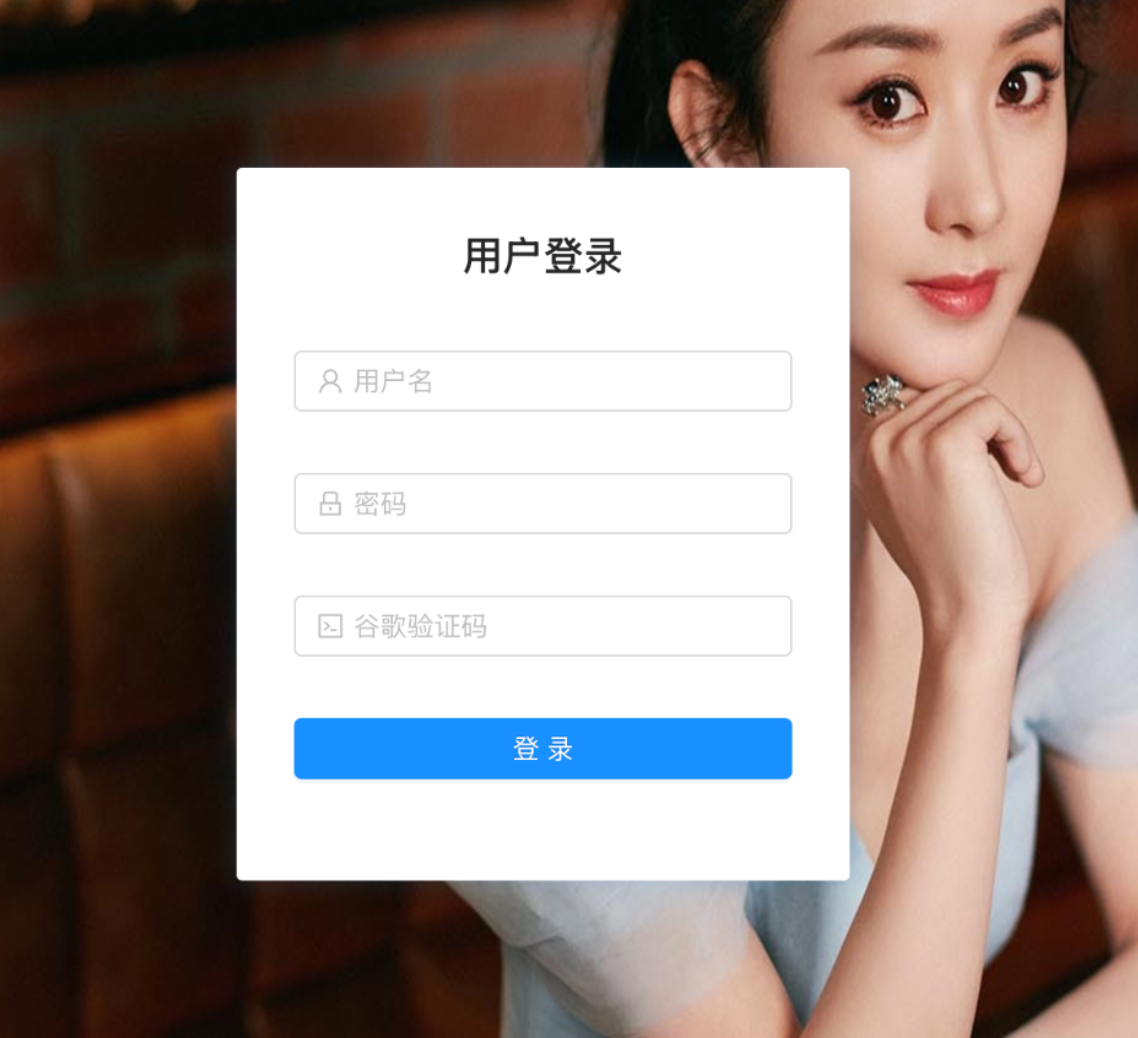
The campaign exploited Meta’s terms of service, claiming that the targeted business accounts were flagged for deletion due to violations. Victims were prompted to submit their credentials and provide an explanation to keep their business pages active. This highlights the increasing sophistication and danger of targeted phishing campaigns against users of major platforms.
