In our previous paper, Investment Scam Playbook: From Job Recruitment to Investment Scam, we detailed the scammer’s methods for luring victims into fraudulent schemes. This blog expands on that work.
By documenting the scam’s step-by-step process, this analysis aims to uncover the techniques employed by scammers, empowering individuals and organizations to identify, counteract, and report such malicious activities. Through this effort, we hope to foster greater awareness and resilience against evolving financial fraud tactics.
Infrastructure
Investment Website: totallysoftware[.]tech
The domain TotallySoftware[.]tech was registered recently on 2024-08-12 through NameSilo LLC and is hosted using Cloudflare services. At first glance, the website appears legitimate, positioning itself as a provider of ‘app store boost services’ for startups and mid-sized applications. However, registration on the platform requires a specific code exclusively by the scammer through WhatsApp. This selective entry method is strategically designed to shield the operation from scrutiny by security researchers and to obscure their fraudulent activities from being detected or analyzed. The following screenshots shows the webpage once you log in.
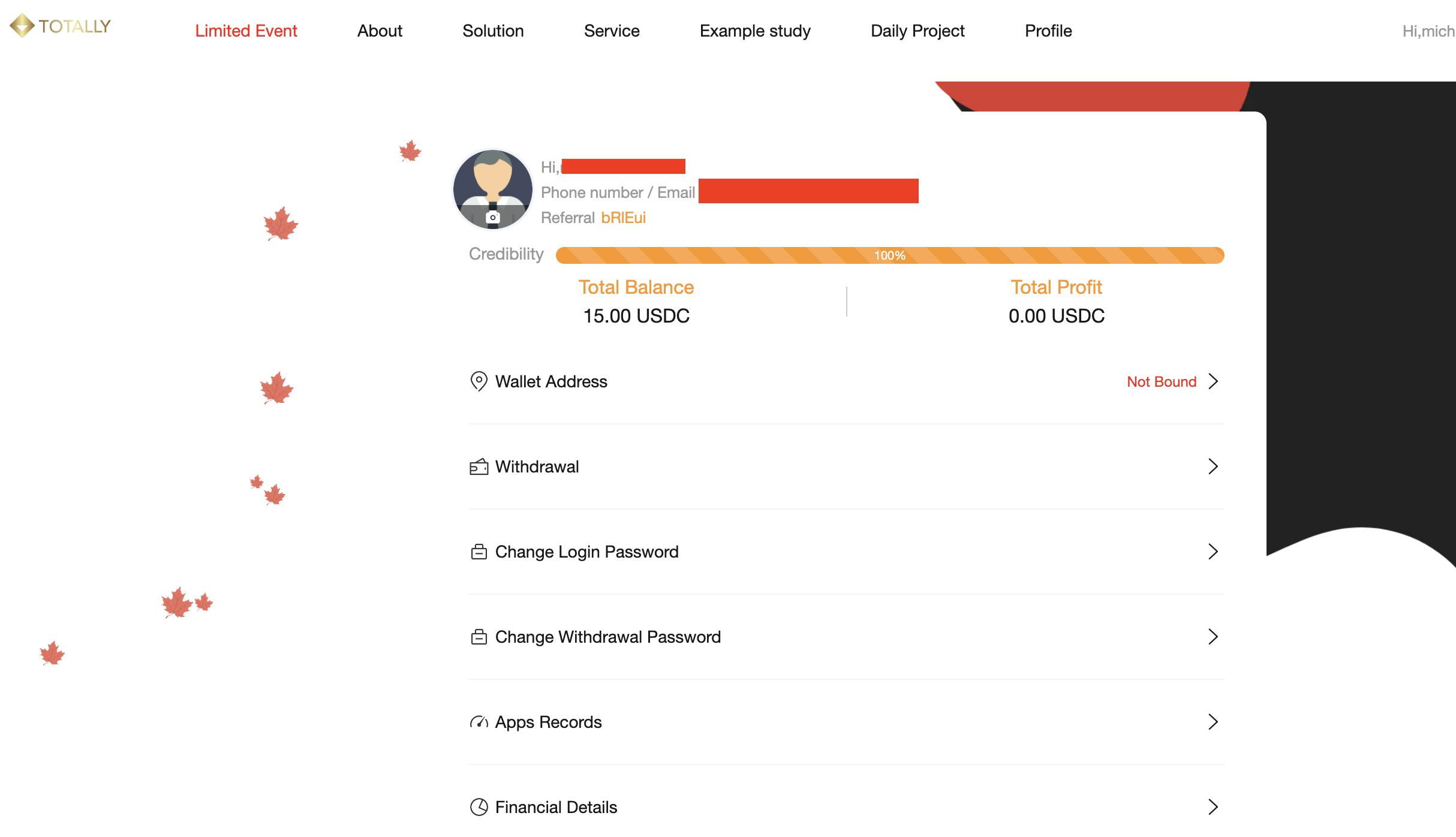
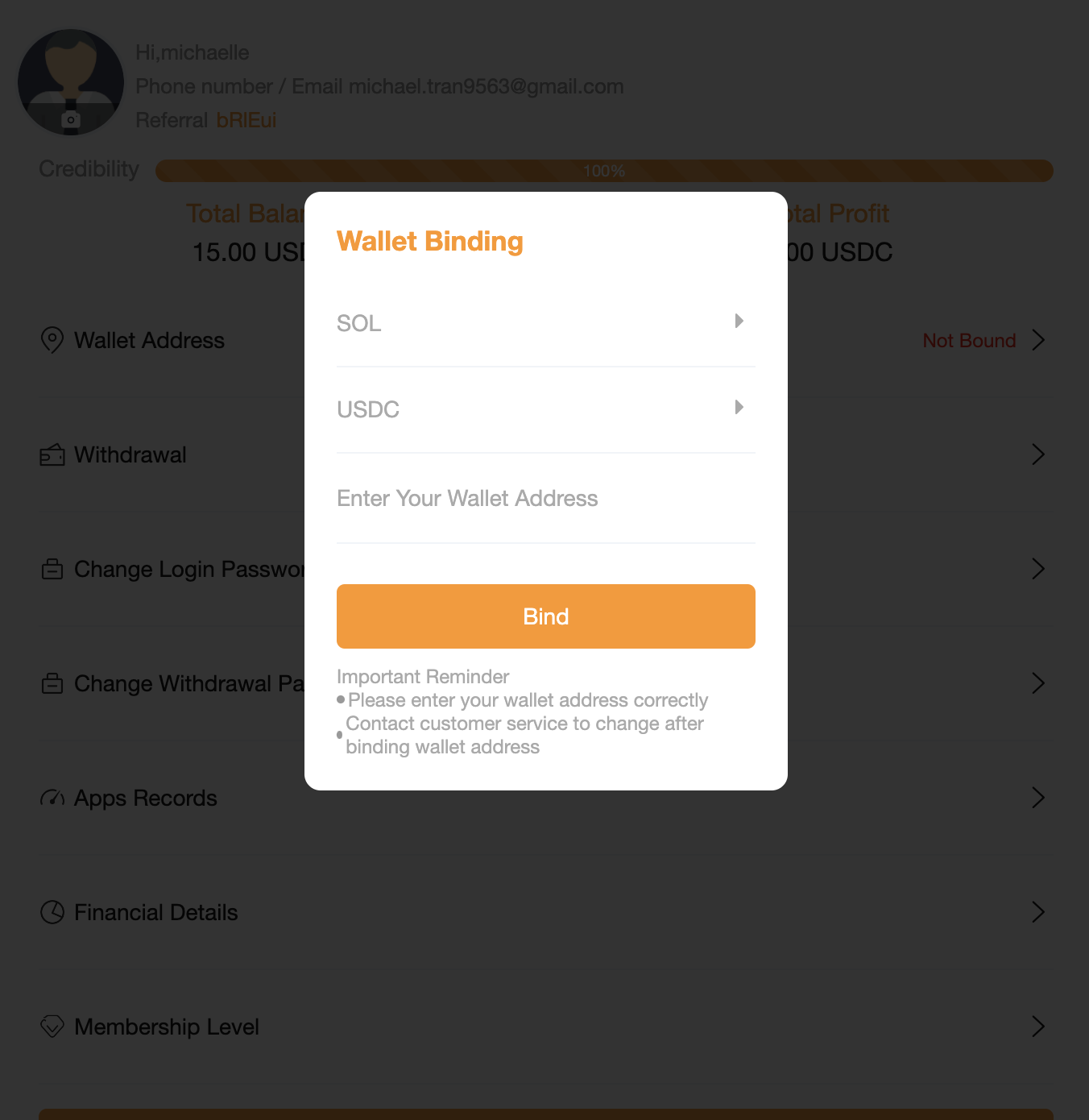
Administration/Scammer Front End
From the backend, the scammer accesses a private dashboard to manage victims’ accounts. The following screenshot illustrates the login page for this dashboard, highlighting the infrastructure supporting the scam’s operations.

