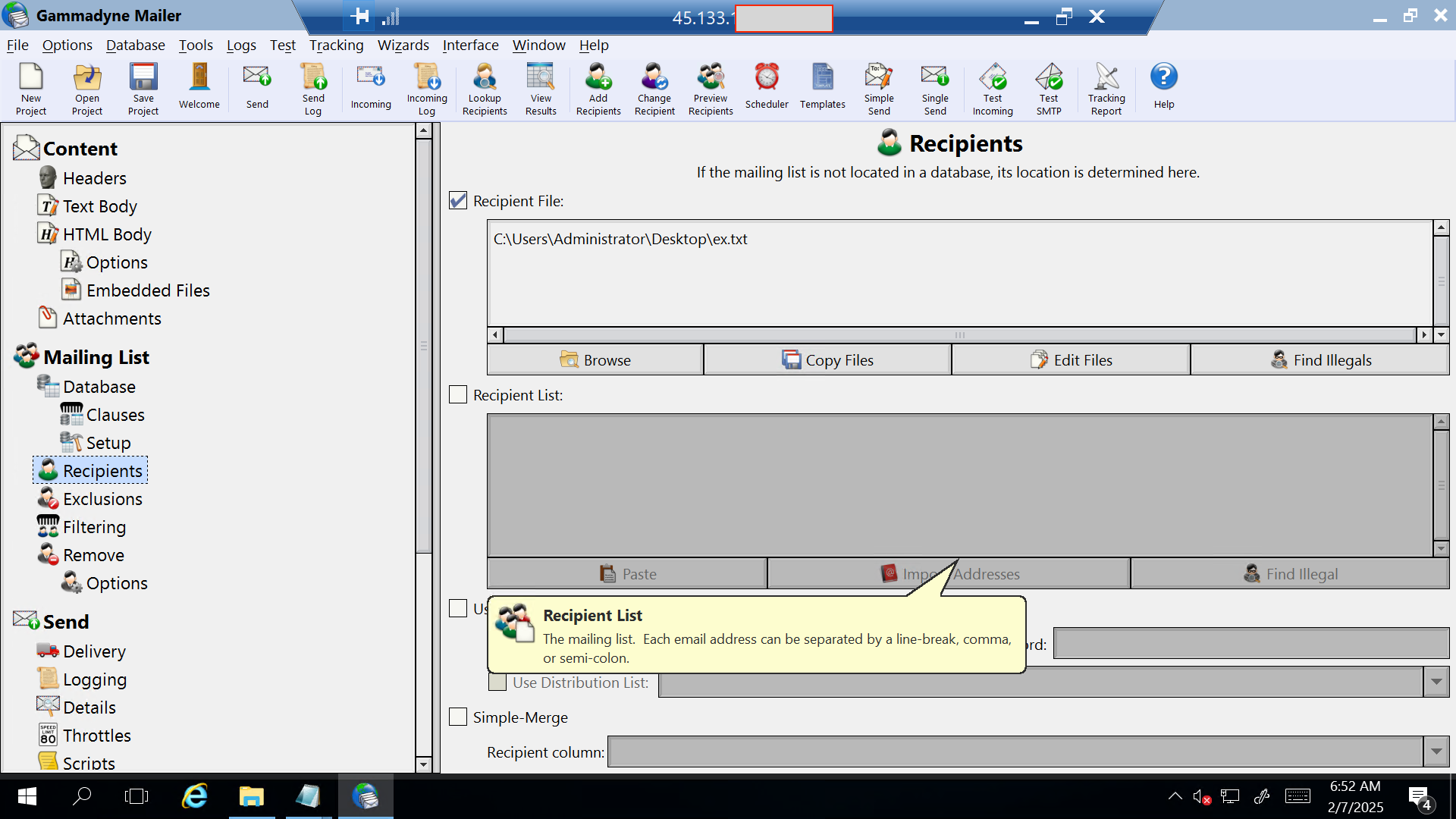
Analysis
Based on the email accounts provided by Gerald, the domain is a well-established one that has been registered for some time. This potentially indicates that the domain was compromised and sold to cybercriminals for spam campaigns.
An additional interesting detail in the image is that the cybercriminal used another server running Gammadyne Mailer, accessed via RDP. This extra layer adds a level of obfuscation, making it slightly harder to trace the cybercriminal in case of an investigation.
Email Message (ChatGPT)
To run a successful campaign, the email message must be convincing, making the quality of the crafted message crucial. Many cybercriminals specialize in this aspect of the scam, creating and selling scam letters to other criminals.