The Campaign’s Tactics
The attackers utilized a well-coordinated strategy to lure Meta business owners into providing their sensitive data:
- Phishing Pages: Over 400 fake websites mimicked Meta’s Business Manager. These pages featured professional designs to appear authentic.
- Social Engineering: The attackers exploited fear and urgency, encouraging victims to send their credentials and reasons for the false claim.
Figures 1 and 2 illustrate the phishing pages and their deceptive lures.

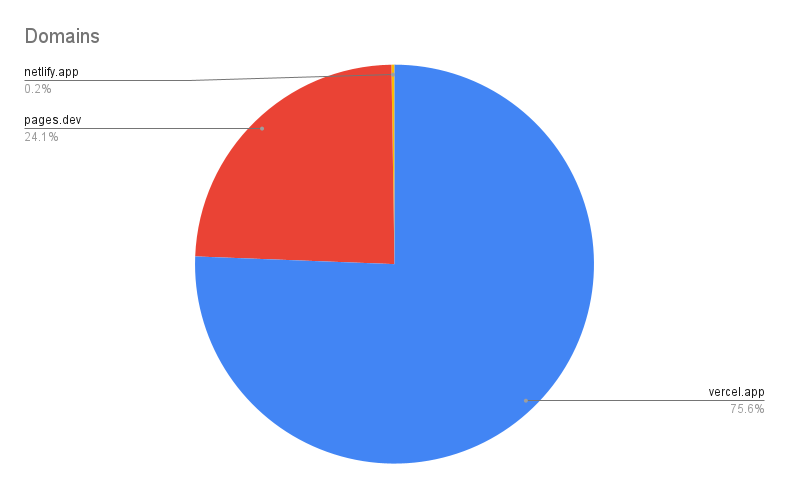
Infrastructure
The phishers utilized various web hosting platforms to deploy their phishing sites. Figure 3 presents a chart detailing the infrastructure employed by the attackers.
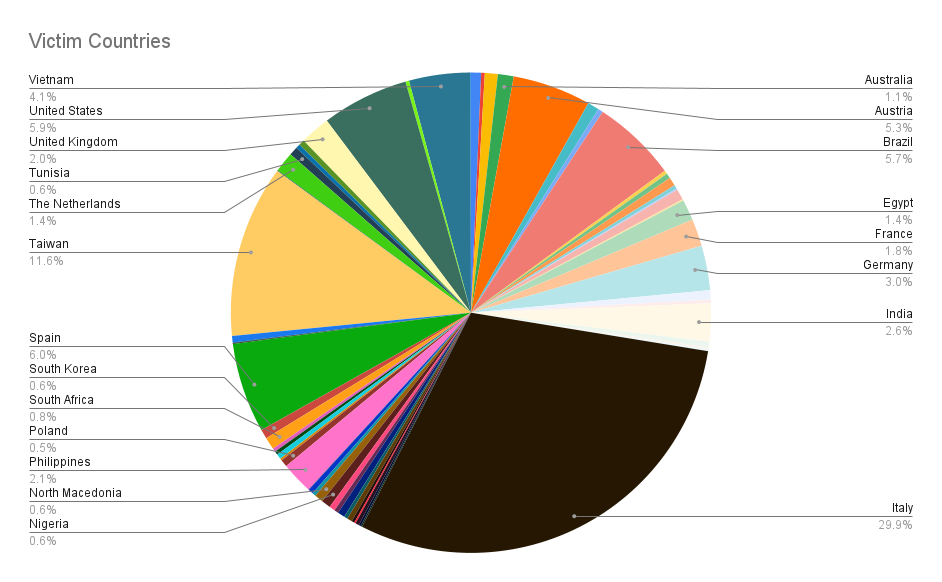
Phish Victims
We observed over 600 victims affected by these campaigns. The cybercriminals targeted businesses worldwide. Figure 4 provides an overview of the victims categorized by country.
