In an era characterized by rapid technological advancements, the cyber threat and fraud landscape is evolving at an unprecedented pace. As organizations aim to outpace sophisticated adversaries, the traditional concept of Security Operations Centers (SOCs) must undergo rapid transformation.
The traditional SOC and Fraud
In financial institutions, security groups are typically structured to address various aspects of cybersecurity and fraud prevention. While specific names and roles may vary between organizations, common security groups include:
Security Operations Center (SOC)
The SOC is in the cyber security department and is responsible for monitoring and responding to security incidents. It involves security analysts who analyze and respond to alerts generated by security systems.
Fraud Prevention Team
This team is in the fraud department and focuses specifically on detecting and preventing fraud. It may include fraud analysts, investigators, and specialists in areas such as identity theft, payment fraud, and account takeover.
Incident Response Team
This group is in the cyber security department and is tasked with developing and implementing plans to respond to security incidents. Their goal is to minimize damage, contain threats, and restore normal operations.
Risk Management Team
The risk management team assesses and manages the overall risk posture of the financial institution. This includes identifying potential risks, implementing risk mitigation strategies, and ensuring compliance with regulations.
Information Security Team
This team is responsible for the overall information security of the organization. It includes specialists in areas such as network security, application security, and data protection.
Security Architecture Team
Security architects design and implement the organization’s security infrastructure. They focus on creating a secure and resilient architecture to protect against cyber threats.
Compliance and Governance Team
This team ensures that the organization complies with relevant regulations and industry standards. They also establish and enforce security policies and procedures.
Threat Intelligence Team
This team is in the cyber security department and responsible for gathering and analyzing intelligence related to emerging threats and vulnerabilities. They provide proactive insights to enhance the organization’s security posture.
Cybersecurity Awareness and Training Team
This group is responsible for educating employees about cybersecurity best practices and ensuring that staff members are aware of the latest threats and how to mitigate them.
IT Security Operations Team
This team manages the day-to-day security operations, including configuring and monitoring security systems, conducting regular security audits, and responding to routine incidents.
These groups are often in two or more departments, for the operational group, it’s often the cyber security department and fraud department.
Common Challenges
Given the distinct responsibilities of each group and the numerous tasks they handle on a day-to-day basis, the siloed responsibility between security groups and fraud groups in an organization can result in various issues that impede the overall effectiveness of cybersecurity and fraud prevention efforts. Some common issues associated with siloed responsibilities include:
Limited Information Sharing
When security and fraud prevention teams operate in silos, there is often limited sharing of critical information. This lack of communication can result in missed opportunities to correlate security incidents with potential fraudulent activities.
Delayed Incident Response
Siloed responsibility can lead to delays in incident response. Security incidents that may be initially identified by the security team might not be promptly communicated to the fraud prevention team, resulting in delayed or inadequate responses to emerging threats.
Ineffective Threat Detection
The failure to integrate security and fraud detection tools and processes can result in ineffective threat detection. Cybercriminals often exploit vulnerabilities that traverse traditional security and fraud boundaries, making it crucial for both teams to collaborate.
Fraud Attacks Flow
In today’s fraud landscape, fraudulent activities often involve multiple stages encompassing both the Darkweb and Clearweb. For example, for a cyber criminal to steal money through ACH transfer using phishing as the attack vector, they would follow the following steps:
Target Identification
Identify potential targets for a specific financial institution. The criminal compiles a list of email addresses obtained through a breach, such as the Target breach or Bidencash dump, or purchases the leads email from a vendor like Figure 1.
Scam Page Setup
The cybercriminal sets up a phishing page and sends emails to the targets, aiming for them to click on the URL and enter their credentials on the fraudulent webpage.
Capture
Once the target submits their credentials, the cybercriminal utilizes the obtained information to take over the account.
Account Takeover
With control established, the criminal adds a bank account to the compromised account and executes a transfer through ACH.
This attack encompasses multiple activities requires both the Security Operations Centers and Fraud groups to effectively coordinate. However, the lack of communication and siloed responsibility may lead to delayed detection of the attack, potentially hindering effective response measures.
