A company recently approached us to reverse engineer a decryption tool that was used to decrypt a file that had been encrypted by ransomware, and which they had paid the hacker to unlock. However, the tool was only able to decrypt one file and the hacker demanded further payment to decrypt additional files. This situation highlights a growing concern for victims of ransomware attacks: Do their problems go away once they’ve paid the ransom? The two cases that follow below will show that paying a ransom often fails to solve a victim’s problems because there is no honor among thieves; moreover, perpetrators are financially motivated to not hold up their end of the bargain. From our experience with clients, rather than succumbing to a ransom demand, it is of utmost importance for a victim to contact a cybersecurity expert to come up with potential solutions to help mitigate the impact of such attacks.
Case 1
A company fell victim to a Samas ransomware attack and decided to pay the ransom to the hacker in order to restore access to three of their servers. However, after receiving the decryption tools from the hacker they discovered that the tools were ineffective. Despite attempts to seek support from the hacker, they received no cooperation. The victim was left with no other option but to turn to the security community for assistance, and posted their plea for help on samas ransomware help (reddit.com). One of our researchers saw the post and reached out to the victim to assist them.
The initial step was to determine why the decryption tool provided by the hacker failed to work. With access to both the ransomware and the decryption tool, we were able to reverse engineer them and identify a bug in the decryption tool. We rectified the issue and provided the corrected decryption tool to the victim, enabling them to successfully decrypt all the files on their servers and restore their services. To assist other potential victims, we shared the corrected tool on bleepingcomputer.com.
Case 2
A company was targeted in an unknown ransomware attack and chose to pay the ransom demanded by the hacker to restore access to their servers. Unfortunately, the decryption tool provided by the hacker was only effective in decrypting a single file. Moreover, the hacker demanded additional payments to decrypt the rest of the encrypted files.
In the following analysis, we outline our reverse engineering process for the decryption tool and how we were able to develop a new decryption tool capable of decrypting the remaining files.
Ransomware Family:
At the time of our analysis, we were not able to identify the ransomware family. The encrypted file name has the following naming convention.
[original filename].key-[unique #1].0x[unique #2]
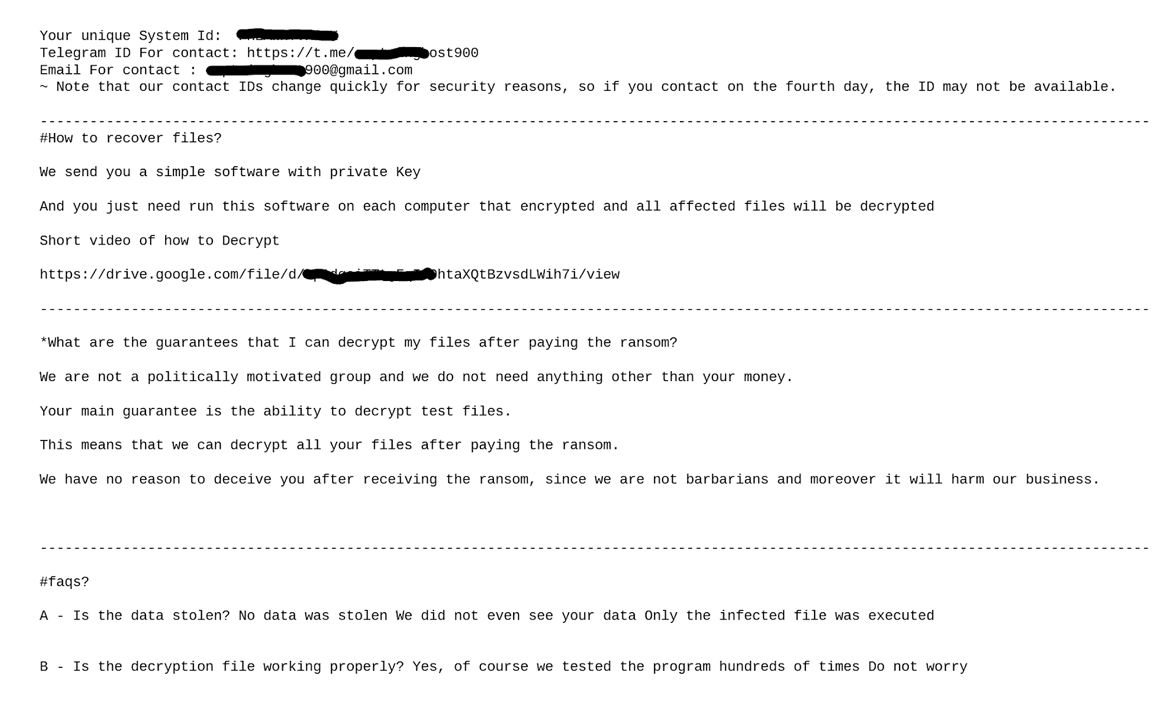
The ransom notes left by the ransomware are presented below.
Ransomware Decryption Overview
The decryption tool is implemented as a Golang application that scans all drives for files with the hardcoded extension associated with the ransomware. The tool pairs each encrypted file with its corresponding system ID, which is specified in the ransom note. The system id (‘unique #1’) is then used as the password to decrypt the file.
Below we see an overview of the ransomware decryption process.

After reverse engineering the decryption tool we discovered that the ransomware uses the AES encryption algorithm to encrypt each file with a unique password; the password itself is generated using PDKDF2 algorithm derived from the system ID. Additionally, each password/system ID is paired with a unique hexadecimal string and is referred to as ‘unique #2’.
Since the ransomware uses a unique password to encrypt each file, hackers are financially motivated to demand payment for each individual file, making it a costly endeavor for the victim. However, by reverse engineering the ransomware tools we were able to develop a decryption tool capable of decrypting all of the encrypted files without the need to pay the ransom.
Summary
Ransomware attacks are increasing in numbers and sophistication. More troublesome is the fact that many victims choose to pay the extortion in the belief that the perpetrators will act in good faith and help them regain access to sensitive files. Our experience has shown, however, that attackers often do not fulfill their promise to help; more specifically, the tool(s) they provide don’t work or are limited in scope. Consequently, many victims are forced to give additional payments for further remediation.
Given that cybercriminals are financially incentivized to not hold up their end of the bargain, paying a ransom only serves to reward their criminal objectives. Instead, it is recommended that victims seek out other solutions such as restoring from backups or seeking assistance from cybersecurity experts to avoid further financial and data loss.