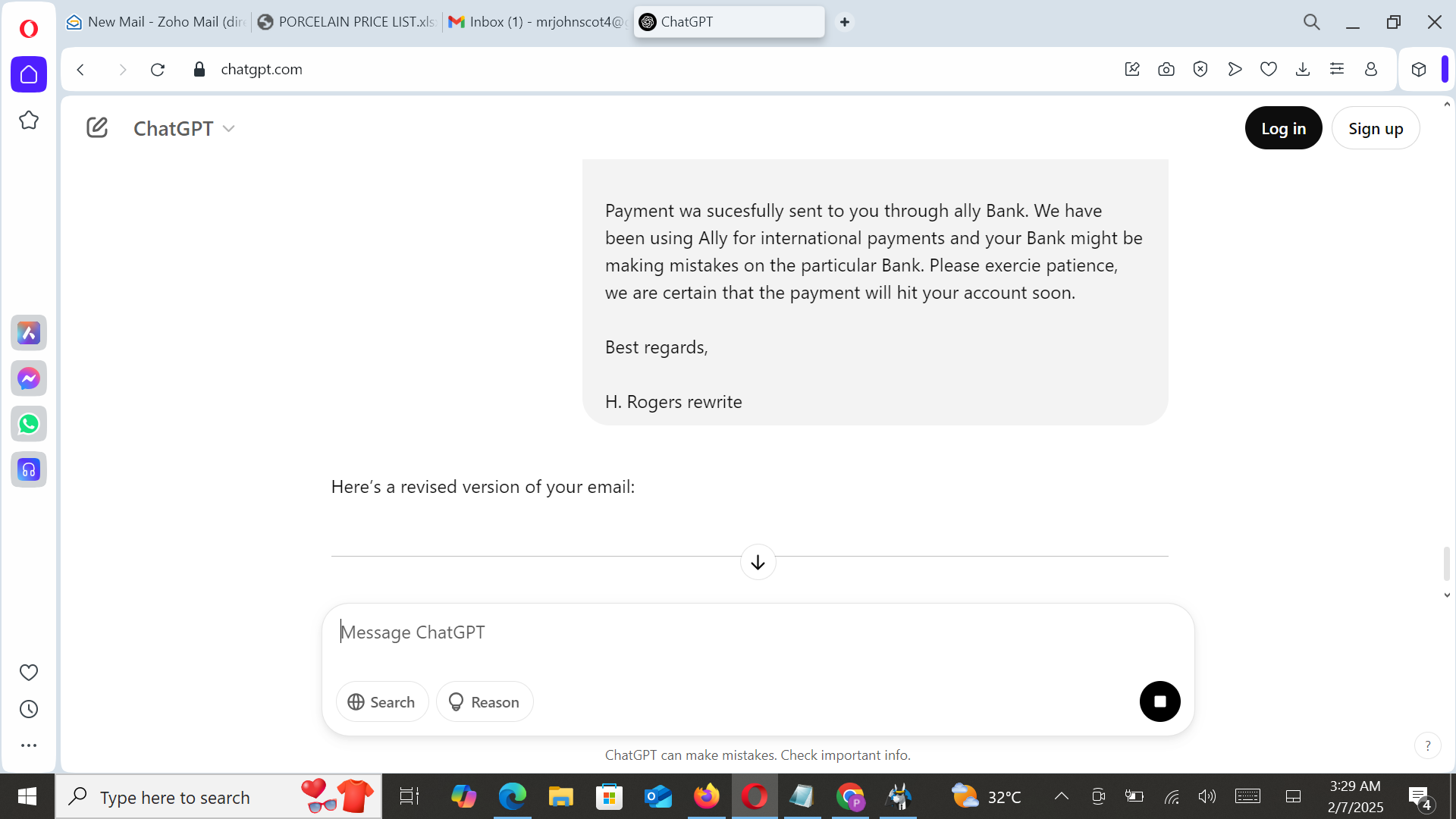
With the introduction of ChatGPT, security researchers feared that cybercriminals would leverage AI to craft more convincing email messages. The following images show how this cybercriminal used ChatGPT to generate phishing messages for a malware campaign.
