The campaign primarily targets small and mid-sized businesses, advertising agencies, and social-media managers who use Meta Ads for their marketing.
For these victims, losing access isn’t just an inconvenience — it means losing customers, visibility, and revenue.
Once an account is compromised, the attacker:
- Changes billing information, adding stolen or virtual cards.
- Launches scam ads promoting fake crypto or investment platforms.
- Removes legitimate administrators, taking full control.
Even a single breach can cause significant financial and reputational harm.
The operation’s global reach suggests a sophisticated and disciplined criminal enterprise.
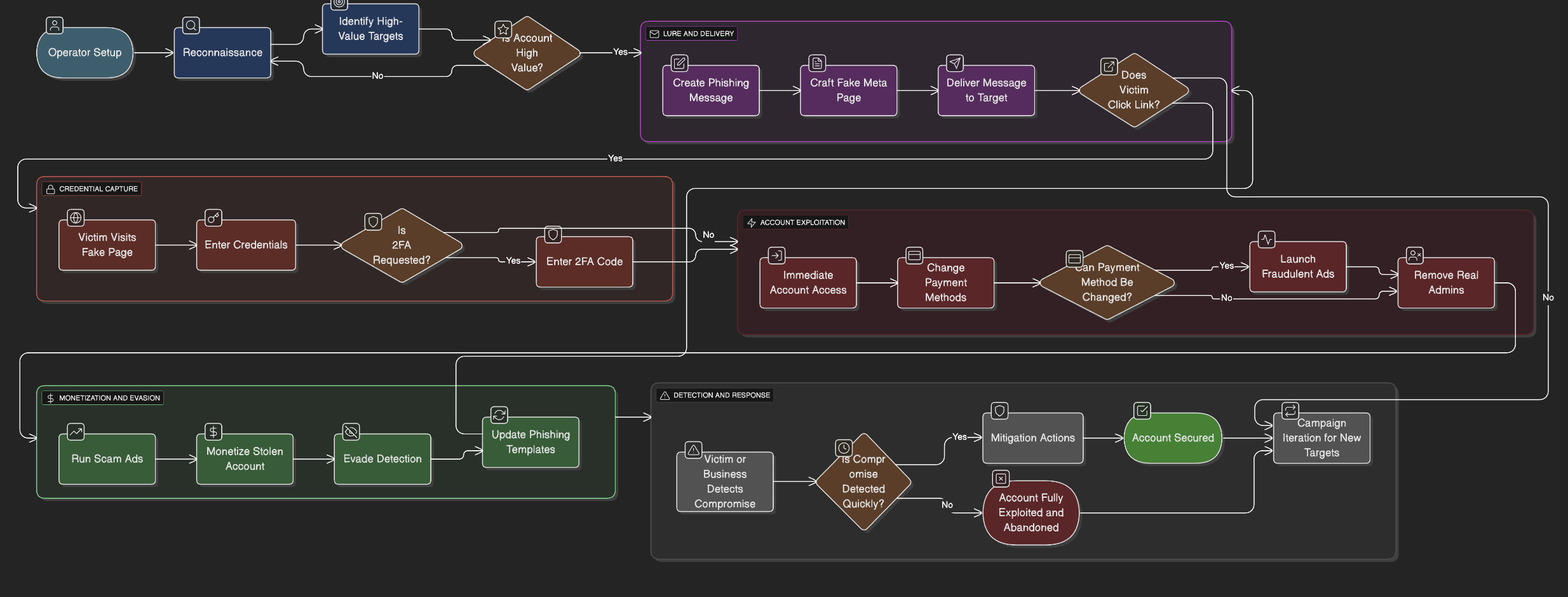
Warning Signs
- Urgent messages about “24-hour suspension” or “policy removal.”
- Meta-style designs with small grammar errors (“We have suspend your page”).
- Links to fake “Help Center” pages asking for login or 2FA.
- Rapid ad or billing changes right after a new login.