Domains
Upon reviewing the domain totallysoftware[.]tech, we identified additional domains sharing similar themes and structures indicative of investment scams. Below is a list of these associated domains, which exhibit characteristics of fraudulent activity, including deceptive registration practices and thematic alignment with known scam infrastructures.

Hosting
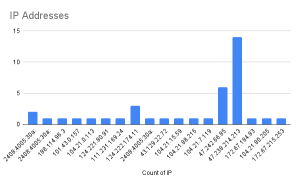
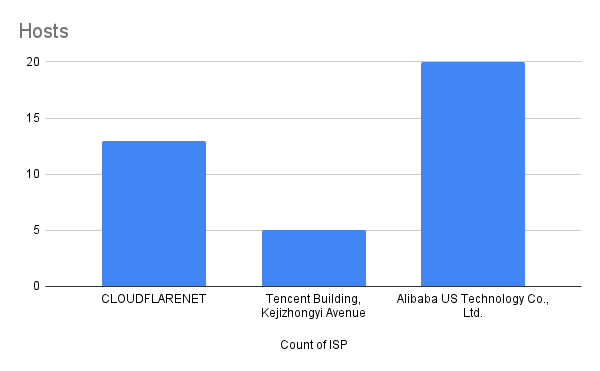
The domains are hosted across various infrastructure providers, including Alibaba Cloud and Tencent Cloud, with some utilizing Cloudflare as a proxy to obscure their true hosting locations. Below is a breakdown of the associated domains and their respective IP addresses, illustrating the diverse hosting environments leveraged to facilitate their fraudulent activities.
IOCs
Domains
totallysoftware[.]tech
totally-app[.]tech
cexsapp[.]bond
gipfelmarketing[.]com
greenlanemarketing[.]bond
greenlanemarketing[.]cc
nptn-app[.]com
nptn[.]app
nptnappp[.]com
oneumbrella[.]app
speednetapp[.]com
tecocraft-app[.]cc
tecocraft-app[.]com
speednetsoftwares[.]bond
cexsapp[.]cyou
cexsapp[.]shop
evamobicc-vip[.]com
evamobi-pro[.]com
evamobicc[.]com
evamobi-xzy[.]com
evamobi-dond[.]com
evamobi-vip[.]com
devlightxio[.]com/
wyertlsdjcalwmf[.]com/
masjiorvklmawl[.]com/
mcasiohgoc[.]com/
diksmfndctqa[.]com/
devlightwmaw[.]com/
wejaskzl[.]com/
evamobilscc[.]com/
badkvmisdo[.]com/
devlightmwju[.]com/
pdsfmwemkahdtop[.]com/
devlighthsow[.]com/
devlight-xyz[.]com/
commercecentriczi[.]com/
devlight-cyou[.]com/
devlight-pink[.]com/
devlight-io[.]com/
commercecentricpink[.]com/
devlight-shop[.]com/
devlight-cc[.]com/
appmonstacn[.]com/
evamobicc-vip[.]com/
appmonsta-org[.]com/
evamobi-pro[.]com/
thegamemarketer-shop[.]com/
evamobicc[.]com/
evamobi-xzy[.]com/
evamobi-dond[.]com/
thegamemarketer-bond[.]com/
thegamemarketer-net[.]com/
evamobi-vip[.]com/
evamobi-site[.]com/
devlight-vip[.]com/
devlightxio[.]com
wyertlsdjcalwmf[.]com
masjiorvklmawl[.]com
mcasiohgoc[.]com
diksmfndctqa[.]com
devlightwmaw[.]com
wejaskzl[.]com
evamobilscc[.]com
badkvmisdo[.]com
devlightmwju[.]com
devlighthsow[.]com
devlight-xyz[.]com
devlight-cyou[.]com
devlight-pink[.]com
devlight-io[.]com
devlight-shop[.]com
devlight-cc[.]com
IP Addresses
2408:4005:30a:4302:6218:d8d9:db29:5de0
2408:4005:30a:4302:6218:d8d9:db29:5dd6
188.114.96[.3
101.43.0[.157
104.21.0[.113
124.221.80[.91
111.231.169[.247
124.222.174.[117
2408:4005:30a:4302:6218:d8d9:db29:5dd2
43.129.22[.72
104.21.15[.59
104.21.88[.215
104.21.7[.119
47.242.66[.85
47.238.214[.213
172.67.184[.83
104.21.80[.205
172.67.215[.253
47.238.214[.213