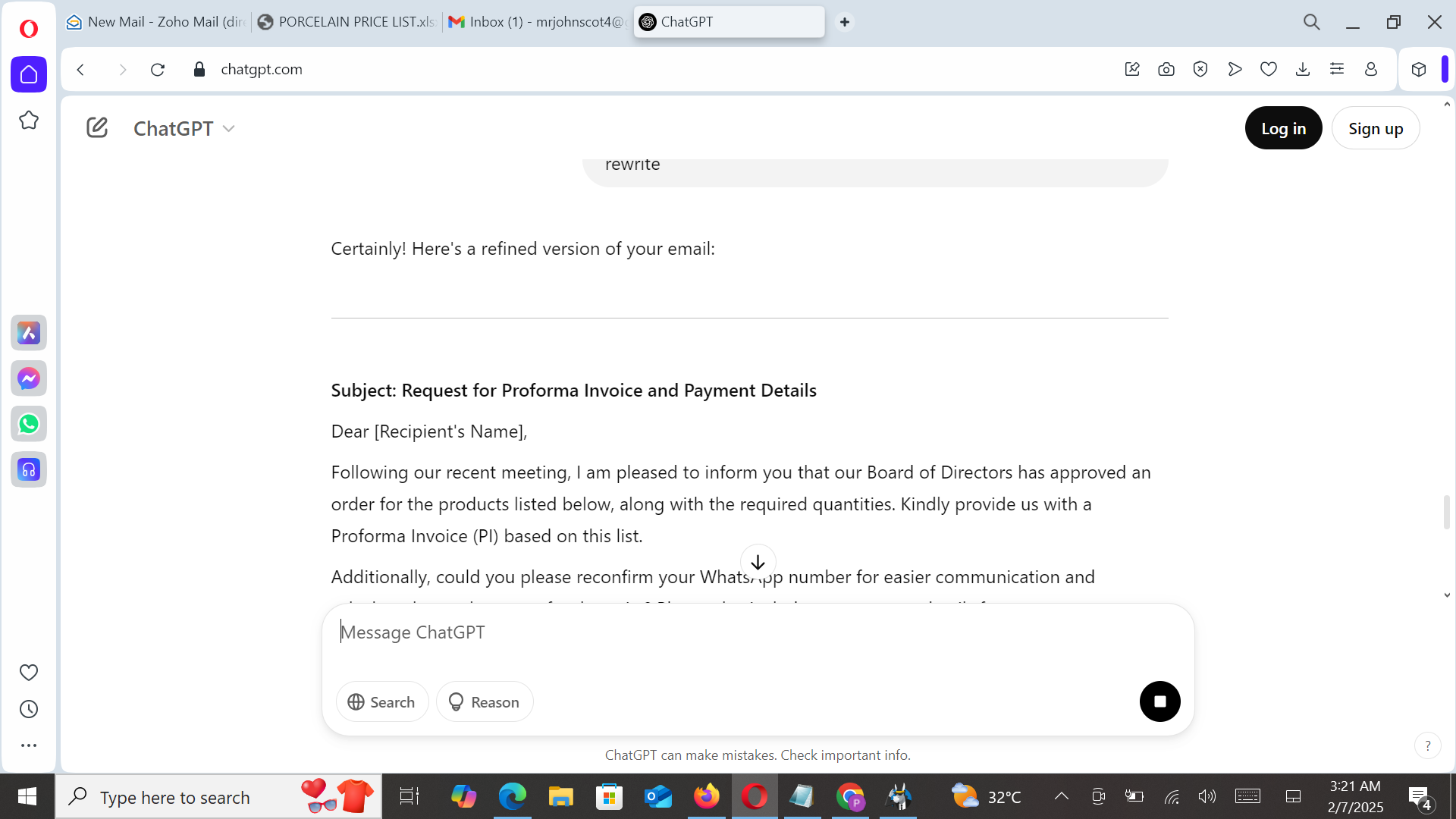
Email Campaign
Once the email campaign is configured, the next step is to launch the attack. The following image shows how the cybercriminal executes their campaign.
