In the dark web landscape, numerous illicit activities take place, ranging from the sale of compromised accounts to the dissemination of fraud techniques. This landscape is in a constant state of expansion, with criminals even offering real-time customer support to facilitate fraudsters, along with the development of fully automated systems for account takeover. Cybercriminals actively share substantial amounts of data on dark web forums and private channels, primarily on Telegram chat platforms. This data includes compromised credentials, account checking software, phishkits, and logs of malware stealers. As a result, these circumstances present an open opportunity for criminals to exploit.
This article examines the tactics employed by cybercriminals to distribute malware droppers via malware stealer logs within the dark web community. These logs are then shared with other cybercriminals. When an unsuspecting cybercriminal downloads and opens the compromised file, they unknowingly infect themselves with the Shinobu clipper malware. Subsequently, the malware takes control of their crypto address and substitutes it with the cybercriminal’s own address. As a result, any cryptocurrency sent by the infected user ends up in the possession of the malicious actor, instead of reaching its intended recipient. The cumulative amount stolen by these cybercriminals is estimated to be around $2,579.56.
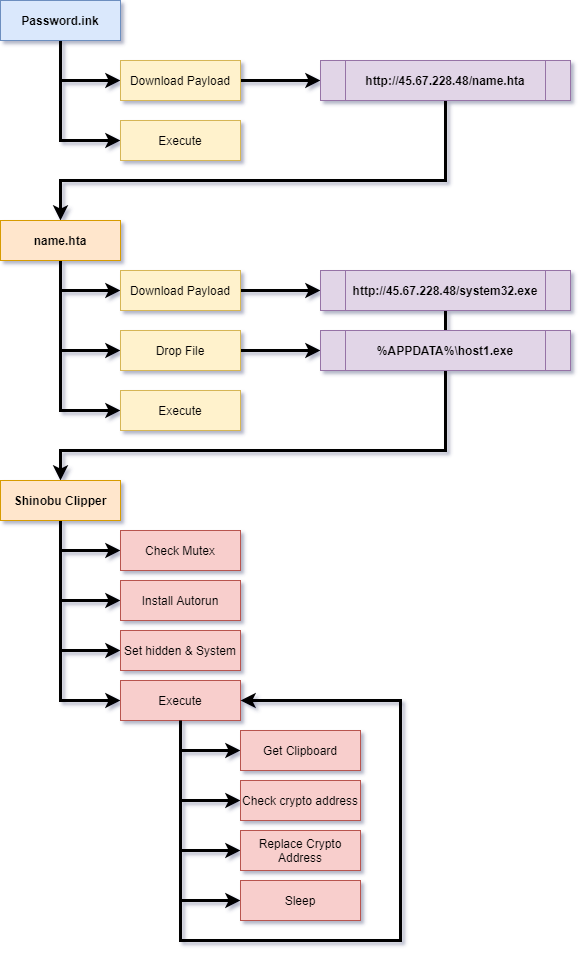
Dropper Overview
During our investigation of the dark web, we came across a peculiar sample of a malware stealer’s log file that deviated from the typical Redline log file structure. Instead of containing the expected ‘Passwords.txt’ file, this log sample included a file named ‘Passwords.lnk,’ which is a Microsoft Windows shortcut file. At first glance, the file appears to be a regular shortcut file under the standard Windows operating system. However, once a user clicks and opens this file, it triggers the execution of a PowerShell script, initializing the infection process of the Shinobu stealer malware.
Below we see the folder containing the stealers’ log, along with the presence of the malware dropper.