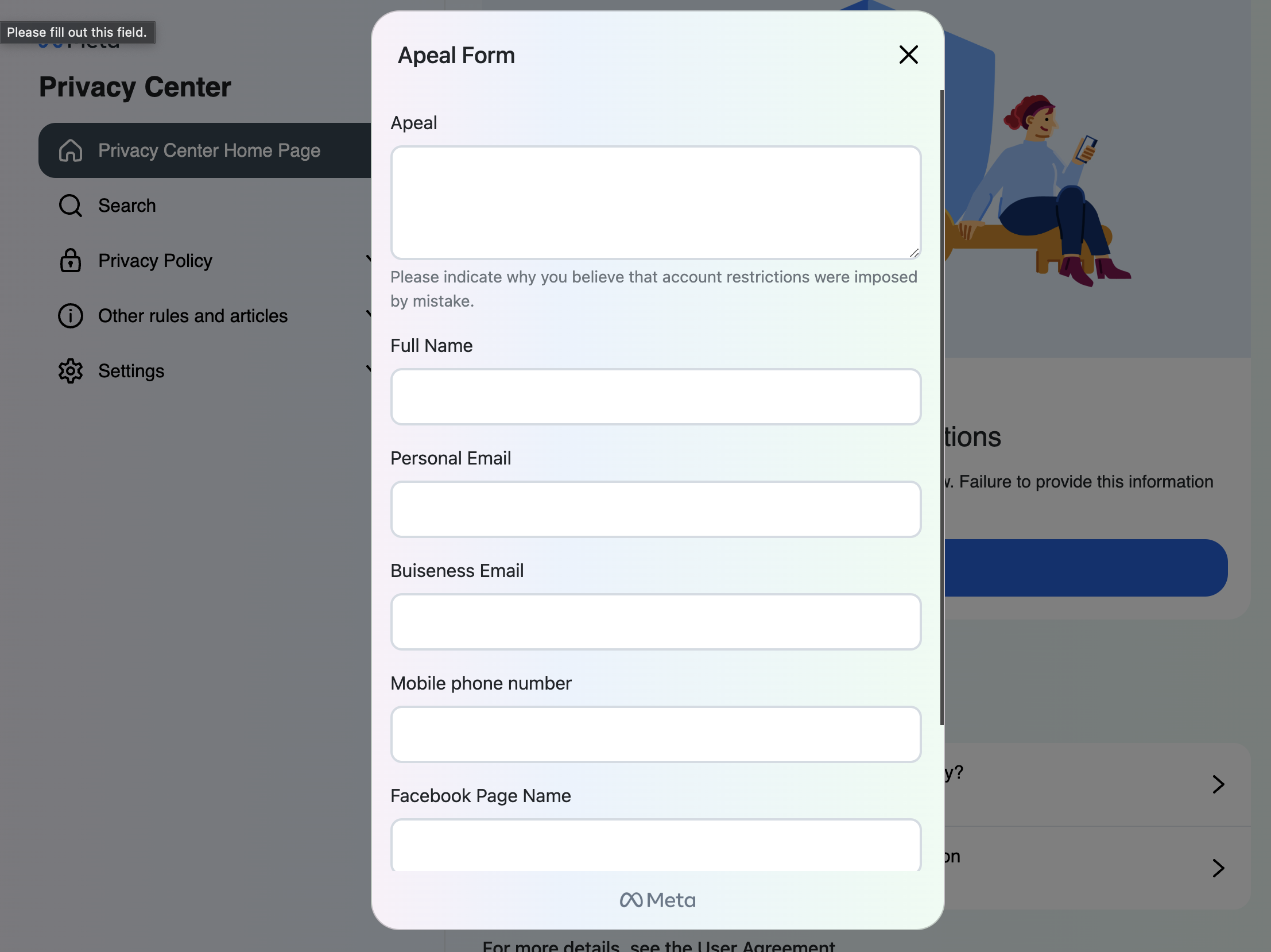
Potential Phish Owner
Our analysis of the phishing sites revealed that the captured data is transmitted to a Telegram channel managed by two users, @Tigerok3001 and @vlxx12312. Figure 5 illustrates the communication points utilized by the phishing operations.

During our observation of the phishing activities, we discovered that the attackers initially deployed and tested their phishing kit at
http://103.186.67[.]50/intest.html
Analysis of the traffic revealed that one victim submitted the name “Nguyễn Đình Quyết” along with the email address quyetnd288@gmail.com. This name and email address were repeatedly used across multiple test phishing infrastructures, suggesting their involvement in the campaign’s early stages.
Indicators of Compromise
Below are the indicators of compromise (IOCs) we have identified so far:
https://github.com/cyberarmortech/iocs/blob/main/quyetnd288.txt