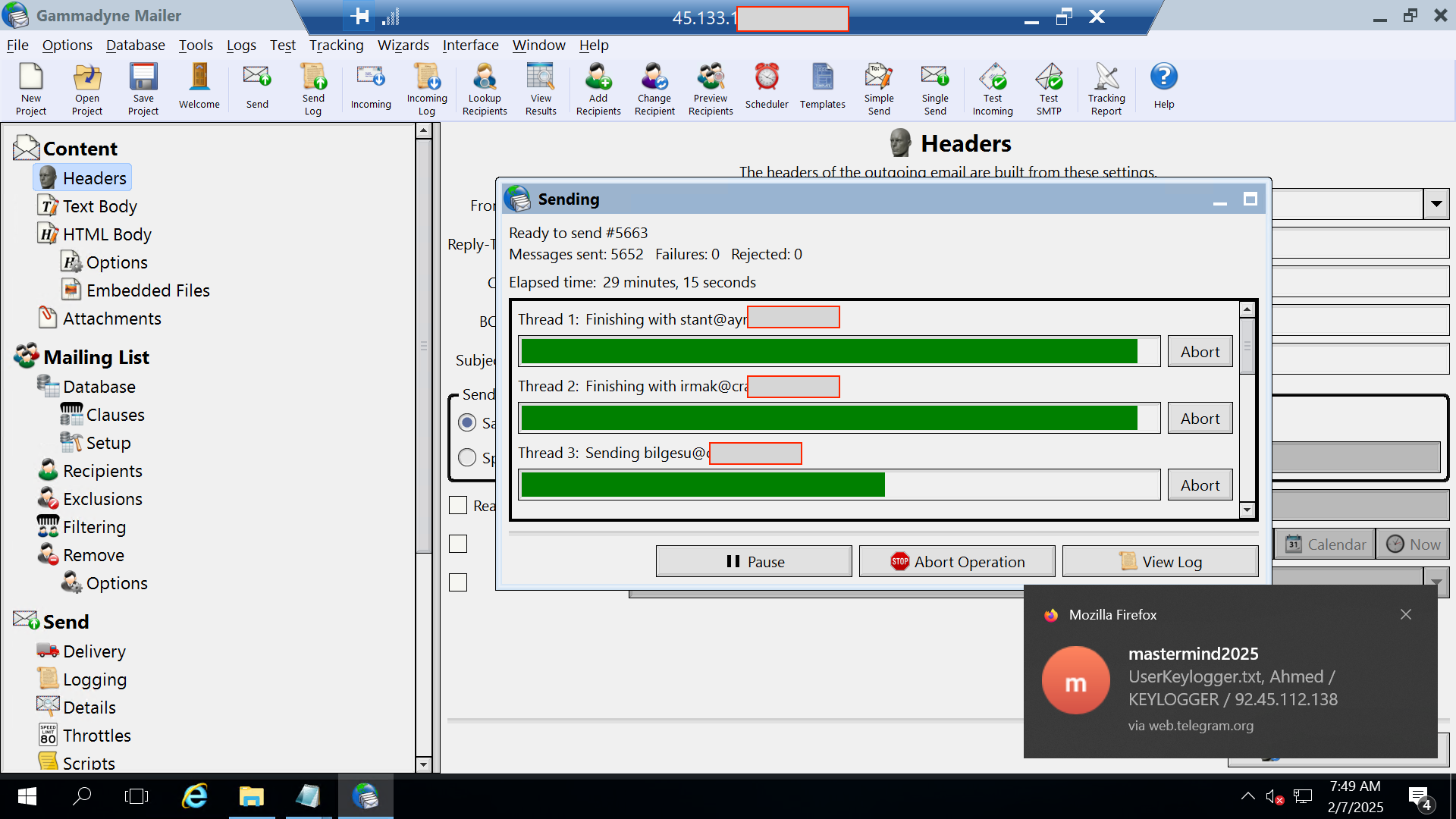
As seen on the scammer’s desktop, they are running multiple campaigns in parallel. In the bottom right, it shows that at least one user has been infected with the malware, and the scammer is actively receiving stolen data (malware logs).
The following image shows the cybercriminal’s desktop with their webmail open, displaying the email campaign sent to the target.