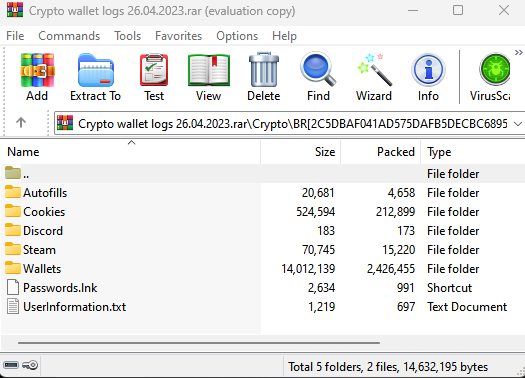
Dropper File
The dropper disguises itself as a ‘Passwords.txt’ file within the Redline stealer logs. However, it is actually a Microsoft Windows shortcut file. When the user opens this file, it triggers the execution of a PowerShell script. Here are the properties of the drop file:
Filename: Password.lnk
MD5: 11829e5c4f32c9312b794085e3bec48f
SHA1: 95897923fd6136e30c7e04212bffedbbbcdf9f8d
SHA256: 2d9f0179595ba0a74803c5d3446a1d63c0769f2356632ee55ba2095b6fbfcd1b
Size: 2634
FileType: Shortcut
The powershell is stored in the target properties of the shortcut as shown below.

Upon execution, the PowerShell script decodes the URL, proceeds to download the second-stage payload, and subsequently executes another PowerShell script. Here is the URL of the second stage:
hxxp://45.67.228[.]48/name.hta
Obfuscated JavaScript
The second stage of the attack involves an MS Windows HTML application that contains obfuscated JavaScript. The JavaScript within the application is responsible for decoding the PowerShell script and executing it. The PowerShell script, in turn, downloads the final payload, which is then dropped into the %APPDATA% folder and executed. Here are the properties of the HTML application:
File Name: name.hta
MD5: 1e34ba7ca79958f904b2fcaebe9532e2
SHA1: b7bb882788c32b13c8456fef4161b6dda4e3e1bd
SHA256: 40f6211b3e50058e11c5d8969d5c0a0bb8ed87c2844cdf7df56cd0b798429655
Size: 107992
File Type: HTML Application
Below is the URL of the final payload.
hxxp://45.67.228[.]48/system32.exe
The final payload has the following properties:
File name: system32.exe
MD5: 925a33d545b81303f95076ca52264c0a
SHA1: 81674cc002e4c98d59480e6365adaa4c4733e170
SHA256: 55e1190786eb6c0a8c69827849af9b21ec8ece3936622f9c45ea074f4ee39691
Size: 134144
File extension: exe
File MIME type: application/x-msdownload
The final payload consists of a packed .NET application that performs decryption and loads the Shinobu clipper into the system’s memory. The packed .NET application is designed to obfuscate its code and make analysis and detection more challenging. Once executed, it decrypts the necessary components and proceeds to load the Shinobu clipper, which is a malicious software capable of hijacking cryptocurrency addresses.
Shinobu Clipper
Shinobu Clipper is a crypto hijacker stealer designed to monitor the clipboard activity of an infected system. Its main functionality revolves around constantly scanning the clipboard for any data that resembles a cryptocurrency address. Upon identifying a potential cryptocurrency address, the malware proceeds to replace it with the attacker’s own address.
When the victim attempts to paste the crypto currency address into the intended destination, they unknowingly paste the cyber criminal’s crypto currency address instead. Consequently, any cryptocurrency sent by the victim will be redirected to the cyber criminal’s address, resulting in the loss of funds for the victim.
You can analyze the source code of the malware in the following github: https://github.com/swagkarna/ShinobuClipper
Malware Crypto Address
The Shinobu Clipper malware is capable of targeting multiple types of cryptocurrencies. Here is a list of supported cryptocurrencies, the corresponding addresses the malware uses for substitution, and the total amount of cryptocurrency the malware has received from its victims:
Conclusion
With the expansion of the dark web onto the surface web, real-time chat services, and social media platforms, it has become easier for criminals to engage in the world of crimeware and access valuable data. There’s no honor among thieves as demonstrated by this research.
In certain instances, cyber criminals exploit less knowledgeable criminals by implanting fake data with the intention of infecting them. Further investigation reveals that the malware used in these activities is also found within various criminal software tools. These tools, such as account checkers, log validators, and other utilities commonly shared on the dark web, are frequently utilized by fraudsters.
It is essential to exercise caution and implement robust security measures when operating within these environments, as the risk of encountering malware, fake data, and deceptive tactics remains prevalent.
DarkArmor’s fraud intelligence platform offers organizations real-time actionable data to help them protect themselves and their assets. For more information, please contact us or book an appointment on our contact page. We are committed to assisting you in enhancing your security measures and safeguarding against fraudulent activities.