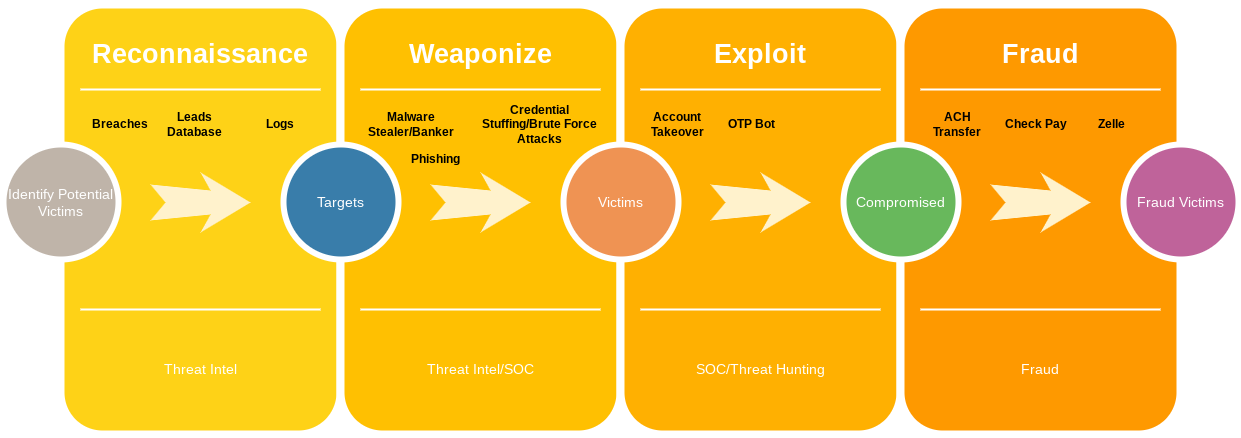
The Fraud team typically becomes involved at the final states of the cyber attack, making it challenging to intervene in a timely manner. Consequently, there’s a risk that the organization may transfer money out, too late to prevent or reverse the transaction.
How can we stay ahead?
Cyber-Fraud Fusion Operation
In the attack flow below, cyber attacks generate signals at various stages. Leveraging additional technologies at different points creates an early warning system. The integration of the Fraud team into the cybersecurity process empowers the organization to stay ahead of potential threats.
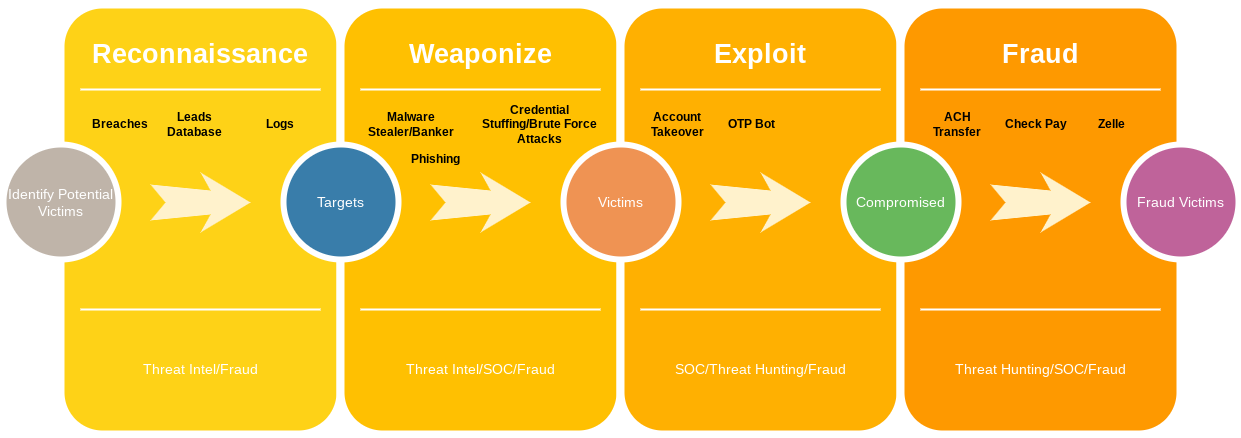
Elevating the traditional fraud team’s understanding of cybersecurity equips them to navigate the digital terrain where many new fraud instances originate. By actively participating in the early stages of the detection process, the fraud team gains the ability to identify and prepare before an attack takes place. Furthermore, they can detect and remediate certain threats even before they fully materialize. Amidst an ongoing attack, some assailants emit signals that aid the fraud team in identifying potential victims, enhancing the team’s proactive capabilities.
As demonstrated in the example, comprehending the attack vectors and leveraging cyber intelligence empowers the fraud team to counteract attacks and proactively detect threats, ultimately reducing instances of fraud.
Conclusion
Cybercrime is in a constant state of evolution, with the fraud landscape undergoing significant changes in recent years. Traditional security measures are losing effectiveness, necessitating a collective effort from every team to increase organizational protection. In the dynamic realm of cybersecurity and fraud prevention, collaboration, communication, and a proactive approach are indispensable for staying ahead of emerging threats. Integrating the cybersecurity and fraud teams, the Cyber Fraud Fusion Operation has the potential to revolutionize our approach to combating cybercrime.