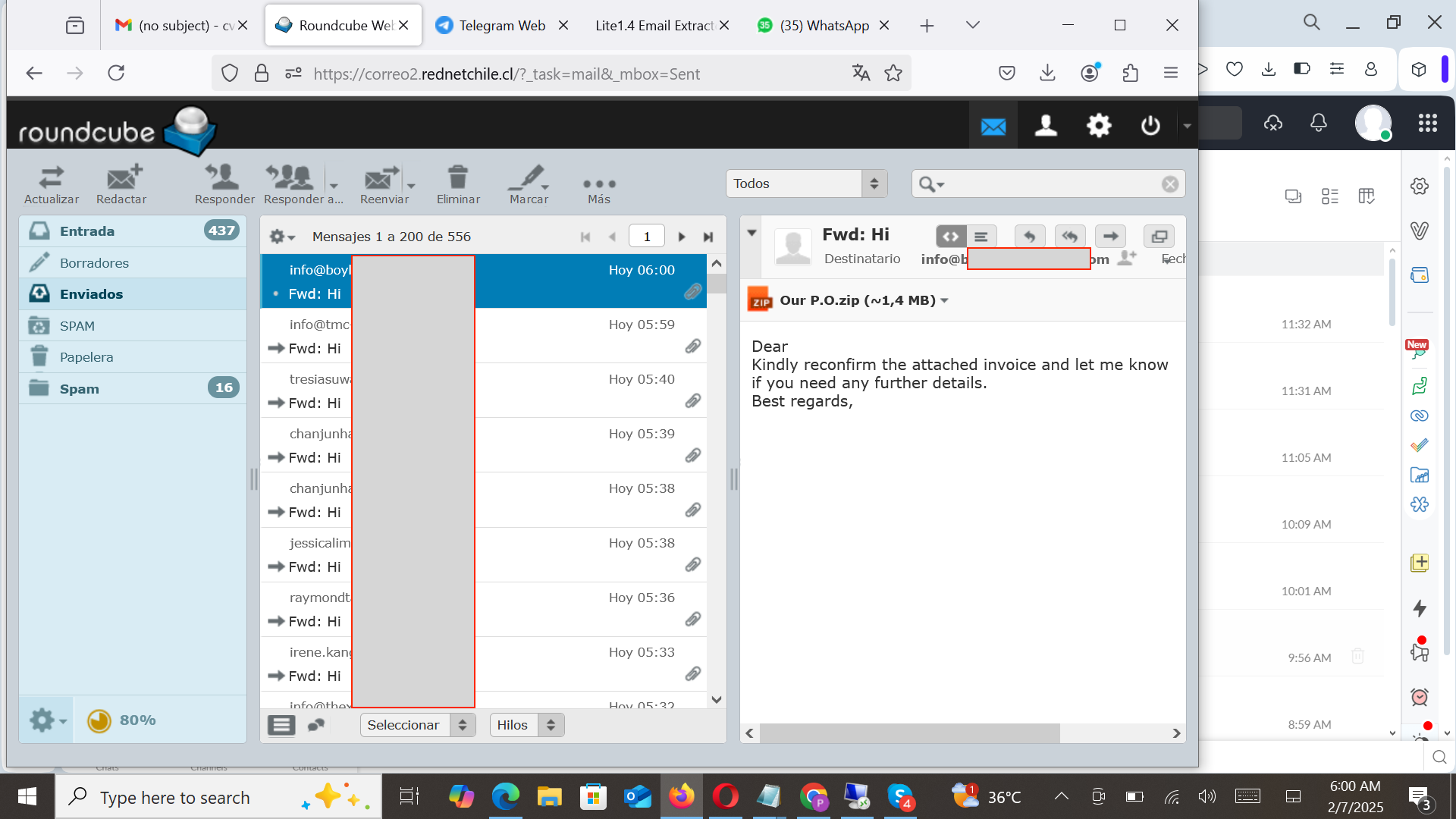
Analysis
The image shows that the cybercriminal was able to send nearly 6,000 emails within 30 minutes. While this may not seem high, it’s a strategy to avoid triggering detection. Additionally, the campaign’s effectiveness is evident, as the cybercriminal managed to compromise a few victims.
Campaign Email
We obtained an email from the cybercriminal. Below is one of the emails they sent to a user.
