How Threat Actors Access and Use the Infrastructure
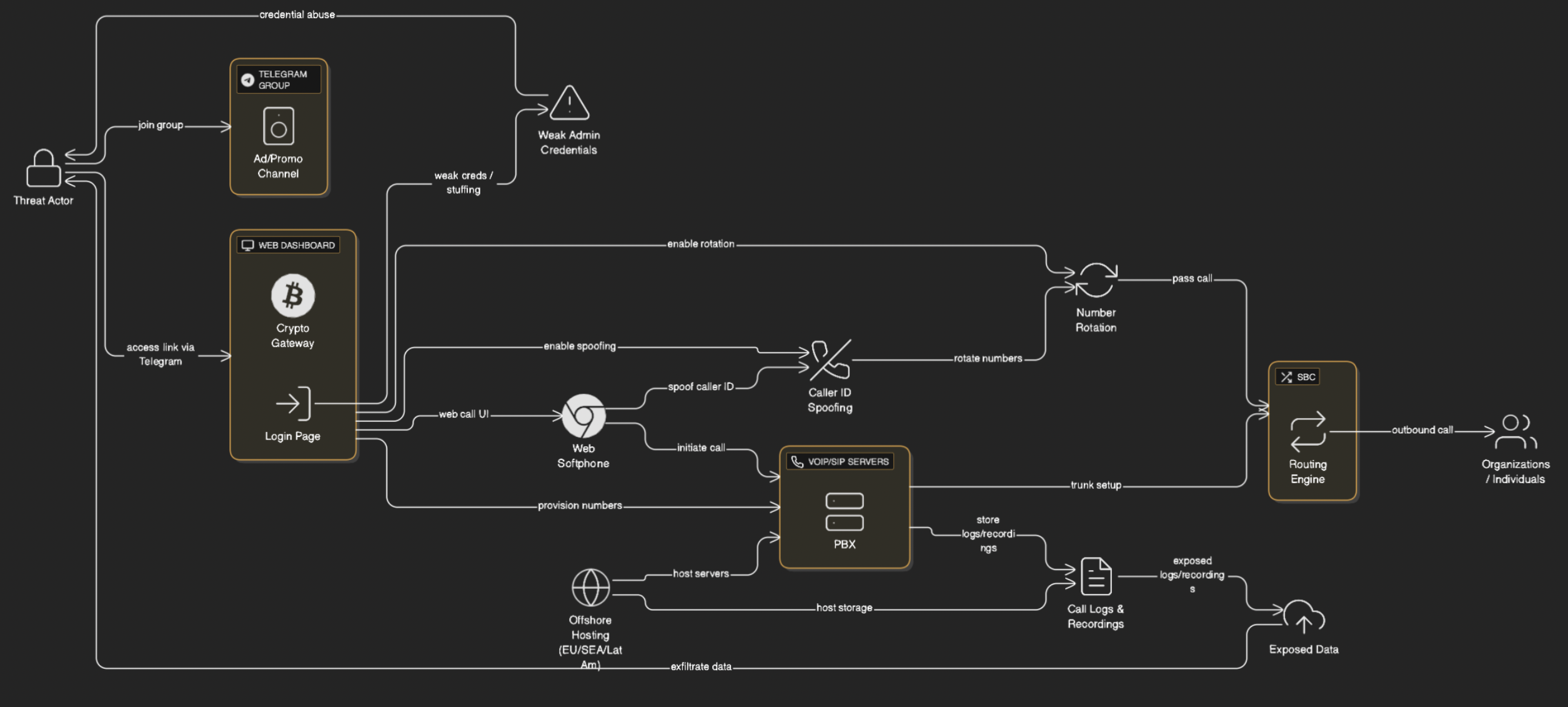
Access is sold directly through encrypted messaging platforms. After joining a private Telegram group, users receive a link to a self-service web dashboard. Once a crypto payment (typically $100–$300 in Bitcoin or USDT) is confirmed, buyers can immediately purchase virtual phone numbers from multiple regions, configure spoofed caller IDs, and begin making calls via an in-browser softphone.
For example, after seeing an ad promoting “anonymous global calling for call centers,” someone could pay a small amount in crypto, log into the dashboard, and start international number spoofing within minutes. The dashboard includes call analytics, automated number purchases, and a “rotation mode” that switches numbers every few seconds to evade telecom filtering and fraud detection systems.
Geographic Reach and Potential Threats
The underlying system likely consists of interconnected VoIP/SIP servers, PBX systems, session border controllers, and crypto payment gateways. Traffic is routed through servers in Europe, Southeast Asia, and Latin America, leveraging offshore hosting and anonymized registration data to obscure ownership.
Such infrastructure can facilitate:
- Vishing campaigns targeting individuals and organizations
- Spam and scam call operations
- Telecom bypass attacks
Risks to Organizations and Users
While this infrastructure primarily serves cybercriminals, legitimate organizations may still be indirectly exposed:
- Leakage of call metadata or recordings: Poorly secured servers or dashboards may expose IP addresses, call logs, and recordings. Exposed backups could reveal numbers called, timestamps, and audio of social-engineering calls.
- Credential compromise: Weak dashboard authentication can allow attackers to change routing rules, enable spoofed numbers, or access historical call data.
- Social engineering enablement: Cybercriminals can impersonate businesses, spoofing bank lines or IT support to extract sensitive information.
- Regulatory and legal repercussions: Organizations failing to detect attacks may face compliance violations (HIPAA, GDPR), fines, or regulatory investigations.
Real-World Example
The user sees an ad for “anonymous global calling” and pays ~$150 in crypto.

The user is then able to log into the dashboard and buy an international number with caller ID spoofing enabled.

They can call customers while impersonating a bank’s fraud team. Rotation mode swaps numbers to evade detection. Poorly secured dashboards could expose call logs and recordings.
Potential impact cannot be underestimated and includes customer data loss, financial fraud, and regulatory scrutiny.
Immediate Recommendations
Organizations are advised to:
Audit VoIP and SIP configurations for anomalies (spikes in outbound traffic, unexpected international routes, unknown trunk endpoints).
Enforce strong authentication and credential hygiene for telephony dashboards.
Monitor call traffic for unusual patterns: repeated short international calls, rotating caller IDs, or high-risk region targets.
Educate staff about vishing and impersonation; run tabletop exercises simulating spoofed calls.
Report suspicious VoIP services to authorities such as CISA, FTC, local telecom regulators, and CERTs to support takedowns.
Conclusion
TG-VoIP-001 highlights how adversaries continue to exploit global telecommunications and set up their own VoIP/SIP infrastructure for financial gain and deception. The growing sophistication of VoIP-based fraud emphasizes the need for continuous monitoring, cross-sector intelligence sharing, and collaborative mitigation to reduce exposure to these emerging threats. Proactive monitoring can make a critical difference - early detection of anomalous call patterns or spoofed numbers can stop attacks before they escalate into large-scale vishing campaigns or data breaches.