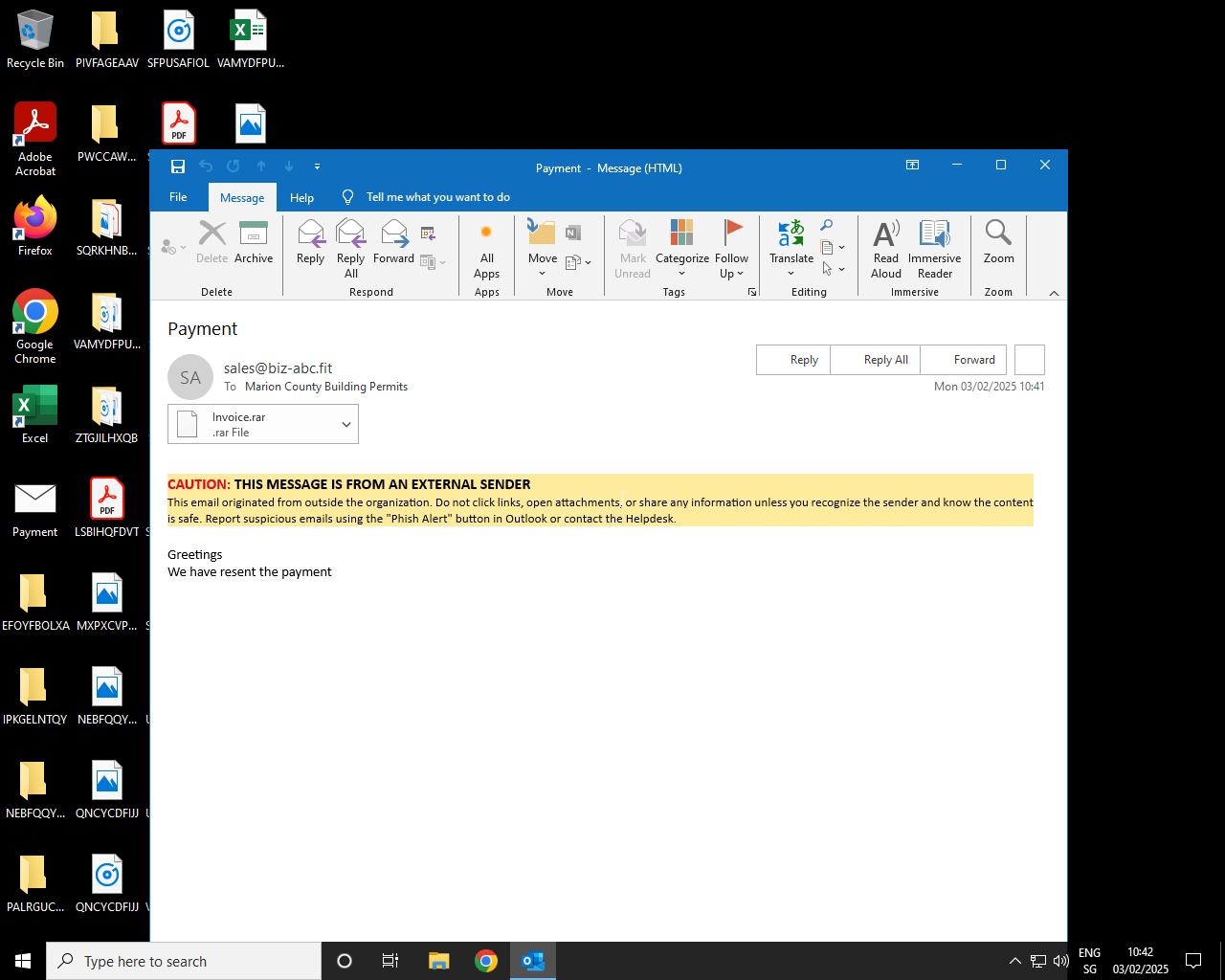
Sender: sales@biz-abc.fit
Subject: Payment
The attachment has the following characteristics:
File Name: Invoice.rar
MD5: 65975cc3faf23bfc6a2e0cff91d9c39f
SHA1: 4d69b63226374a63669550515c7010de57ae34de
SHA256: 9330115e568582d005e19dbedb11d2f08ea7e6492a41a8739f730bf20672b3f9
File Size: 652,869 Byte
File Type: Rar
The attachment contains a Windows executable with the following characteristics:
File Name: Factura.exe
MD5: 4fdfab8f4aaae7d90319a9a5cbc0f8ad
SHA1: a8319c665e8cc5987277a5d71feeb086008672cd
SHA256: bae3ada1c2bdcabc3ebd059ee2715a975237118be145301a0257da5fa84288ca
File Size: 675,944 Bytes
File Type: Exe
From various sandboxes, the executable is classified as Redline malware stealer. However, based on the captured data, the malware is identified as XLogger.
Upon execution, the executable runs a PowerShell script that decrypts the payload and injects the malware into a Windows service. The malware then captures credentials from the machine and sends the stolen data to the cybercriminal’s Telegram channel.
Conclusion
Nigerian hackers have refined their cybercrime operations, making malware campaigns more sophisticated. However, as demonstrated by this cybercriminal, their process remains simple yet effective. This highlights the daily challenges we face, as users, unaware of the security risks, continue to trust malicious senders and end up compromising themselves.
I hope this sheds light on the cybercriminal’s process and helps us train users more effectively while developing stronger countermeasures.





